The article discusses the very basics to keep systems ready for analysis of lateral movement. We present some guidelines in form of a cheat sheet and a tool (Readinizer) that you can run, to ensure that everything is set up as in the guidelines provided.
Compass Security Blog
Offensive Defense
Page 10 of 29
During internal assessments in Windows environments, we use BloodHound more and more to gather a comprehensive view of the permissions granted to the different Active Directory objects. In this post, we’ll show an advanced usage of this tool by using our additional queries.
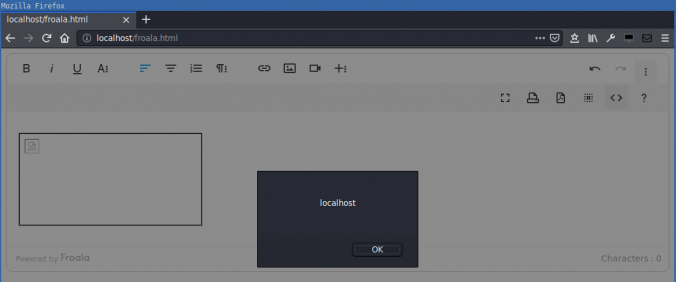
Compass found a DOM-based cross-site scripting (XSS) in the Froala WYSIWYG HTML Editor. HTML code in the editor is not correctly sanitized when inserted into the DOM. This allows an attacker that can control the editor content to execute arbitrary JavaScript in the context of the victim’s session.
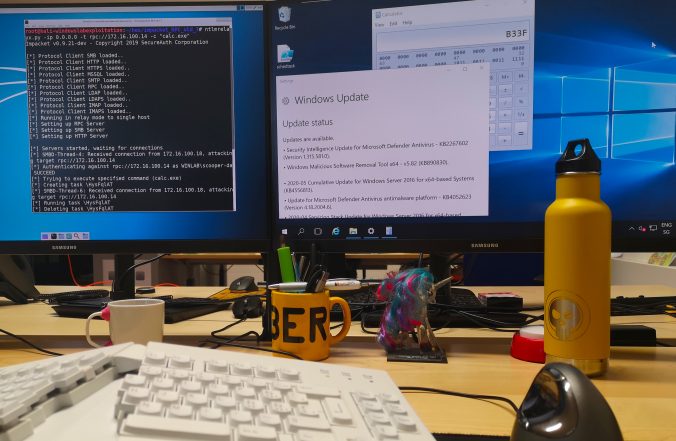
Since a few years, we – as pentesters – (and probably bad guys as well) make use of NTLM relaying a lot for privilege escalation in Windows networks.
In this article, we propose adding support for the RPC protocol to the already great ntlmrelayx from impacket and explore the new ways of compromise that it offers.
This vulnerability was discovered by Compass Security in January 2020, disclosed to Microsoft Security Response Center and assigned CVE-2020-1113 as identifier.
In this blog post we will reverse engineer a sample which acts as downloader for malware (aka a “dropper”). It is not uncommon to find such a downloader during DFIR engagements so we decided to take a look at it. The sample that we are going to analyze has been obtained from abuse.ch and was […]
A new vulnerability (CVE-2020-0796) affecting SMBv3 has been discovered. The community has started to name this vulnerability SMBGhost because everyone knows this vulnerability is present but no additional details are available. Microsoft also released the advisory ADV200005. [1]
When you add a new computer, it must first join the domain. If you use its future main user to do it, they’ll become the owner and be able to hijack the computer to become a local administrator in four easy steps.
Sometimes, it doesn’t take much for a good scam: a good story, a little persuasion, then disappear again… and sometimes, the scammers come up with tactics that come straight out of the textbook.
A write-up of the OWASP Toronto January talk which mainly focused on the correlation and integration of results generated by automated tools in application security such as SAST, DAST and SCA. Alexandre Larocque concludes whether old-fashioned PDF reports are still worth it.
“I love hacking can be used for the greater good.” During the Solothurn Film Festival 2020 we had the opportunity to meet Jim McKay, who directed, among others, two episodes for Mr. Robot season one. Jim had also time for a short interview. What is important for you working as a director/writer? Jim McKay: I […]
© 2026 Compass Security Blog