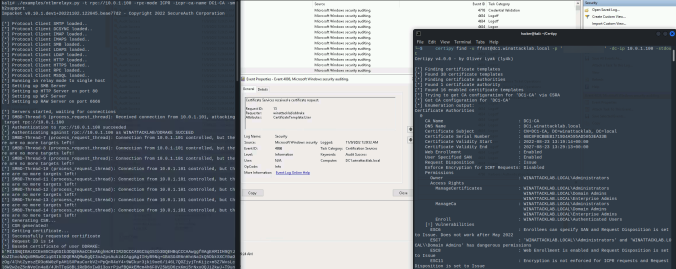
In June last year, the good folks at SpecterOps dropped awesome research on Active Directory Certificate Services (AD CS) misconfigurations. Since then, we find and report these critical vulnerabilities at our customers regularly. One of these new attack path is relaying NTLM authentication to unprotected HTTP endpoints. This allows an attacker to get a valid […]
Compass Security Blog
Offensive Defense
Page 2 of 4
Passwordless products promise greater security and convenience by allowing users to log in to Windows systems with only their smartphone. But what is going on behind the scenes and how could a domain’s security stance be worsened by such a solution? In this post I will explain how these products are implemented and detail the vulnerabilities and weaknesses discovered in three tested products.
BloodHound is the way to go to for finding attack paths in an Active Directory (AD) environment. However, it is not always clear how the data is gathered without looking at the code of SharpHound, the data ingestor for BloodHound. Microsoft hardened their systems over time through updates, which makes enumeration of Active Directory (AD) […]
BloodHound is the way to go to for finding attack paths in an Active Directory (AD) environment. However, it is not always clear how the data is gathered without looking at the code of SharpHound, the data ingestor for BloodHound. Microsoft hardened their systems over time through updates, which makes enumeration of Active Directory (AD) […]
BloodHound is the way to go to for finding attack paths in an Active Directory (AD) environment. However, it is not always clear how the data is gathered without looking at the code of SharpHound, the data ingestor for BloodHound. Microsoft hardened their systems over time through updates, which makes enumeration of Active Directory (AD) […]
A little bit over a year ago, I wrote an article on this blog about CVE-2020-1113 and how it enabled to execute code on a remote machine through relaying NTLM authentication over RPC triggering a scheduled task on the remote system. History repeats itself and a vulnerability of the same category has been fixed by Microsoft in June this year.
Due to recent developments we figured it would be great to contribute a cheat sheet and create security best-practices on how to tie down a Microsoft on-prem environment. Our work mostly relies on MS recommendations. However, we put some effort to really condense it to the essence. We hope to see this applied everywhere and thus open-sourced everything in our GitHub repository.
The article discusses the very basics to keep systems ready for analysis of lateral movement. We present some guidelines in form of a cheat sheet and a tool (Readinizer) that you can run, to ensure that everything is set up as in the guidelines provided.
During internal assessments in Windows environments, we use BloodHound more and more to gather a comprehensive view of the permissions granted to the different Active Directory objects. In this post, we’ll show an advanced usage of this tool by using our additional queries.
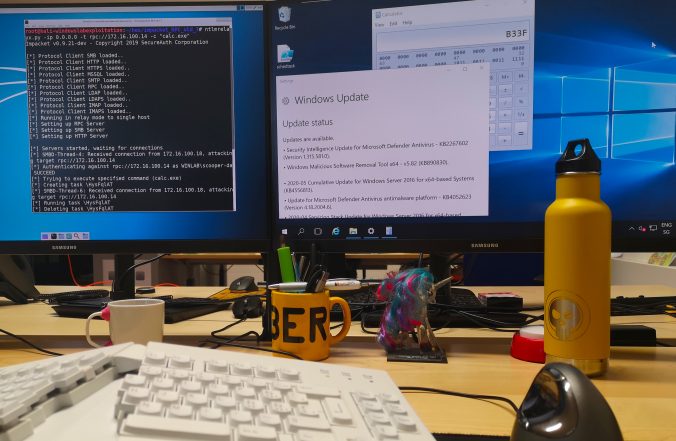
Since a few years, we – as pentesters – (and probably bad guys as well) make use of NTLM relaying a lot for privilege escalation in Windows networks.
In this article, we propose adding support for the RPC protocol to the already great ntlmrelayx from impacket and explore the new ways of compromise that it offers.
This vulnerability was discovered by Compass Security in January 2020, disclosed to Microsoft Security Response Center and assigned CVE-2020-1113 as identifier.
© 2026 Compass Security Blog