Fridays, I was approaching a win32 reversing challenge. So I transferred the binary into my Windows XP virtual box and fired-up OllyDbg. The goal was to bypass the username and password prompt that occurred on application startup. Hilariously, I was just providing a dummy name and password to the app…. “asdf” “asdf” as probably most penetration testers have done so, over and over to test logon prompt behavior.
BANG… the app is telling me: “Correct, le clef est Le saucisson vaudois ca rapicole.!”
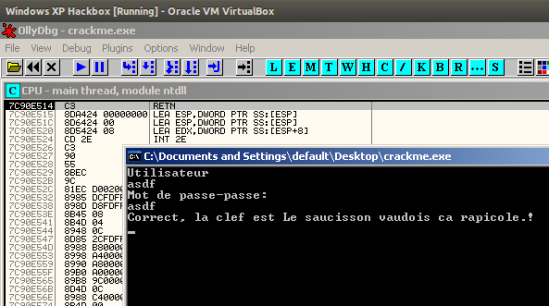
The force was with me and actually, only Chuck Norris could have topped that :). Was I in god mode? Probably not. Later analysis just revealed that the application required the password to be equal to the username and had some minimal restrictions on the credentials length.
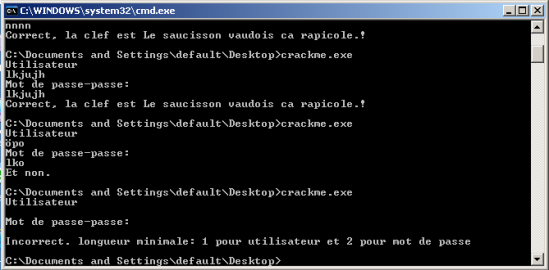
All in all, a 30 seconds exercise.
Lessons learned:
– Implement strong password policies
– Give it a try before you hurry to launch Olly.
Leave a Reply