Sometimes, it doesn’t take much for a good scam: a good story, a little persuasion, then disappear again… and sometimes, the scammers come up with tactics that come straight out of the textbook.

In August 2019, Compass Security’s Digital Forensics and Incident Response Team received a request from an investment company that appeared to have been the victim of invoice fraud. An invoice amount in the 6-digits range was sent to an unknown bank account.
Invoice fraud involves an attacker posing as a customer or business partner and trying to get the victim to wire as much money as possible to the attacker’s bank account.
At the time of the request, the company’s IT manager had already taken the first immediate measures and according to them the attackers seemed to have already been expelled. In addition to providing full access to the implicated systems, we were also provided with a rough sequence of the incident. Now, we could start work and fill the gaps in the timeline of events.
In a forensic analysis, it is often difficult to determine the exact starting point of an attack. One starts at a known point in time (e.g. detection of suspicious activity) and works backwards to the time of the intrusion.
In the Beginning Was the Phishing
On a Monday morning in July 2019, the CEO of the investment company received a phishing e-mail. The sender appeared to be a business partner of the company and the content was a link to a shared business-related document. It was possible to recognize it as phishing by our specialists, as it was a mix of Microsoft SharePoint and Citrix ShareFile, which are similar products, but from different manufacturers. However, with so many providers and different logos, this is barely noticeable to the untrained eye. It is also suspicious that the recipient is “Undisclosed recipients”. Something that happens when you want to hide the recipients from each other, and to prevent the recipients from using “Reply All”.
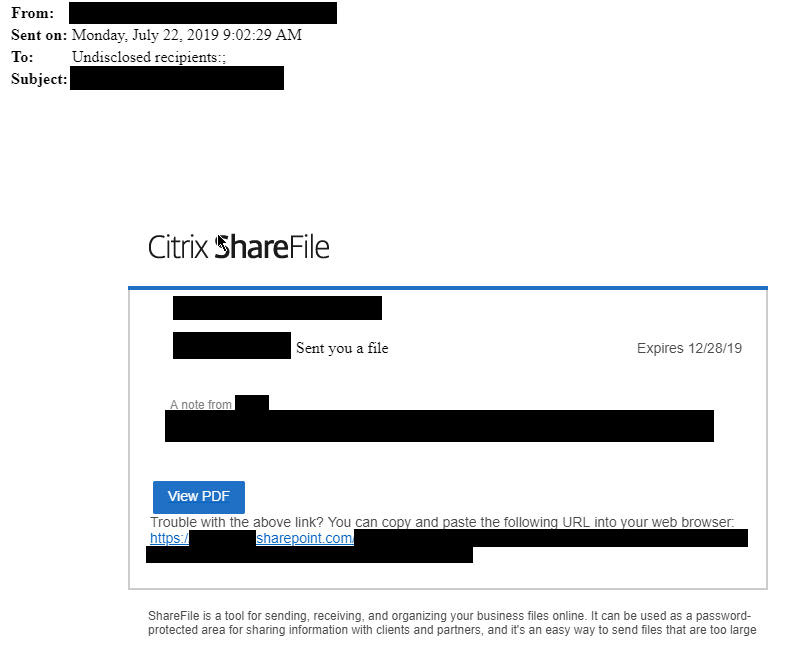
In a moment of inattention, the CEO of the company opened the e-mail and entered his Office 365 credentials in the authentication prompt. Muscle memory. This was his last chance to become aware of the phishing, since the address line of the browser for this page showed a wrong address. It is remarkable that Microsoft SharePoint itself was used as a forwarder to this phishing page, so that a simple automatic detection (e.g. against a known blacklist) would’ve probably been impossible.
50 Minutes Later…
Only 50 minutes after the successful phishing, the attackers logged on for the first time with the stolen credentials. The attackers proceeded systematically and tried to gain the greatest possible profit from each phase of their operation. At first, they downloaded all contacts in order to have a valuable list of new potential victims in case of early detection and lock-out.
However, the intrusion was not noticed and they now began to search the CEO’s e-mails for useful information. Coincidentally, on the same day, a large payment has already been made to an investee. The attackers manipulated a PDF with payment instructions, deleted the conversation and sent the CEO a new e-mail with the manipulated payment instructions and asked to amend the payment. To make this look legitimate, the attackers attached the original history of the e-mail, adapted the writing style to the original sender and even registered a similar e-mail address on Gmail.
