TLDR: Scan GitLab job logs for credentials using https://github.com/CompassSecurity/pipeleak Many organizations use (self-hosted) GitLab instances to manage their source code and a lot of infrastructure is managed in code (IaC), thus these configurations must be source-controlled as well, putting a lot of responsibility on the source code platform in use. Often deployments are automated using CI/CD […]
Compass Security Blog
Offensive Defense
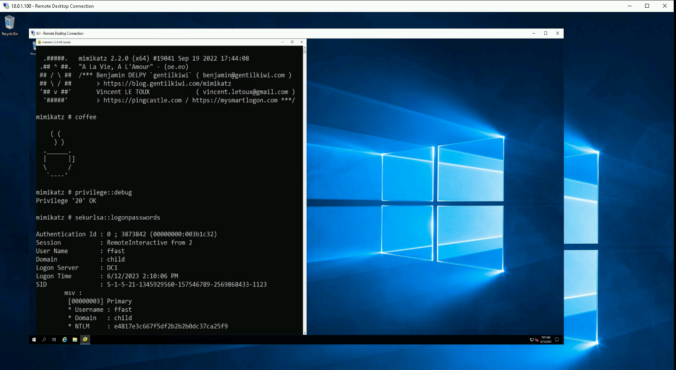
When accessing a remote server, one should always assume it has been compromised or might be in the near future. It is particularly crucial for users with administrative privileges to establish a secure connection to the Remote Desktop Protocol (RDP) service in order to not fall victim to credential theft or impersonation. To achieve this, there exist several measures in Windows. In this blog post, we’ll look at some of them, their benefits and their drawbacks.
Sometimes, the good old credential dumping techniques just won’t work. This is the story of how a bad actor could dump credentials on a fully-patched, monitored and hardened workstation.
© 2026 Compass Security Blog