On October 12th the Swiss Cyber Storm conference took place in the Kursaal in Bern. Several Compass analysts attended the conference, our security analyst Yves Bieri held a talk and we also had a booth. The conference was great fun, finally a in-person conference with many interesting talks. This blog post wraps up some talks we attended.
Talk: Patterns and anti-patterns in software development
In this talk Philippe de Ryck talked about helping programmers writing secure code.
The main point made in this presentation is that important security behavior should be encapsulated in libraries. To illustrate this, de Ryck talked about an Apache Pulsar JWT vulnerability. The vulnerability allowed the use of the algorithm “none”. This basically means the JWT is not signed and there are no security guarantees anymore.
Checking the source code of the vulnerable and the fixed version shows that it is not immideatly clear how the vulnerability came to be and why it is now fixed:
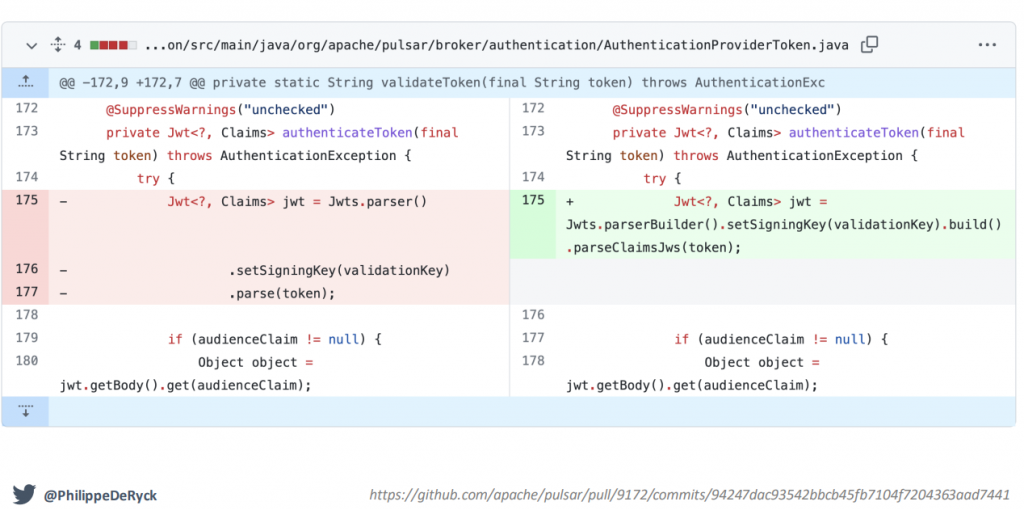
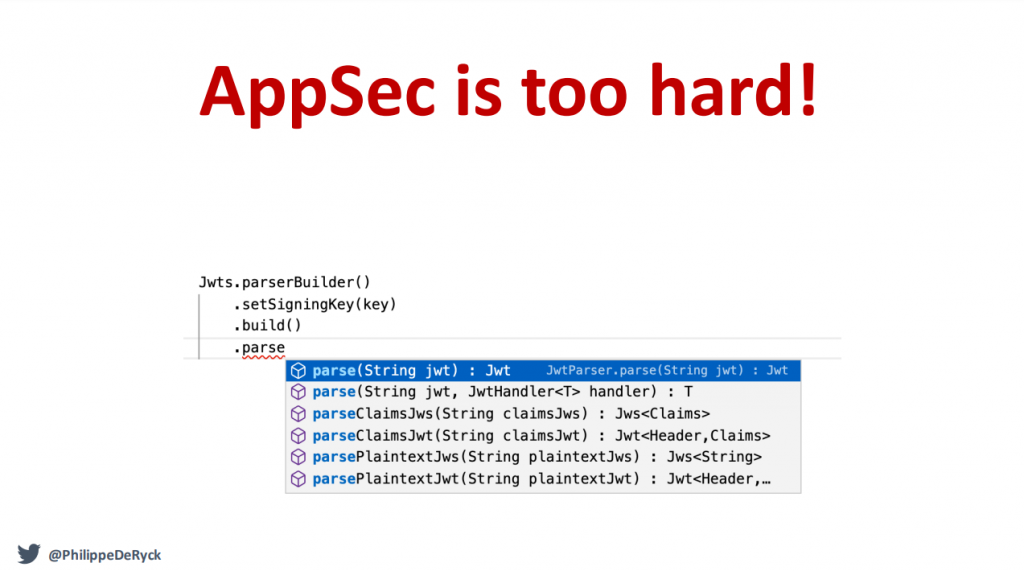
If the JWT library works like this, then such vulnerabilities are bound to happen since in this specific example developers would need to read the source code of the different functions to figure out if algorithm none would be accepted. Instead, a single function, which implements parsing of a JWT securely, should be made available to developers.