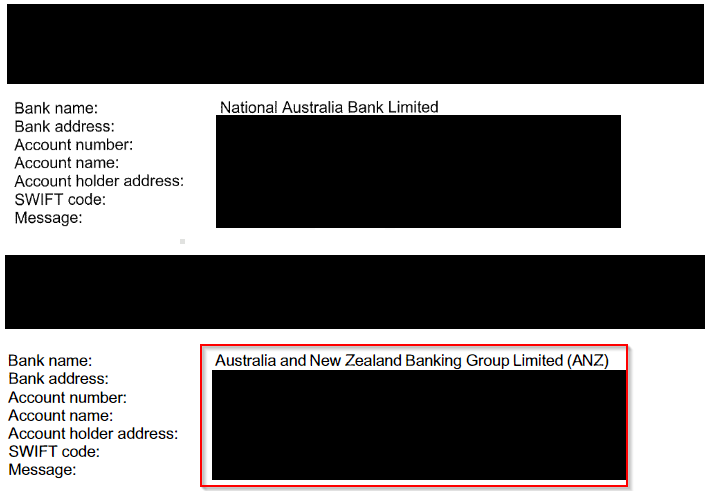
The fake e-mail from the attackers fitted in perfectly and even the bank was chosen appropriately: The National Australia Bank, where the money should have been sent, became the Australian and New Zealand Banking Group. After only an hour, the payment order was “corrected” by the investment company. Surprisingly, an employee noticed an error the following day, which was also in the original payment instructions, but the attackers just played their role and held a professional conversation over several e-mails to correct the error to the satisfaction of the investment company.
Two for the Price of One
Tuesday. While the attackers were waiting for their money, a second valuable opportunity unexpectedly came their way: Another investee sent the CEO their bank information. Only 15 minutes pass and the attackers have already reacted and created an inbox rule to automatically move the e-mails of this investee from the inbox to a separate folder so the CEO never sees them.
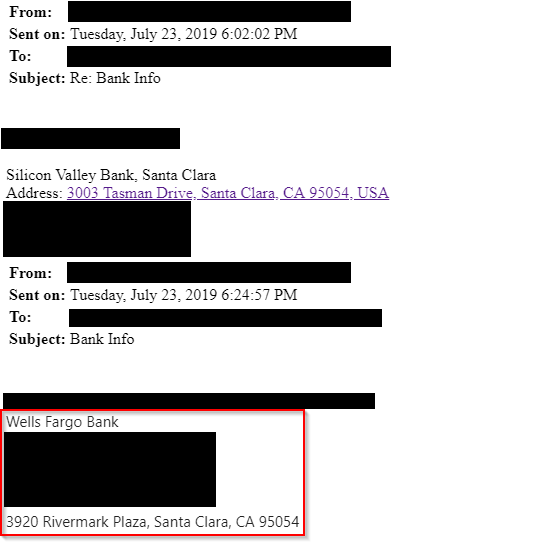
Only 10 minutes later, the attackers have bought a domain that looks confusingly similar to the sender’s domain. The same game starts all over again and the attackers have replaced the investee’s bank information with their own. Again, it is astonishing that the attackers had a matching and similar bank at hand again, which also has a branch in Santa Clara like the original bank.
After Me, the Deluge
Wednesday. The real investee from the first payment became impatient and asked both the CEO and an employee of the company about the payment. The attackers were faster and could delete the e-mail within 2 minutes from the CEO’s inbox and then also created an inbox rule for this investee. However, they had no access to the employee’s e-mails. So they used a simple trick: They sent the exact same e-mail from their phishing address, so that it appears further up in the employee’s inbox because it is newer. Then, to reassure the employee, they sent a message a few minutes later that they had called the bank and the payment was on its way. So there was no need for him to act.
Inbox rules are automatically applied when a new e-mail arrives. For example, you can move an e-mail to a folder, or even forward it, based on its sender.
In the meantime there was a small but lucky mistake internally: One employee was not taken into CC of a conversation and sent the second investee an e-mail with a question that had already been answered. But they asked the real one and not the attackers. The investee immediately recognized that something was wrong with the e-mail and called the company by phone. The employees immediately realized that this was some sort of attack and informed the other employees and the CEO by e-mail that the payment had been manipulated and it had to be stopped immediately.
