This is hopefully the most useless blog post you will read this year as this post will detail our experience dealing with ransomware cases. It is one of the most common reasons why we get called in to help and it has become a big business. Chainalysis, for example, has tracked $1.1 billion in ransomware payments in 2023 alone.
How does a ransomware attack unfold?
Initial Access
First, a threat actor (TA) gains initial access to the infrastructure. This is usually done with password phishing, exploiting unpatched systems or by using leaked credentials (trying username/password combinations from other leaks). Some ransomware groups carry out attacks themselves, while others buy access from an initial access broker (where the initial access broker only gets a foothold in an organization and sells that access on the darknet) or recruit affiliates to perform “postpaid penetration tests” and provide them with encryption tools for a percentage of the profit.
Privilege Escalation and Lateral Movement
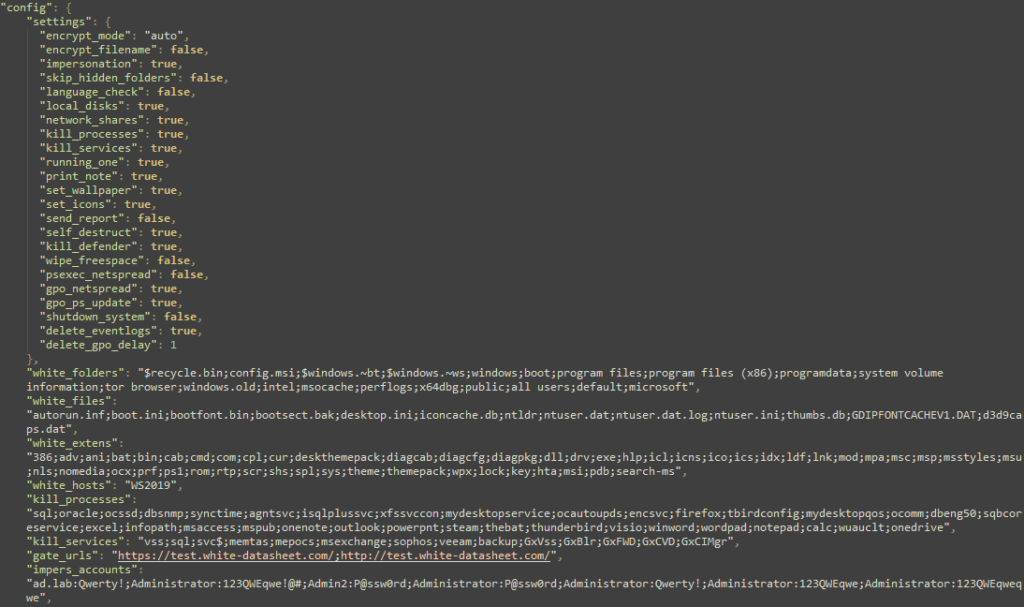
Once the TA has a foothold, they analyze the networks and configurations to identify ways to gain more privileges and pivot to other systems. They also look for files of interest, such as personally identifiable information (PII), patents, or trade secrets — essentially, anything that can be used for extortion. Additionally, they look for accounting information and balance sheets to guesstimate the ransom amount. They may also look for a cyber insurance policy which might mention payout limits in the event of a ransomware attack. How long does this phase take? Depending on the infrastructure, it could be as little as a few hours. According to Sophos’ analysis, it takes attackers on average just 16 hours from initial entry to taking over an Active Directory environment. We can second this with experience from internal penetration testing and red teaming engagements.
Data Exfiltration
Once a TA is satisfied with the access, they move on to the final two steps. First, all the data of interest is uploaded to a file transfer services such as Dropbox or Mega, or to a TA-owned infrastructure. Finally, the ransomware is deployed, and the encryption routine is run. Today, most TAs do not build their own ransomware, but instead use Ransomware as a Service (RaaS). These RaaS tools vary in sophistication, offering everything from simple encryption/decryption solutions to integrated darknet leak sites and automated bitcoin payment verification handling.
File Encryption
The approach to file encryption has changed significantly over the past decade. Early ransomware would immediately start encrypting on infected computers, which quickly drew attention when computers slowed down or became inaccessible. Nowadays, the perpetrators know that they will raise red flags by shutting down and encrypting an entire server farm, so they come back late at night when system administrators are asleep. Furthermore, the ransomware is programmed not to encrypt everything. Operating system files are usually left untouched, allowing the computer to boot and run. Another trend is to encrypt entire virtualization environments such as ESXi, underscoring the importance of centralizing logs.
