This blog post introduces our new custom queries for BloodHound Community Edition (CE) and explains how you can use them effectively to analyze your Active Directory infrastructure.

TL;DR: Check out our new BloodHound CE custom queries!
Active Directory and BloodHound
The majority of our customers run a Microsoft Active Directory infrastructure, either exclusively on-prem or increasingly in hybrid environments using Entra ID. BloodHound is one of our primary tools for identifying potential misconfigurations and attack paths in Active Directory. Therefore, we use BloodHound to analyze our customer’s infrastructure in nearly every internal penetration test we conduct.
In 2020, we published some custom queries1, to get even more out of the collected data with BloodHound. These are available on GitHub2.
In August 2023 3, the BloodHound Community Edition (CE) was released. The queries from the “legacy” version of BloodHound are not compatible with the new CE version. To address this, we rewrote the queries to ensure compatibility with the CE edition and added many new queries to uncover even more attack paths. These queries can be found in our new BloodHound CE repository on GitHub4:
BloodHound CE Queries
The queries are available in a markdown file in the repository, allowing you to easily copy (1) them to your BloodHound CE instance. Sometimes, the queries also contain some additional information (2):
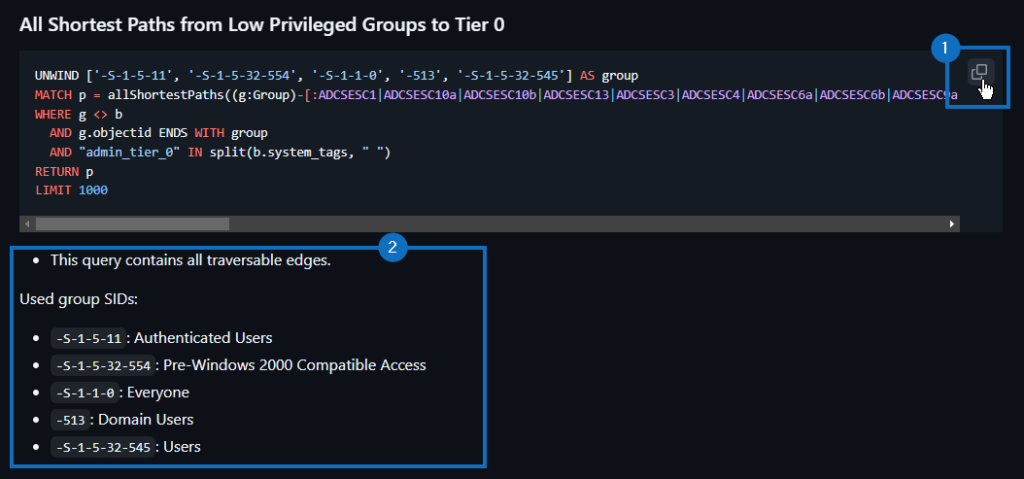
BloodHound CE only supports importing queries through the BloodHound API. The Readme contains step-by-step instructions that guide you through the process of importing the queries, along with a script that simplifies the entire procedure using BloodHound Operator5.
Once the import is complete, you will see the queries in BloodHound (since ordering and categories are no longer supported, some ASCII formatting and a numbering scheme has been used instead):
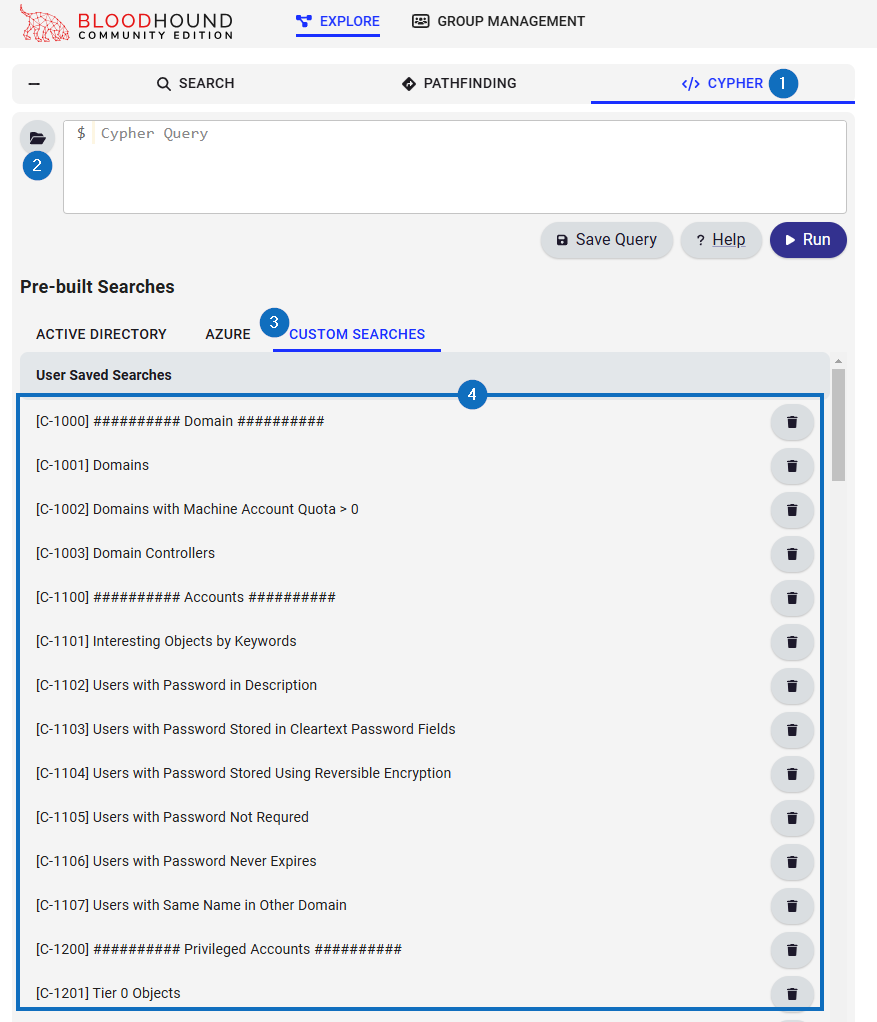
There are queries regarding the domain, accounts, privileged accounts, computer accounts, Kerberos, owned objects, shortest paths, DACL abuse, GPOs and ADCS. I won’t go into detail about all these queries — you should try them out for yourself! BloodHound also provides you some example data6.
