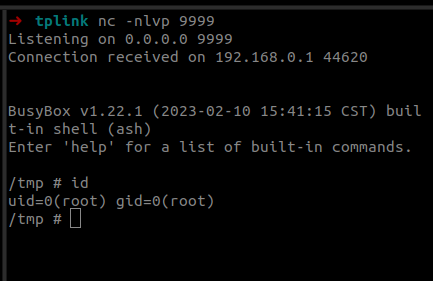
Last year we participated in the Pwn2Own 2023 Toronto competition and successfully exploited the Synology BC500 camera. The DEVCORE Internship Program team managed to exploit a bug in the TP-Link Omada Gigabit VPN Router. So I was naturally curious and wanted to figure out how difficult it would be to recreate that exploit having access only to a high-level bug description and the firmware.
Compass Security Blog
Offensive Defense
A journey into the discovery of privilege escalation vulnerabilities in the Lenovo Update process.
One of the rare cases where we can decrypt and recover files following-up with a ransomware attack.
Passwordless products promise greater security and convenience by allowing users to log in to Windows systems with only their smartphone. But what is going on behind the scenes and how could a domain’s security stance be worsened by such a solution? In this post I will explain how these products are implemented and detail the vulnerabilities and weaknesses discovered in three tested products.
We show how to decrypt passwords from the configuration backup of a Xerox WorkCentre and how, during the reverse engineering, a command injection vulnerability was discovered (CVE-2021-27508).
In this blog post we will reverse engineer a sample which acts as downloader for malware (aka a “dropper”). It is not uncommon to find such a downloader during DFIR engagements so we decided to take a look at it. The sample that we are going to analyze has been obtained from abuse.ch and was […]
Black box analysis of a not so smart card in ID-1 form factor that is in use for the billing of washing machines and tumble driers.
This post will give a quick intro into software defined radio (SDR) basics and provide guidance for the decoding of a very simple form of digital modulation (on-off keying). Device Wireless Specs Wireless junk hacking is not too difficult. Usually, devices transceive in the 433MHz or 868MHz ISM radio bands. As these bands are somewhat lax […]
Back in Black (back from Black Hat with a bag full of schwag and branded black shirts). Black Hat and DEF CON again allowed insights into latest research and concerns. Where some topics loose grip ( vulnerability scanning, IPv4, DNS, general web issues) others gain momentum (DDoS, mobile computing, smart energy, industrial control and embedded […]
“Jailbreak Detection” is a set of checks, mostly performed by Mobile Device Management solutions like MobileIron / Good Technologies or other third party Apps to determine if a device is jailbroken or not. It checks if all security controls of Apple’s iOS are still in place and if we can / should / want “trust” […]
© 2025 Compass Security Blog