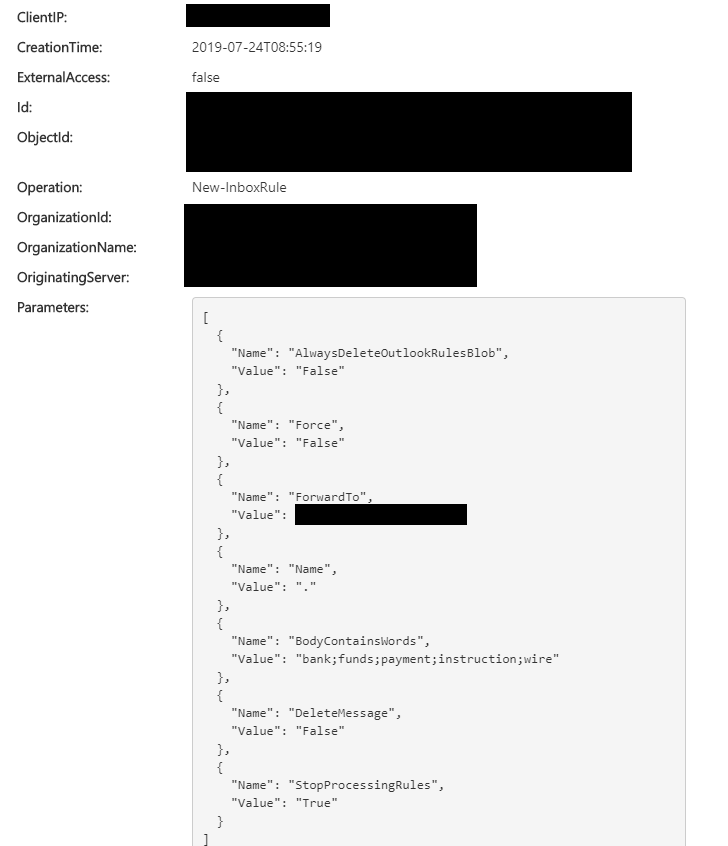
As of then, the attackers knew that they were blown and we could observe an interesting and striking change in their strategy. Now it was only a matter of time until the weak spot was found and they were locked out with a password change. So they took a last and risky step: They created another inbox rule and forwarded all e-mails with certain keywords (e.g. bank, funds, payment) to their own external e-mail address and not to another folder in the same account as they previously did. At this point at the latest, it was easy to detect the exfiltration and we later found an alarm in Office 365 for this very same inbox rule.
Postplay
Now the IT manager came into play and on the same day changed the CEO’s password and activated multi-factor authentication for all employees. In addition, the IT manager discovered and deleted all inbox rules that he had found for the CEO’s inbox.
One day later, on Thursday, the attackers again sent an e-mail on behalf of the first investee to an employee and asked for the still outstanding payment. This was because they knew that their attack was noticed in the second case, but they also knew that their first attack was probably still undetected, so they could continue.
What they did not know, however, is that the money has already been frozen by the bank because of suspicious activities. Surprisingly, the attackers were in contact with one of the employees until Tuesday of the following week, when they finally gave up and the last remains of them had been removed.
Lessons Learned
The criminals behind the attack acted very deliberately all the time and always achieved the best possible result according to the circumstances. In the beginning, they tried to get as much data as possible, as quickly as possible, in case the attack was immediately detected. After some time, they became calmer and reacted to the concrete content of the e-mail inbox and planned their next steps. They always tried to keep the conversation focused, not to ask new questions and to behave as normal as possible. They constantly adapted by editing a PDF, changing their e-mail formatting or using similar wording as the genuine investees.
In the end, trust, automatisms and single communication channels played into the cards of the scammers. So here are some tangible approaches that you can implement immediately:
- Critical changes, such as bank details, should always be approved twice. An additional verification with your customer for confirmation is enough to expose the fraud early. Pick the phone and talk to them.
- Do not always reply to the same old e-mail history. Also write a new e-mail and check the e-mail address of the recipient. This way, you will avoid replying to an attacker and also receive more organization – for free.
- E-mails are usually as insecure as letters. Anyone can write any sender on it. So do not have blind faith in them.
- If you are in doubt whether an e-mail is genuine or not, ask or assume that it is spam. In the worst case, your contact will get back to you and you can argue that the message was caught by your personal spam filter.
Here are also some important tips for Office 365:
- Enable multi-factor authentication for all accounts.
- Use Conditional Access to restrict access to accounts as much as possible (e.g. login is only allowed from certain countries or IP addresses).
- Disable access via legacy protocols via IMAP, POP and SMTP, otherwise you will override the multi-factor authentication.
- Check your accounts for hidden inbox rules using our instructions from a previous blog post.
Leave a Reply