BloodHound Operator Queries
Since the new BloodHound no longer supports queries that update objects, we had to adopt a different approach. We decided to use BloodHound Operator to modify the objects. After importing the BloodHound Operator module and authenticating to the BloodHound API, the queries can be copied and pasted from the corresponding markdown file.
For example, if you want to set the groups “Server Operators”, “Account Operators” and “Print Operators” as high-value targets, you can use the first query:
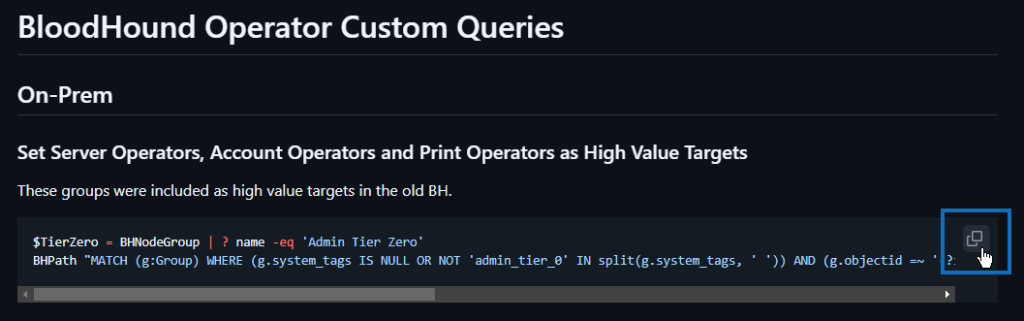
This will now mark these groups again as high-value, as it was in BloodHound legacy:
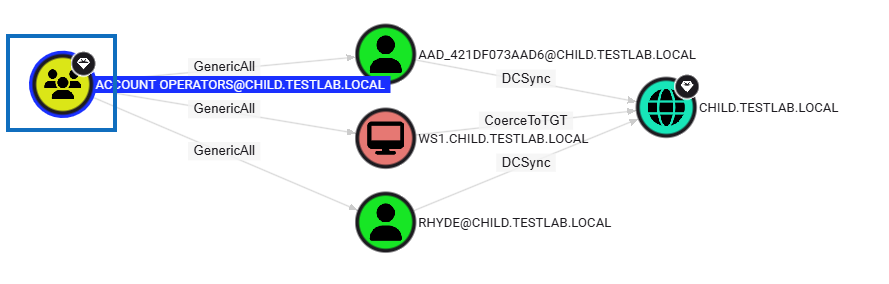
There are several queries that set various accounts as high-value targets, add information about SMB signing, and remove inactive accounts. Be sure to check them out!
BloodHound Legacy vs. BloodHound CE
The new BloodHound CE version is not yet perfect. Some useful features from the legacy version are missing, such as the back button, the ability to remember the “layout” display setting, custom query import via the UI, custom query ordering and categories, selection dialogues in queries, modifying queries, or UNION queries. However, these are minor issues, and either workarounds exist or some workflows may need to be adjusted.
Unfortunately, there is at least one more significant bug. The RDP/Admin/Code Execution edges are not always shown when configured via GPO7. Since this information can be very crucial for penetration tests, it’s still necessary to use the legacy BloodHound version alongside the CE version until this is fixed.
Nonetheless, we really encourage using the new CE version! It includes many more edges and attack paths, such as all those related to AD Certificate Service abuse, applying GPOs, collecting additional AD properties, and, not to forget, all the attack paths concerning Azure/Entra ID (which we will cover in another blog post, stay tuned!).
For more information about BloodHound, its usage, possible attacks, and more, refer to the official documentation8.
So, have fun using our queries while exploring your next attack paths ;-)!
Want to Learn Hands-On?
Gain experience and train your IT security skills in realistic attack scenarios with our Internal Network and System Security course in Zurich May 5th to 7th.
The course covers prevalent security issues, attacker tools, and methodologies, and introduces countermeasures for vulnerabilities commonly exploited. Seats are limited. Sign-up now.
https://www.compass-security.com/en/trainings/internal-network-and-system-security/inss-zurich-may-2025
References
- Make the most out of BloodHound: https://blog.compass-security.com/2020/07/make-the-most-out-of-bloodhound/ ↩︎
- GitHub, Compass Security, BloodHoundQueries: https://github.com/CompassSecurity/BloodHoundQueries ↩︎
- BloodHound Community Edition: A New Era: https://posts.specterops.io/bloodhound-community-edition-a-new-era-d64689806e90 ↩︎
- Github, Compass Security, BloodHound CE Resources: https://github.com/CompassSecurity/bloodhoundce-resources ↩︎
- GitHub, SadPRocessor, BloodHound Operator: https://github.com/SadProcessor/BloodHoundOperator ↩︎
- BloodHound Example Data: https://github.com/SpecterOps/BloodHound/wiki/Example-Data ↩︎
- BloodHound Issue regarding RDP/Admin/Code Execution Edges: https://github.com/SpecterOps/BloodHound/issues/240#issuecomment-2437805997 ↩︎
- BloodHound Documentation: https://support.bloodhoundenterprise.io/ ↩︎
This is amazing work thank you.