What is a Hack-Lab?
Compass Security provides a monthly playful occasion for the security analysts to get-together and try to hack new devices, dive into current technologies and share their skills with their fellows.
This also includes the improvement of internal tools, the research of newly identified publicly known attacks, and security analysis of hardware and software we consider useful for our future engagements. This hack-lab took place in our office in Bern.
Topics
The following topics, tools and technology has been discussed during this Hack-Lab:
- Threat Modeling and Security Concept session,
- CMS Assessment,
- JWT4B development,
- GnuRadio door bell analysis,
- Windows Share Enumeration Tool,
- Exploit.courses testing and training
Wrap-Up
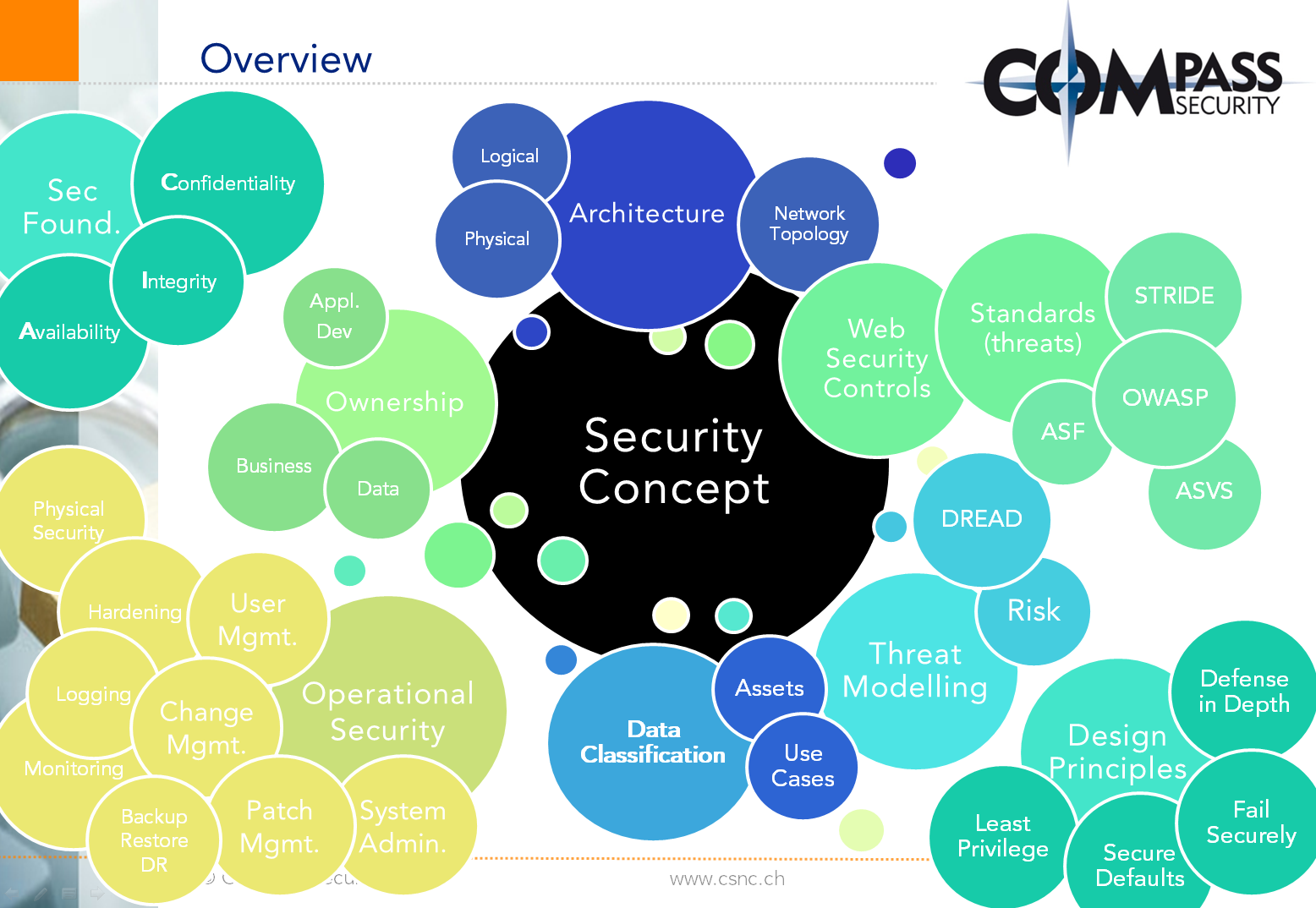
Topic #1 -Threat Modeling and Security Concept session
In a combination of talks and hands-on workshop sessions, Thomas Röthlisberger shared his knowledge about threat modeling and security concept creation and analysis with colleagues.
