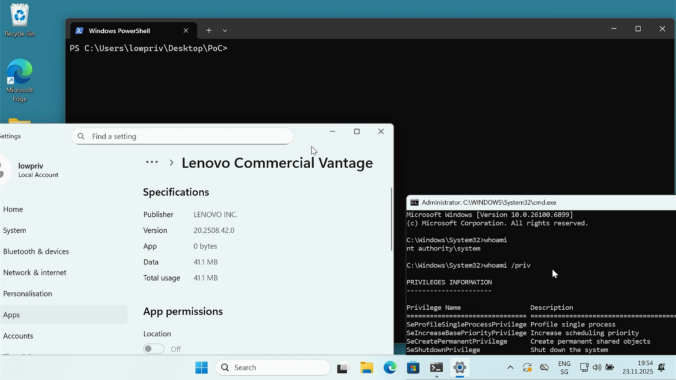
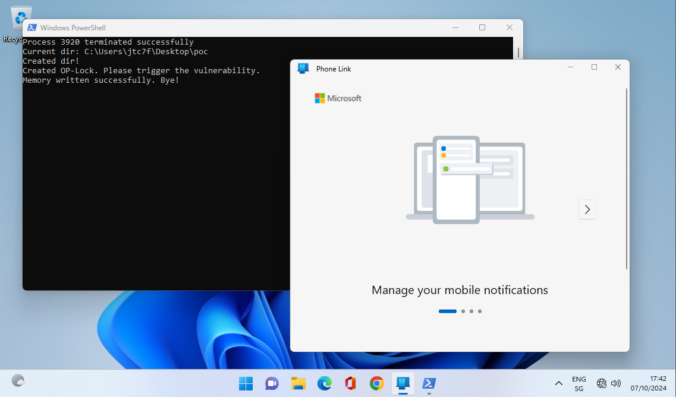
Last year we wrote about a Windows 11 vulnerability that allowed a regular user to gain administrative privileges. Not long after, Manuel Kiesel from Cyllective AG reached out to us after stumbling across a seemingly similar issue while investigating the Lenovo Vantage application. It turns out that the exploit primitive for arbitrary file deletion to gain SYSTEM privileges no longer works on current Windows machines.
Compass Security Blog
Offensive Defense
As a pentester you are sometimes thrown into projects where you have no idea where you are going to end up. This project was one of those where you were given a customer laptop and the aim was to “find something interesting”, perhaps a misconfiguration on the customer side. The problem was that the laptop […]
This blog post introduces our new custom queries for BloodHound Community Edition (CE) and explains how you can use them effectively to analyze your Active Directory infrastructure. TL;DR: Check out our new BloodHound CE custom queries! Active Directory and BloodHound The majority of our customers run a Microsoft Active Directory infrastructure, either exclusively on-prem or […]
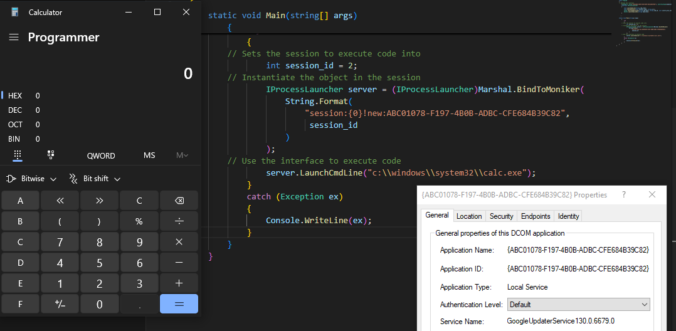
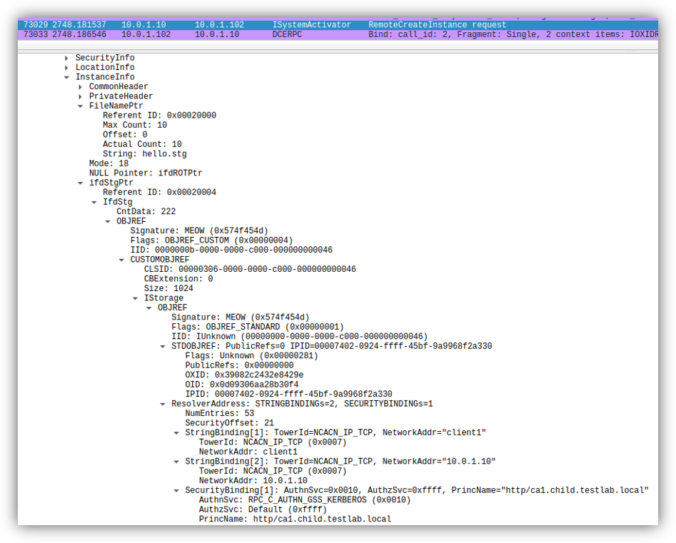
Once again, reading blogs and tweets from James Forshaw led me to wonder how things work. This time, I was working on DCOM for my last blog post and while reading about cross-session activation, I had trouble believing what I was reading.
