The analysis of Social Media apps gets more and more weight as these applications gain momentum with end users. Thus, forensic analysts must not only understand how to grab files and content from a suspects computer but also from its online services (not to use the damn Cloud word). Therefore, it is crucial to understand the full functionality of online Social Media applications since not only publicly published contents but also hidden and drafted files may be of interest to investigatory entities.
In the end, investigators would need to understand how to recover passwords from supporting desktop software such as blog client programs. This article should point out on how to recover user accounts and passwords from the well used Blogilo KDE (Linux) blog client software.
All KDE applications configuration files are stored within the user home ~/.kde/share/apps folder. Blogilo does store its configuration within that path as well.
cbrunsch@tubarao:~$ ls -laR .kde/share/apps/blogilo/ .kde/share/apps/blogilo/: total 92 drwx------ 4 cbrunsch cbrunsch 4096 2012-01-06 08:21 . drwx------ 11 cbrunsch cbrunsch 4096 2011-12-29 16:10 .. drwx------ 2 cbrunsch cbrunsch 4096 2012-01-02 23:03 1 drwx------ 2 cbrunsch cbrunsch 4096 2011-12-28 17:10 -1 -rw-r--r-- 1 cbrunsch cbrunsch 62464 2012-01-06 08:21 blogilo.db .kde/share/apps/blogilo/1: total 48 drwx------ 2 cbrunsch cbrunsch 4096 2012-01-02 23:03 . drwx------ 4 cbrunsch cbrunsch 4096 2012-01-06 08:21 .. -rw-rw-r-- 1 cbrunsch cbrunsch 29586 2012-01-02 23:03 style.html .kde/share/apps/blogilo/-1: total 8 drwx------ 2 cbrunsch cbrunsch 4096 2011-12-28 17:10 . drwx------ 4 cbrunsch cbrunsch 4096 2012-01-06 08:21 ..
Actually, the file of interest is the blogilo.db file. Let’s see whether we can read the accounts directly from that file.
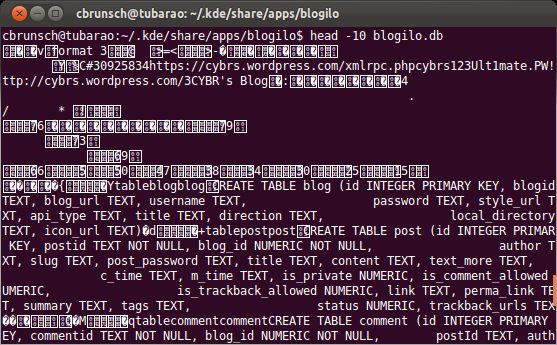
We could try to guess from the output what the username and password might be. However, there is also some more binary content. Thus, let’s have a closer look.
cbrunsch@tubarao:~/.kde/share/apps/blogilo$ file blogilo.db blogilo.db: SQLite 3.x database
The file command reports an SQLite database. To store the configuration of applications within the file based SQLite format is becoming very popular. Also Firefox does store passwords and history information within databases of the SQLite format. Luckily, these files could be queried very conveniently using an SQLite client. The schema information of that specific Blogilo database can be queried from the sqlite_master table contained within the same file. The schema does also contain information on existing tables.
cbrunsch@tubarao:~/.kde/share/apps/blogilo$ sqlite3 blogilo.db SQLite version 3.7.9 2011-11-01 00:52:41 Enter ".help" for instructions Enter SQL statements terminated with a ";" sqlite> select name from sqlite_master where type="table"; blog post comment category file post_cat post_file local_post local_post_cat temp_post temp_post_cat sqlite> select * from blog; 1|30925834|https://cybrs.wordpress.com/xmlrpc.php|cybrs123|Ult1mate.PW!|http://cybrs.wordpress.com/|3|CYBR's Blog|0|| sqlite>
Here we go. For each configured blog, there will be an entry within the blog table. Each of the records will contain the XML-RPC interface URL as well as the username and password of the blog account. That logon information will also grant access on the online service and would allow to seize hidden and drafted evidence.
NOTE: You must install the SQLite version 3.x client otherwise you won’t be able to query the file.
Leave a Reply