Update – 13.10.2015: Netgear published a new firmware (version 1.1.0.32) which fixes the reported authentication bypass.
My most recently appointed colleague, Daniel Haake, described in the previous blog article “Authentication Bypass in Netgear WNR1000v4 Router” how he found an authentication bypass in commonly used Netgear firmwares. Due to the rediscovery of the issue and its public disclosure, we decided to go public despite the fact Netgear did not yet release a fix for the identified security hole.
Shortly after the release of the Compass advisory on public mailing list Bugtraq, we were contacted by Joe Giron, who experienced troubles with his Internet connection around September 27th. On September 28th, Joe noticed that his Netgear router’s primary DNS server had been set to point to a non-standard DNS server. This timeframe means that attackers were active before the release of Shellshock Lab’s blog article (which is detailing the same vulnerability). Joe mentioned that the remote administration interface of his Netgear router was accessible via the Internet, but protected by a strong password. He therefore had high suspicions that he fell victim of an attack against an unpatched vulnerability in his router. The release of our advisory was the confirmation and technical explanation of it.
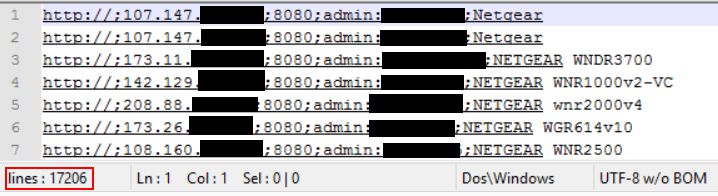
The IP of the rogue DNS server set in his router did not only expose a DNS service, but also a web server. This web server served various PHP scripts, log files and text files. The logs contained over 17’000 entries of presumably hacked routers, including their IP address, username and password of their administration interfaces. A further analysis of this list would identify more than 11’000 unique routers.
As we discovered that this authentication bypass was being exploited in the wild and that over 10’000 users were affected, we contacted Switzerland’s CERT for further help. GovCERT was very helpful and took over the case by
- Attempting to contact Netgear again to urge them to release the patch
- Analyzing the logs of the web server and identifying the victims
- Taking down the command and control server to avoid further infections
- Liaising with GovCERT’s partners worldwide to notify the Internet service providers of the victims
In the meantime, the media got interested in the advisory and Threatpost published yesterday evening an article about the flaw and its follow-up. A second person reached out to us after the publication of this article, describing the same infection vector as well as the same IP address for the DNS and C&C server. We are currently in contact with other media outlets and will update this section when further articles are released.
The debate between responsible- and full disclosure is endless and both approaches have their pro- and cons. At Compass Security, we attempt to get the best balance between these two approaches. We are confident that our approach of leaving some time for the vendor to patch the vulnerability before publicly disclosing the issue in case of no adequate response was the best. Public information has proven to work and helped identifying ongoing attacks. Coordination with the relevant authorities allowed coordinated action against the attackers and will hopefully help the victims of this hack.
Media Update, 11.10.2015:
- Leichter Zugriff auf den Router möglich (Inside-digital.de)
- Mehrere Netgear Router können leicht übernommen werden (derstandard.at)
- Netgear router exploit detected (bbc.com)
- Critical Netgear Router Exploit allows anyone to Hack You Remotely (thehackernews.com)
- Netgear Router Vulnerability: Are You At Risk? (tomsguide.com)
- @hacks4pencakes (twitter.com)
- @dragosr (twitter.com)
Media Update, 12.10.2015:
- Hackers exploit serious unpatched Netgear router DNS vulnerability (betanews)
- Netgear patch delay left thousands of routers under attack (SC Magazine)
- Netgear To Release Patch to Fix Wireless Router Vulnerability (Legit Reviews)
- 10,000 routers attacked through unpatched Netgear DNS vulnerability (IT Pro Portal)
- Sicherheitslücke: Zehntausende Netgear-Router kompromittiert (Heise Online)
- Sicherheitslücke in Netgear-Routern ermöglicht Fernzugriff (Golem)
Leave a Reply