Earlier this year, several security researchers published research about using DCOM to coerce Windows systems to authenticate to other systems. This can be misused to relay the authentication to NTLM or Kerberos, to AD CS over HTTP for instance. This sounds like a hot and complex topic. Let’s take a look back how this started […]
With the rise of remote working, Microsoft Teams has become the de-facto standard for video conferences, chat, and collaboration. The nature of the Teams architecture are some central systems that route information between parties. With that comes that Teams client software must be allowed to communicate to the Internet. Microsoft even recommends letting Teams traffic bypass inspection proxies for compatibility reasons. Its network communication pattern has significant overlap with malicious C2 traffic und thus it is nearly impossible for blue teams to spot adversary communication. Therefore, Teams is an interesting candidate to be abuses for C2 traffic. Thus, we put some research into this.
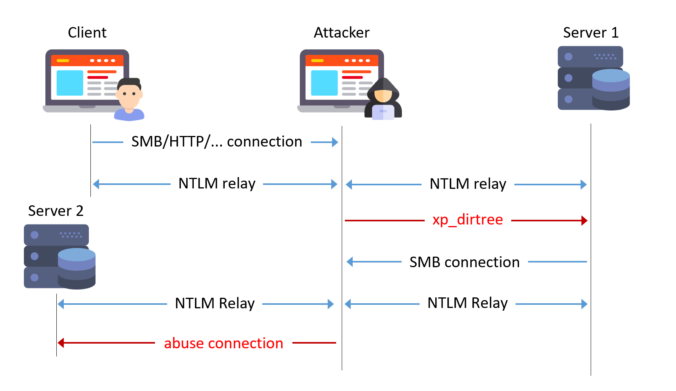
Readers of this blog probably know that I like to try NTLM relaying over all protocols possible! Relaying to Microsoft SQL (MSSQL) is known to work when using the default weak configuration.
With this blog post, we show some dangerous configurations and release a small tool to automate NTLM relaying in these cases.
A journey into the discovery of privilege escalation vulnerabilities in the Lenovo Update process.
When accessing a remote server, one should always assume it has been compromised or might be in the near future. It is particularly crucial for users with administrative privileges to establish a secure connection to the Remote Desktop Protocol (RDP) service in order to not fall victim to credential theft or impersonation. To achieve this, there exist several measures in Windows. In this blog post, we’ll look at some of them, their benefits and their drawbacks.
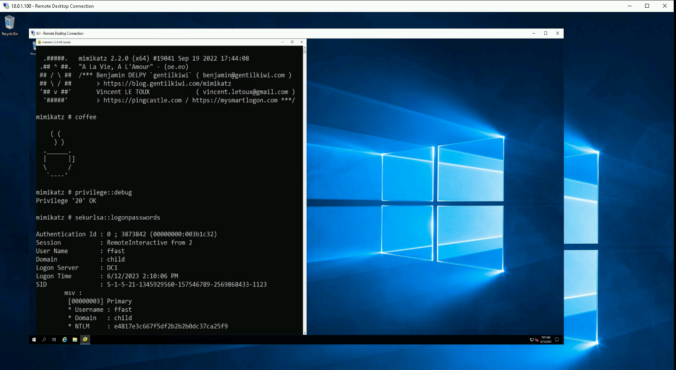
Sometimes, the good old credential dumping techniques just won’t work. This is the story of how a bad actor could dump credentials on a fully-patched, monitored and hardened workstation.
© 2026 Compass Security Blog