What is a Hack-Lab?
Compass Security provides a monthly playful occasion for the security analysts to get-together and try to hack new devices, dive into current technologies and share their skills with their fellows.
 This also includes the improvement of internal tools, the research of newly identified publicly known attacks, and security analysis of hardware and software we consider useful for our future engagements.
This also includes the improvement of internal tools, the research of newly identified publicly known attacks, and security analysis of hardware and software we consider useful for our future engagements.


Topics
The following topics, tools and technology has been discussed during this Hack-Lab:
- SharePoint Security,
- Bypassing Android 7.0 HTTPS Apps Certificates Restriction,
- JWT4B,
- CodeInspect,
- Smart Meter,
- DNS Tunnel Debugging
Wrap-Up
Topic #1 – SharePoint Security Lab and Knowledge Sharing
SharePoint is a very popular browser-based collaboration and content management platform. Due to its high complexity, proprietary technology and confusing terminology it is often perceived as a black-box that IT and security professionals do not feel very comfortable with.
In a combination of talks and hands-on workshop sessions, Thomas Röthlisberger shared his research work with colleagues. They challenged his findings and shared their thoughts on pros & cons of security relevant settings. The outcome of this Hack-Lab session will be shared in a series of blog posts within the next couple of weeks.

The research in our very own hands-on SharePoint lab allows us to gain an in-depth understanding of any type of SharePoint environment, be it a purely internal collaboration web application, a platform to share information with external partners or a publishing site hosting the company website. To build or assess a secure SharePoint environment one needs to understand the importance of governance, logical and physical architecture, network topology, active directory considerations, authentication and authorization, segregation of classified data, hardening and most importantly web security relevant settings to make sure the built-in protection measures are effective. Like other modern Microsoft products, an out-of-the-box SharePoint installation can be considered secure. However, there are so many weirdly named settings which heavily depend on each other that misconfiguration is likely to happen, leaving the door wide open for unauthorized access by adversaries with SharePoint skills.
TECHNOLOGY:
- SharePoint Server 2010 & 2013
- Web Applications, Site Collections, (Sub-)Sites, (Custom) Lists, Document Libraries, Web Part Pages, Web Parts, Apps
- Web Security, Cross-site Scripting (XSS), Cross-site Request Forgery (CSRF)
- Navigation Links
- Web Sensitive Files, permission to Add & Customize Pages and Scriptable Web Parts, e.g. Content Editor and Script Editor (“SafeAgainstScript=False”)
- Browser File Handling
- Web Page Security Validation (aka Anti-CSRF token)
- Lockdown Mode Feature
- Remote Interfaces SOAP, CSOM, WCF Service, REST Interface
- Server-Side Controls
- .NET Sandboxing, Sandboxed Solutions and Apps
- Self-Service Site Creation
- Developer Dashboard
- Audit Logs
- People Picker
Topic #2 – Bypassing Android 7.0 HTTPS Apps Certificates Restriction
With Android 7.0, apps do not trust user imported certificates anymore. Intercepting app network traffic with a proxy has become more complicated.
The goal is to find or create a custom application which is explicitly developed for Android 7.0. Then to configure the app with the network_security_config.xml file, which is used to bypass this restriction, and therefore enables user defined certificates.
Technology:
- Android Studio
- Android 7.0
- Apktool
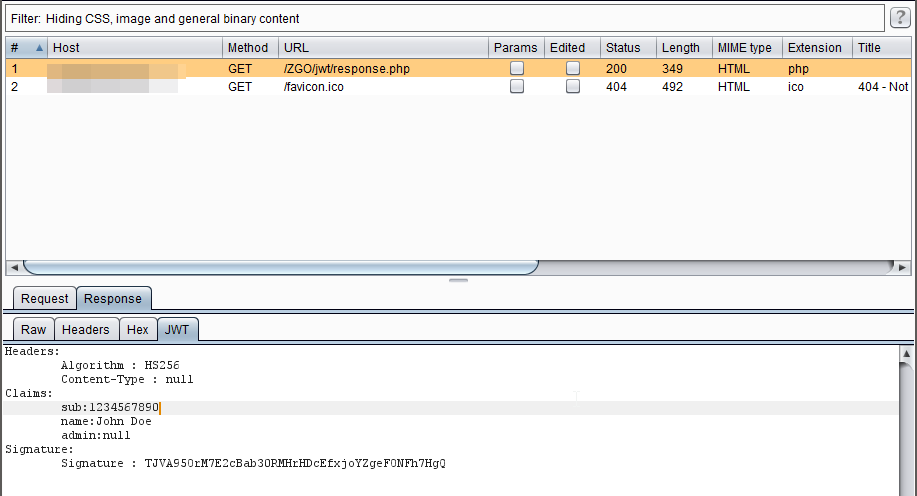
Topic #3 – JWT4B
Create a Burp plugin which helps the analyst when testing an app that uses JSON Web Tokens (JWT.IO).
Frist step is to create a prototype which enables Burp to visualize the tokens. On further hacklabs it should be possible to automatically perform JWT attacks.
Technology:
- Java
- JJWT (library)
- JWT
Topic #4 – CodeInspect
Evaluation of CodeInspect’s features.
Determine if CodeInspect could be used to make future Android app analysis assessments more efficient.
Technology:
- Java
- Android
Topic #5 – Smart Meter
Description:
An Energy Monitoring System was provided for testing. It is used to measure the current consumption and provides various interfaces. Web browser (TCP/IP) and Modbus are the main ones.
Assess the security of the interfaces. What can an attacker exploit if given network access to the device?
Technology:
- TCP/IP
- Modbus
- HTTP Web Application
Topic #6 – DNS Tunnel Debugging
Compass Security has its own trojan toolkit which we use for responsible phishing attacks in mandate for our customers, and also demos and proof of concepts. The trojan also implements DNS tunneling.
Analyze the source code and perform debugging to identify and fix some reliability issues while performing DNS tunneling with multiple clients.
Technology:
- C++
Leave a Reply