Talk: Suppliers! Resist Phishing, Implement FIDO2
In this talk Compass Security Analyst Yves Bieri showed how FIDO2 based authentication can prevent phishing attacks.
The problem with traditional second factors is that they do not protect against credential phishing. A malicious webserver, impersonating the target server, can simply forward both the password and the second factor token to gain access to the target server.
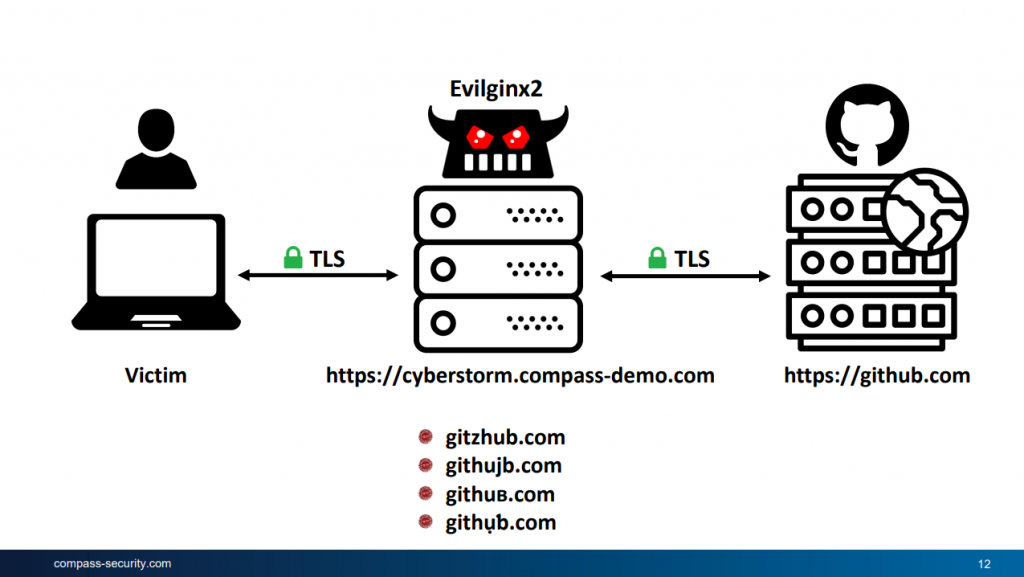
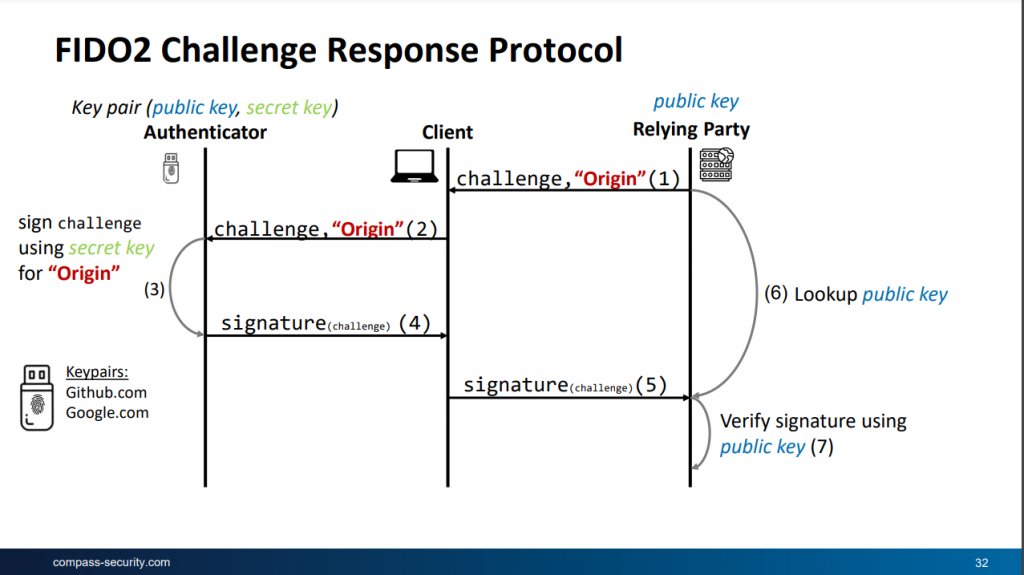
How does FIDO2 stop such an attack? Basically the origin of the server, to which the user wants to login, is passed to the authenticator. Even though a human may be fooled by a similar looking origin (for instance gitzhub.com vs github.com), the authenticator will not. The malicious origin will most likely not be in the authenticator’s keypair list and the login will fail.
