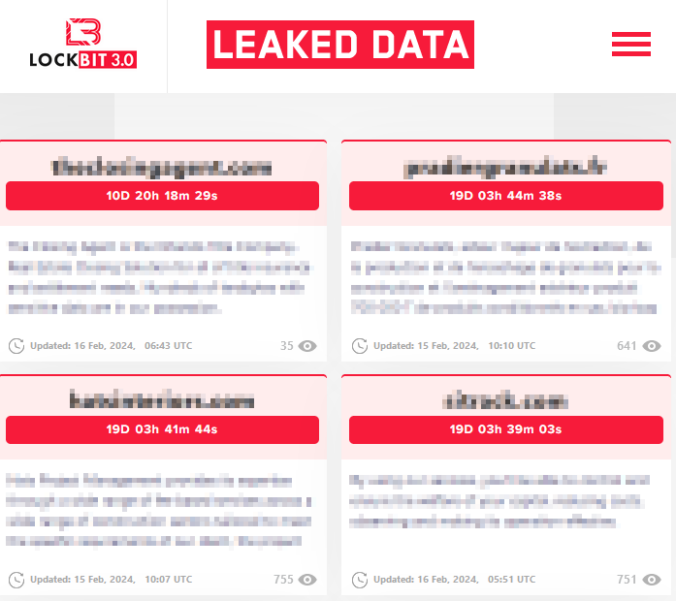
Over the past few years, we have had the opportunity to conduct several Purple Teaming exercises together with our customers.
Particularly after Purple Teaming exercises involving external providers, we often see a mismatch between the customer’s expectations and the service provided.
This blog post attempts to summarize how to prevent the most prevalent issues with a managed security service as early as possible.