“Fake President Fraud” or “CEO Fraud” is a social engineering attack where an adversary tries to convince a member of the financial department of a company to send out a payment to the attacker’s bank account. The attack can be divided into three steps.
- Establish Contact:
Typically only employees responsible for bank transfers get contacted by the adversary, as they have all needed permissions to execute payments. Therefore the criminal impersonates a CEO or any other superior who has enough authority to arrange urgent payments.
These kind of social engineering attacks work if the adversary gathers enough information about the individual he wants to impersonate. As most CEO’s are referenced on the world wide web with detailed personal information such as curriculum vitae and email address, it is easy for an attacker to gather everything he needs to fake a CEO email. Furthermore, company websites often disclose information about customers and other useful details which help an adversary to be more convincingly when requesting a payment. - Request Payment Transaction:
The attacker often uses email (spear phishing) or phone calls (vishing) to contact his target. Whereby a phone call only works if the victim does not know the voice of the impersonated superior, an attack over email has no such restrictions.
The request itself is about an urgent payment to a foreign bank account and uses a variety of pretexts such as acquisitions or customer projects. For this step to succeed, the criminal uses different elements to convince the target to be compliant to his request and send out the payment:- Authority: Asking the target as an authority adds a strong argument to every request. Jonathan J. Rusch writes “People are highly likely, in the right situation, to be highly responsive to assertions of authority, even when the person who purports to be in a position of authority is not physically present.” One of the most impressive experiment in social psychology history, which demonstrated the blind obedience to authority figures, is the Stanley Milgram experiment.
- Valorization: The “fact” that the CEO or a superior has “chosen” this specific employee implies that he trusts him. The feeling of being trusted makes the body release oxytocin, often referred as the “love hormone”. This hormones facilitates trust and attachment between individuals. This is an additional factor that helps the attacker to quickly build feelings of rapport and to convince the target to be compliant to his request and send out the payment.
- Secrecy: In order to avoid that a target verifies the authenticity and validity of an order, attackers often label the request as “STRICTLY CONFIDENTIAL” or insert statements like “this project is still secret and its success depends on this transaction”.
- Pressure: Shifting all the responsibility for the success or failure of a project to the target’s shoulder, the attacker put a lot of pressure on him. This will induce the victim to be more compliant and execute the request.
- Urgency: Urgency and authority is a good combination to convince the target to perform the payment as fast as possible. The attacker creates a false sense of urgency in order to get the target to make a rushed judgment or a rash decision. Example email:
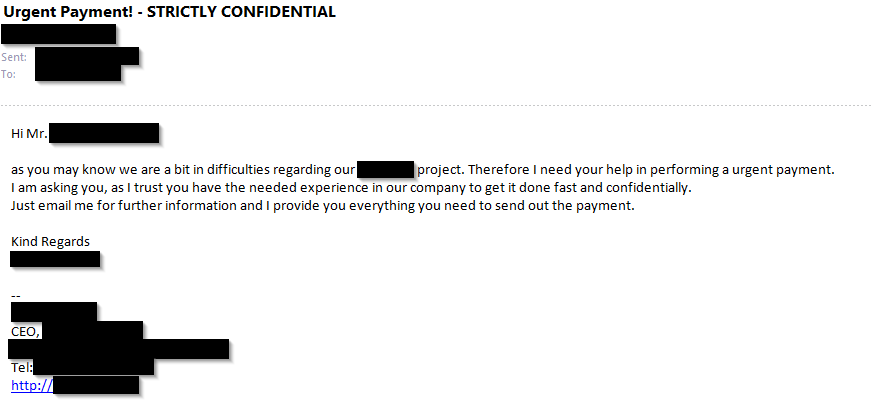
- Transfer Money:
If the attacker manages to convince the targeted employee to send out the payment, the money gets transferred to the foreign bank’s account.
Now the question arises what a company can do to avoid a “Fake President Fraud”. Different organizational and technical steps can be done to mitigate the risk of an incident.
- Organizational:
- If possible email or phone communication should not be allowed when authorizing large payments. Therefore face-to-face meetings should be mandatory.
- Develop and communicate guidelines and processes of how payment transactions need to be handled.
- If a transaction does not fit the defined process it should be necessary that the employee asks feedback questions which verify that it is a authorized request.
- Employees should participate a special social engineering training to learn how to avoid getting manipulated by an attacker. The goal of the course should be to convey how an attacker thinks, arise a general awareness for social engineering attacks and explain that such attacks are not limited to one communication channel (e.g. email, SMS, WhatsApp, personal).
- Only publish as little financial and personal information in social media and company websites as necessairy. This makes it harder for an adversary to prepare his attack.
- A two-step (4-eyes) verification process when sending out large amounts of money to foreign bank accounts helps mitigating the damage an attack. It is important that the companies culture is good enough that the second person actually really reviews the payment and can challenge the first person without fears for both of them of being in a “Big Brother” system.
- Do not allow employees to use their personal email address for business purpose. This avoids that a compromised private email account allows someone to gain business data access.
- Technical:
- Do not allow that an email from an external mail server is accepted by your mail server when the email address contains your domain name.
- Always use email signatures/encryption at least when sending mails with confidential and/or sensitive content (e.g. S/MIME, PGP).
- Mark emails from external mail-servers with a tag inside the subject (e.g. [EXTERNAL]). This should be done when the emails enter the company’s mail server. With conditional formatting mails can be marked in red if the mail originates outside the company.
- To avoid an Outlook WebAccess from being hacked and used to perform a CEO Fraud, a strong authentication method should be used in addition of a strong password policy (e.g. client certificates, two factor authentication or access restriction to VPN traffic only).
- Attackers may register and use similar looking domains for a CEO fraud attack. To be aware of this, the company should check if there are any similar existing domains (e.g. .co instead of .com top-level domain) and blacklist them on their mail server.
- Additionally the company should try to register all similar looking domains to make it harder for an attacker to register a domain for his attack which looks slightly different then the domain of the company.
Even if the described attack is a real threat, exploited by attackers around the world every day, there are some effective steps to mitigate the risk of an incident as shown above. Especially an awareness training where the employee is taught when to be suspiciously and how attackers try to manipulate people is recommended, as this is the best protection against different types of social engineering attacks.
Leave a Reply