Ransomware note
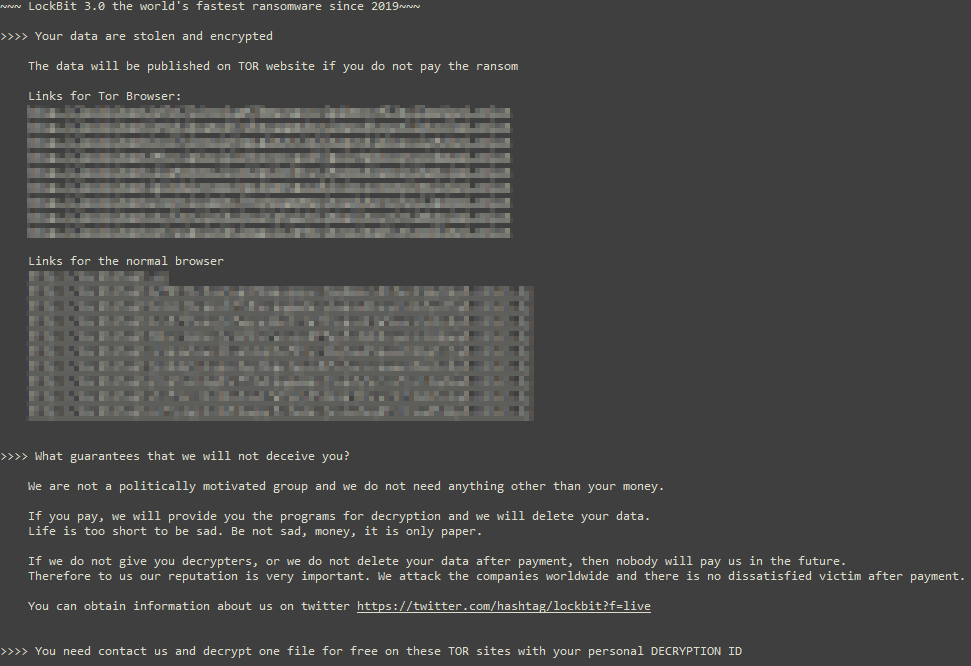
After encryption, the TA waits for the victim to contact them. Some TAs list their victims on darknet leak sites and threaten to leak stolen data, including the PII they have stolen. As a result, many countries now require reporting of data leaks. There have even been reports of the TA moving on and reporting the breach to the authorities!
The aftermath
When a data breach occurs, there are only unfortunate choices. The second best option (the best, of course, is never to be in this situation in the first place) is to restore from backups and identify the data that was lost. Restoring from backups requires some care, as the TA may have been in the system longer and placed some cleverly hidden backdoors. A thorough investigation is still required. Key details to determine include how and when the TA accessed the systems, how they escalated privileges, what data was stolen, and whether there are any surprises left in the form of backdoors.
If systems are unrecoverable, or if backups have been deleted because the attacker gained access, you may have to negotiate. Should you? Ideally, no. You are feeding the dark side! Even just contacting gives them a motivational boost. Another important consideration is that paying is not a panacea that solves all problems. First of all, recovery with a decryptor might not be faster at all, and there’s no guarantee that the data won’t be leaked. It might also put you on a list of “companies willing to pay ransom”, which could invite further attacks. Remember, you are dealing with shady people.
Negotiation
If negotiations are unavoidable, we recommend hiring an experienced negotiator to guide you through the process as safely as possible. Clarify the goals of the negotiation — whether it’s to determine the price, buy time, obtain the decryption tool, or prevent the data from being leaked. The most important (and most difficult) thing to remember before starting a negotiation: The moment you enter a negotiation, it becomes a business deal like any other. Emotions will not help. Think of this negotiation the same as when a paper mill needs an emergency supply of wood pulp.
How to not become a victim in the first place?
Remember, you don’t have to be the fastest when running from a fancy bear, just not the slowest. The same goes for ransomware. Ransomware groups are in it for the money (or in the words of Lockbit3: “We want nothing more than money”). Most victims we see are victims of opportunity, not targeted attacks. Here are some general recommendations for running fast enough from the bear:
- Have immutable or detached backups that cannot be encrypted in the event of a complete environment compromise
- Test the restore to ensure that all required information and configuration is included in the backups
- Have 2FA enabled for at least all external accounts
- Have an emergency patching process in place, especially for externally exposed systems
- Install an endpoint protection solution on all endpoints and monitor the alerts it generates
- Have network segmentation in place and enforce it with no exceptions
- Check your Active Directory for misconfigurations that allow privilege escalation
You can contact our Incident Response specialists for negotiation assistance.
Want to learn the techniques of the hackers?
Gain hands-on experience and train your IT security skills in realistic attack scenarios with our Internal Network and System Security course in Zurich June 3rd to 5th.
The course covers prevalent security issues, attacker tools, and methodologies, and introduces countermeasures for vulnerabilities commonly exploited. Seats are limited. Sign-up now.
https://www.compass-security.com/en/trainings/internal-network-and-system-security/inss-zurich-june-2024
Note: This training will be held in German only (slides/course material are in English).
Leave a Reply