Did Roger Federer call us for some IT-security advice or did Nicolas Heiniger and I find a new way to spoof a caller id?
The Human Factor is, and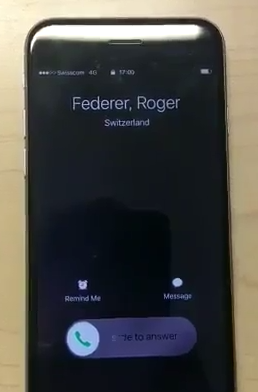 remains, the biggest and most relevant threat to the security of every company. The latest statistics state that “only about 3% of the malware they run into tries to exploit a technical flaw. The other 97% is trying to trick a user through some type of social engineering scheme” [1].
remains, the biggest and most relevant threat to the security of every company. The latest statistics state that “only about 3% of the malware they run into tries to exploit a technical flaw. The other 97% is trying to trick a user through some type of social engineering scheme” [1].
One of the attack vectors on the rise, used by criminals for highly targeted scams, is known as vishing. Vishing is nothing more than voice elicitation through a phone call. It is the telephone equivalent of phishing. This type of attack largely relies on the victim’s tendency to place trust in the sanctity of a landline versus other communication platforms such as email. It is a fairly simple attack, from a technical point of view. The basic ingredients for a successful vishing call are: a good pretext and a spoofed caller id. Spoofing a caller id allows an attacker to choose his own phone number, and thus appearing as a trustworthy person to the victim. This trustworthiness will be increased if the phone displays a known name on the incoming call.
Assuming that the attacker already has a good pretext, let’s focus only on the technical part.
Caller id spoofing can be done in different ways, for example by using an Asterisk setup or by subscribing to an online service that will do it for you.
Limitation of the caller id spoofing attack
The main problems about caller id spoofing is not “spoofing the number”, but actually :
- finding the phone number of the person that the attacker wants to impersonate
- hoping that the victim, which will receive the spoofed call, has stored the phone number of the impersonated person (associated a phone number, which will be faked, with a name)
Those who performed some OSINT research know how difficult it can be to find the private phone number of a VIP, a CEO or a very privacy aware person. It is even more difficult to be sure that your target will have the number of the VIP stored on his phone. We discovered a new way to bypass all those limitations, thanks to a functionality provided by Swisscom [2].
The new attack – How to bypass the limitation
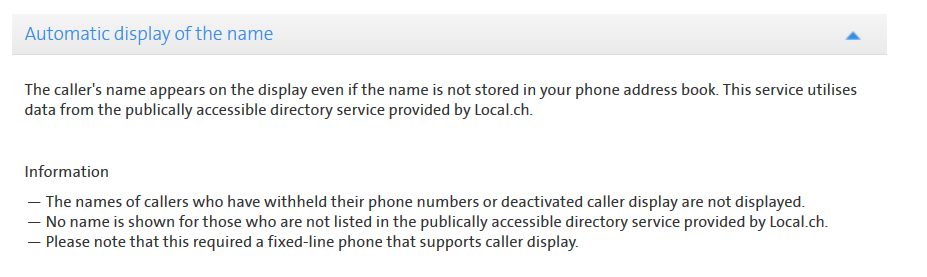
In the last months I noticed, when receiving a call on my mobile phone from a customer, that many times the name of the company appeared on the display even if that name was not stored in my phone book. We found out that this new service uses data from the publicly accessible directory service provided by local.ch:
This means that spoofing the caller id (telephone number) of someone listed on local.ch automatically will display its name on the victim’s phone.
Does an attacker want to impersonate a famous politician, VIP or CEO? He only needs to find someone on local.ch who has the same name and to spoof his number. What if the attacker does not find someone that has the same name on local.ch? We didn’t try this yet, but we assume that it should not be too difficult to create a new entry on local.ch with an arbitrary name.
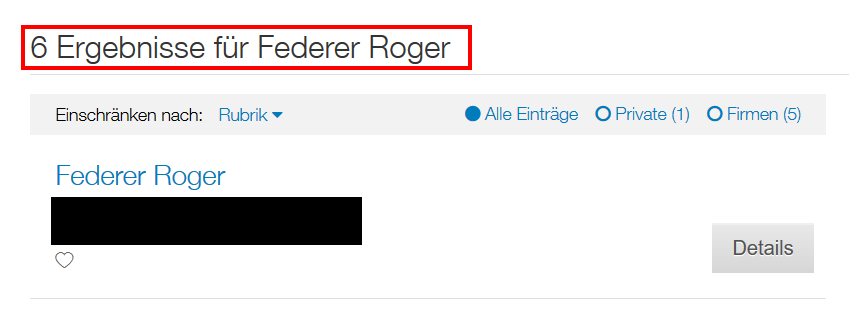
Let’s take an example and have a famous person call us. We first have to search for him on local.ch:
Using this phone number we can spoof our caller id to this number. And the result, when calling the victim’s phone, is as follows:
This simple trick bypasses most of the limitations of the actual spoofed caller id attack and allows the execution of new social engineering scenarios against the victim.
The attacker now:
- doesn’t have to find the real number of the person that he want to impersonate
- doesn’t have to hope that the victim has stored the contact of the impersonated person
He can dedicate his time to find an even better pretext.
This attack and many more will be discussed and analyzed during our brand new Social Engineering course in November 2017 in Zürich.
Note:
Further research should be done to determine which phone models, OS versions and phone carriers support this feature. Up to now we’ve proven it work on every iPhone we tested and on some Android phones as well.
References:
- https://digitalguardian.com/blog/social-engineering-attacks-common-techniques-how-prevent-attack
- https://www.swisscom.ch/en/residential/help/fixed-network/suppressing-your-telephone-number-service-31.html
Leave a Reply