As penetration testers, our main goal is to identify as many vulnerabilities as possible. This allows our customers to more objectifly assess their security level and to shut as many doors as possible which an intruder could use to break in. This process needs to be based in respect of cost-benefit, depending on risk probabily and impact. Exploitation is only a secondary objective, mostly used to facility the first one. Also – the fix for most software vulnerabilities is the same: Always update all your software everywhere as soon as possible.
In my spare time, I like to get low-level and study the art of exploitation. From time to time I try to shed some light on the dark art of exploitation, by giving a little presentation to my work colleagues about my findings.
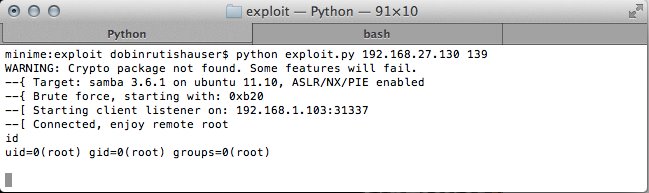
In my presentation I talk about CVE-2012-1182 (“root” credential remote code execution in Samba). First I show a small analysis of the vulnerability itself. After that I outline the inner workings of the Samba heap allocator. Based on this knowledge, I describe how to develop a working exploit which circumvents typical anti-exploitation securiy features like NX, ASLR and PIE.
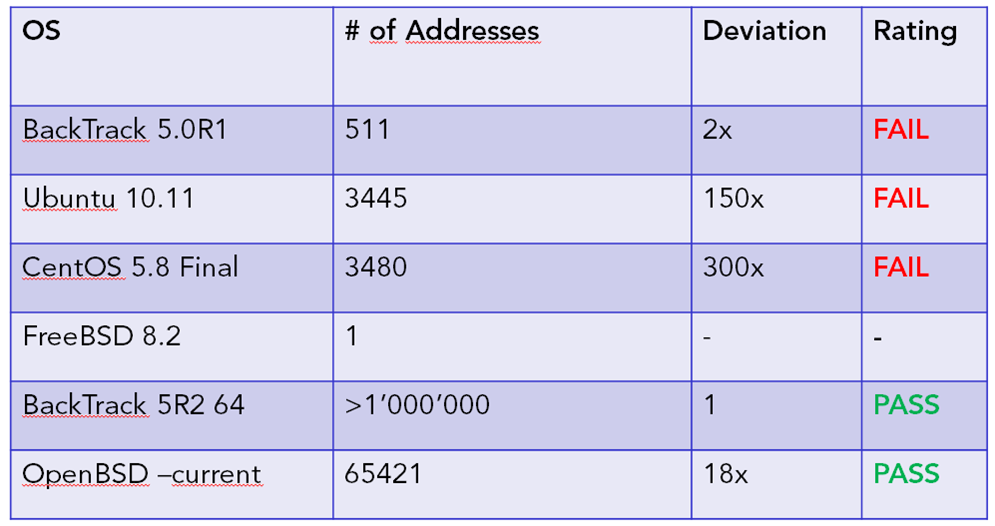
I close the presentation with a short analysis of the randomness of libc function addresses of common linux distributions. To summarize, ASLR/PIE implementations in 32 bit Linux distributions do not provide adequate randomness against brute forcing of ret2libc function addresses, as they provide less than 12 bit of entropy. OpenBSD-32bit provides 16 bit, and 64 bit linux distributions more than 20 bit of entropy, which considerably slows brute-force exploiting attempts.
Here are the results of my short evaluation. I generated around 1 million processes, each printing the address of system(), collected them in a file and did some analysis. In the following table, the second row shows the number of unique addresses collected. The third row shows how many times the most common address is being used, in respect to the least common.
It is not really a problem to brute force around <2000 addresses in a suitable timeframe, so the 32 Bit Linux distributions receive a FAIL rating. OpenBSD does a much better job on randomizing LIBC function addresses (as expected). 64 Bit operating systems are the hardest to brute force.
More details in my presentation: sambaexploit_v1.0.pdf
Leave a Reply