Even if the malicious origin is in the keypair list, the keys for signing are unique. Thus, simply relaying the signed challenge will fail since the public key the target server will use to check the signature will not correspond to the private key used for signing.
Talk: Climbing the Hacking /mnt/ain
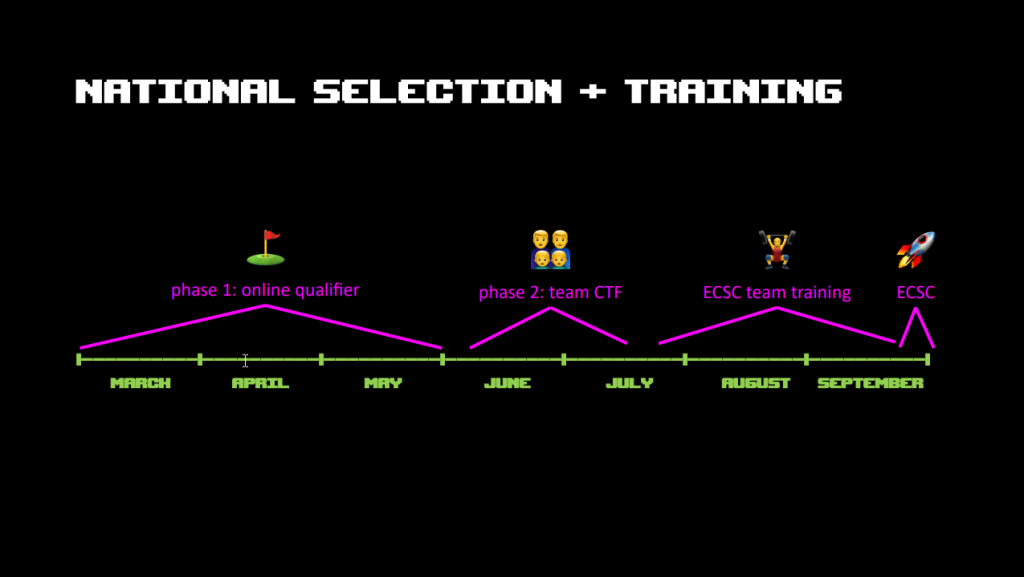
In this talk Miro Haller talked about /mnt/ain, the Swiss ECSC (european cyber security challenge) team, the team’s journey to the tournament and how the team fared.
The journey to the ECSC had three phases. In the first phase an online qualifier was used to select 16 candidates from over 200 people who had participated. In the second phase a 1 day on-site CTF was organized to select the team members who would travel to Prague to participate in the ECSC. In the third phase the selected members trained for the upcoming CTF event, playing almost every weekend, which resulted in the team ranking number 86 worldwide (in only 3 months of playing).
At ECSC the CTF took place over two days against teams from all over Europe. The team was in fourth place up to 6 hours before the end but then dropped to 11th at the end.

To show the difficulty of the ECSC challenges, a heap exploitation challenge, which the team solved during the competition, was presented.
Mini-CTF
The Hacking-Lab organized a CTF with some fun challenges. Participants of the CTF had a chance to win some great prices at the conference raffle.

We’re looking forward to participate in the conferences next year (Insomni’hack, Area41, Swiss Cyber Storm). If you also plan to attend them, don’t hesitate to ping us!

Leave a Reply