Today I’m happy to release the following security advisories:
- SQL injection in Leed (CSNC-2013-005 / CVE-2013-2627)
- Cross-site request forgery in Leed (CSNC-2013-006 / CVE-2013-2628
- Authentication bypass in Leed (CSNC-2013-007 / CVE-2013-2629)
- URL redirection in Secure Entry Server (SES)
I would take the opportunity to thanks Valentin CARRUESCO aka Idleman for the timely patches he implemented within Leed.
Of further interest is the vulnerability which affected the SES as it was due to a common mistake made when validating URLs. Let’s illustrate the issue with another occurrence of the same flaw, which affected LinkedIn and was reported back in November 2012.
Back then, attempts to visit a page reserved to LinkedIn members only triggered a redirect to the following login page:
https://www.linkedin.com/uas/login?session_redirect=%2F[original_page]
Variable session_redirect was used to keep track of the initially desired page. Once successfully logged in, the web application would redirect us straight to this page using the following AJAX response:
{"status":"ok","redirectUrl":"/[original_page]"}
Attempts to misuse this mechanism and inject a full URL in parameter session_redirect (e.g. session_redirect=https:%2F%2Fwww.csnc.ch) would fail, presumably because the developers ensured that the first character of value session_redirect had to be a slash (or its URL-encoded hex value %2F).
But what about partial URL //www.csnc.ch? Based on the aforementioned logic, such an URL would be considered as safe by the code, as it starts with a slash. But modern browsers don’t interpret a redirection to //www.csnc.ch as being http(s)://[victim]//www.csnc.ch, but in fact as a redirection to http(s)://www.csnc.ch. This behaviour is RFC conform and commonly used over the Internet to embed resources regardless of the URL scheme (http if the initial page was called over http, https if called over https).
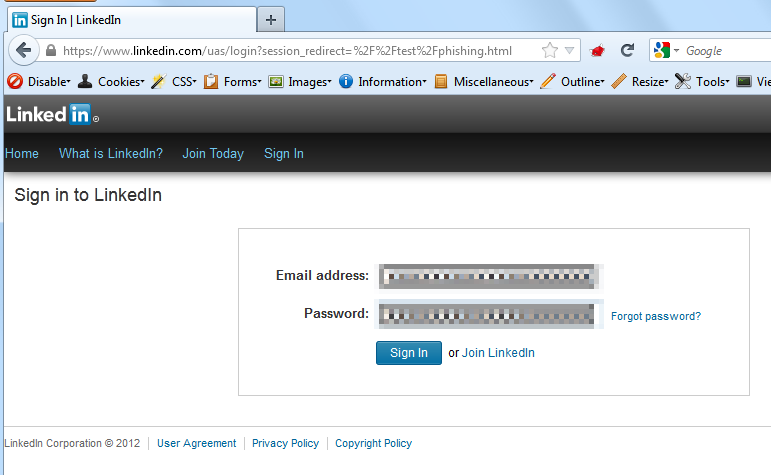
Was it possible to abuse LinkedIn and the SES with such a trick? Yes, here’s an illustration of it:
Attempt to login on LinkedIn using forged URL (note the double slash – %2F%2F) https://www.linkedin.com/uas/login?session_redirect=%2F%2Ftest%2Fphishing.html
Pressing button “Sign In” would submit the entered credentials. An extract of the AJAX response is shown below:
HTTP/1.1 200 OK
Server: Apache-Coyote/1.1
[removed various Set-Cookies directives]
X-LI-UUID: B[base64_stuff]nsg==
[removed various Set-Cookies directives]
Pragma: no-cache
Expires: Thu, 01 Jan 1970 00:00:00 GMT
Cache-Control: no-cache
Cache-Control: no-store
Vary: Accept-Encoding
Content-Type: application/json;charset=UTF-8
Content-Language: en-US
Date: Sat, 10 Nov 2012 11:45:45 GMT
Age: 1
Connection: keep-alive
Content-Length: 52
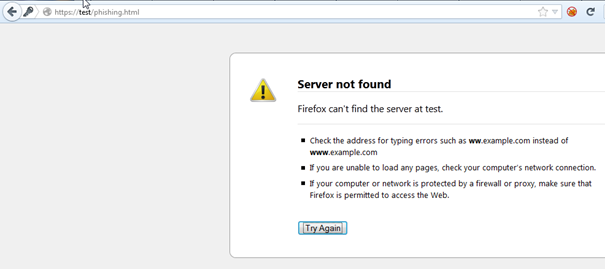
{"status":"ok","redirectUrl":"//test/phishing.html"}
The browser would then interpret this redirection as being meant for [scheme]://test/phishing.html and perform the according request as seen below:
GET /phishing.html HTTP/1.1 Host: test User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:16.0) Gecko/20100101 Firefox/16.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: keep-alive Referer: https://www.linkedin.com/uas/login?session_redirect=%2F%2Ftest%2Fphishing.html
The issue was reported to LinkedIn in November 2012 and fixed without further acknowledgement.
As a conclusion, do not assume that a partial URL value starting with a slash will always represent a path on your website. It may as well be a valid URL representation pointing to another domain. Furthermore, always perform redirections using a full qualified domain name and don’t just rely on a partial URL representation.
Leave a Reply