The ntds.dit file from a domain controller contains all password hashes of the domain. In a company with employees around the globe we were allowed to analyze the hashes. Here are the results, and the reason why you should implement a banned password list.
Compass Security Blog
Offensive Defense
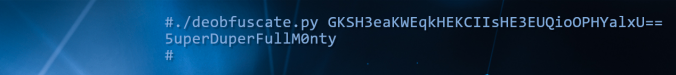
During internal penetration tests or Windows client hardening engagements, we often find configuration files with obfuscated passwords. The post demonstrates a general approach and required tools to effectively make use of such credentials.
Fridays, I was approaching a win32 reversing challenge. So I transferred the binary into my Windows XP virtual box and fired-up OllyDbg. The goal was to bypass the username and password prompt that occurred on application startup. Hilariously, I was just providing a dummy name and password to the app…. “asdf” “asdf” as probably most […]
© 2025 Compass Security Blog