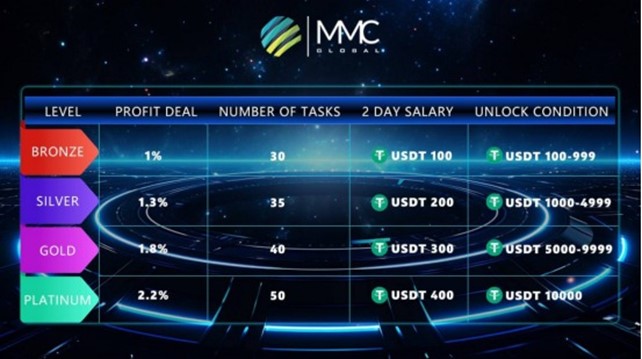
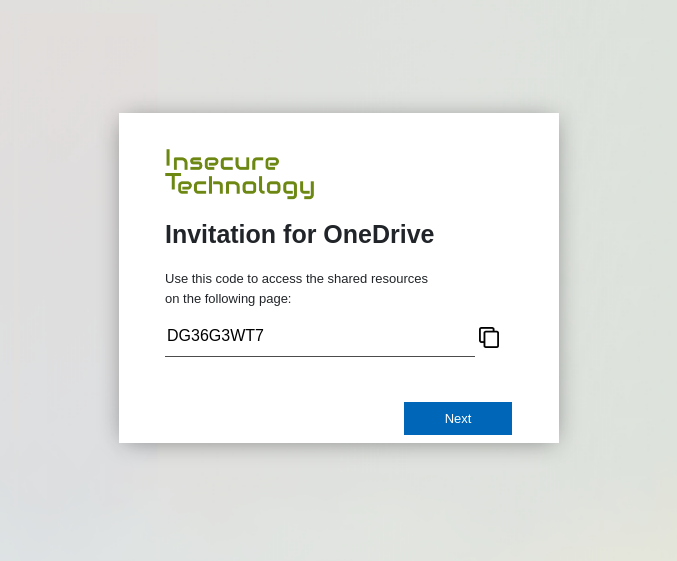
In the era of the internet, scams vary in forms, targeting those who aren’t cautious. Lately, a fresh scam focused on Switzerland has gained attention on social media and in the news. This scam revolves around job offers from a seemingly genuine headhunting company. I chose to engage with the scammers to uncover the secrets of this scheme.
Compass Security Blog
Offensive Defense
Device code phishing is nothing new. In fact it has been around for some years now. Despite the awesome capabilities of device code phishing, it is not widely used by threat actors. Therefore, it probably does not receive much attention from Microsoft. Compass Security is releasing two tools that can work hand in hand in a device code phishing exercise or even your next red team engagement.
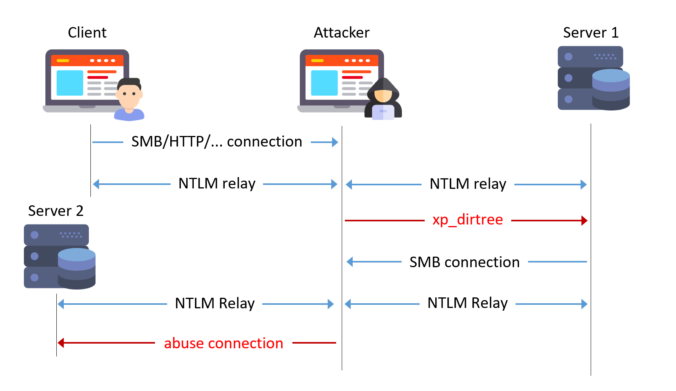
Readers of this blog probably know that I like to try NTLM relaying over all protocols possible! Relaying to Microsoft SQL (MSSQL) is known to work when using the default weak configuration.
With this blog post, we show some dangerous configurations and release a small tool to automate NTLM relaying in these cases.
Internet of Things (IoT) and Operational Technology (OT) is an area that has grown strongly in recent years and is increasingly being used in the business world. To be able to test the security in this area, let’s take a closer look at the Message Queuing Telemetry Transport (MQTT) protocol to understand the strengths and weaknesses of the protocol.
Nowadays, web developers rely mostly on well-established frameworks to develop their platform or web sites. These frameworks take care of many vulnerabilities like XSS, SQLi, etc. and give the developers a care-free environment.
However, there is one sneaky weakness that can escape the usual checks quite easily and go undetected: SSRF.
A journey into the discovery of privilege escalation vulnerabilities in the Lenovo Update process.
When accessing a remote server, one should always assume it has been compromised or might be in the near future. It is particularly crucial for users with administrative privileges to establish a secure connection to the Remote Desktop Protocol (RDP) service in order to not fall victim to credential theft or impersonation. To achieve this, there exist several measures in Windows. In this blog post, we’ll look at some of them, their benefits and their drawbacks.
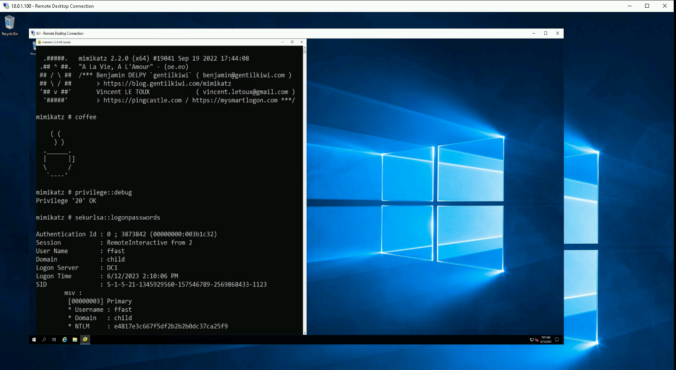
Sometimes, the good old credential dumping techniques just won’t work. This is the story of how a bad actor could dump credentials on a fully-patched, monitored and hardened workstation.
The anonymous data on our cases allows us to answer the question “What is a typical DFIR case at Compass Security?” and we conclude its the analysis, containment, eradication and recovery of one or a few devices in a Windows domain which is probably no surprise :)
Red Teaming exercises are getting popular with the growth of security operations centers. These attack simulations aim to help companies improve their defenses and train the blue team. But solid foundations are necessary to get the most of such an exercise.
© 2024 Compass Security Blog