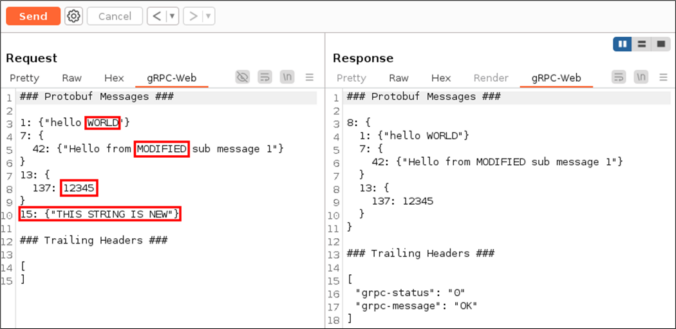
The gRPC framework, and by extension gRPC-Web, is based on a binary data serialization format. This poses a challenge for penetration testers when intercepting browser to server communication with tools such as Burp Suite.
This project was initially started after we unexpectedly encountered gRPC-Web during a penetration test a few years ago. It is important to have adequate tooling available when this technology appears. Today, we are releasing our Burp Suite extension bRPC-Web in the hope that it will prove useful to others during their assessments.