Information Security fundamentals:
- Security Foundations – CIA
- Security Design Principles
- Threat Modeling and Standards
Security Concepts:
- Ownership and Data Classification
- Architecture and Network Topology
- Web Security Controls
- Operational Security
Topic #2 – CMS Assessment
Using different available security and hardening scanners, we try to asses the security of three CMS: Drupal, Joomla, WordPress.
The goal is to find new vulnerabilities and possible test cases. We refresh and update our Compass Knowledge and improve our tool-set for CMS security assessments.
Technology:
- Drupal
- WordPress
- Joomla
- Web Scanners written in Python
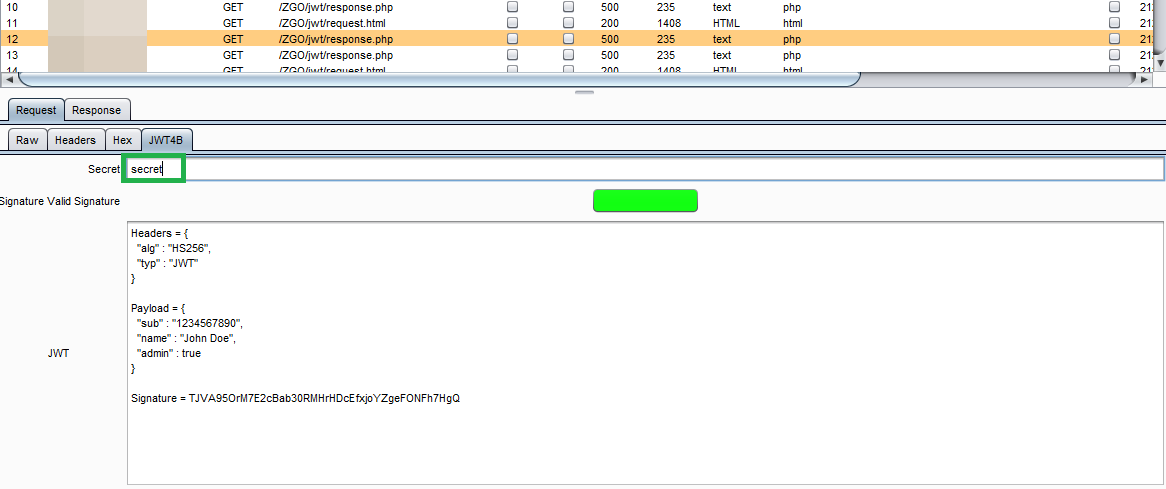
Topic #3 – JWT4B development
We create a Burp plugin which helps the analyst testing apps which uses JSON Web Tokens (jwt.io).
The first step, which we performed in the previous hacklab, was to create a basic prototype, which enables Burp to visualize the tokens. During this hacklab we increased the functionality, implemented signature checking and interception functionalities. It is possible to comfortable modify the JWT token content.
Here a screenshot of the signature-checking functionality. The correct key was provided by the tester, which was detected by JWT4B (green indicator):
Technology:
- Java
- JJWT (library)
- JWT
Topic #4 – GnuRadio door bell analysis
We analyzed a wireless door bell with the help of GnuRadio and HackRF One. We captured the ASK modulated signal, and stored it as digital bitstream in a file. Afterwards we could successfully replay the stored bitstream, making the door bell ring. The next step will include to further analyze the bitstream.
Technology:
- GNU Radio
- HackRF One SDR
- Kali Linux
Topic #5 – Windows Share Enumeration tool development
If a pentest is performed in a large environment, it is possible that hundreds of accessible Windows shares are available in the network. The goal is to create a tool, which supports us during our penetration tests. Our tool should display the following information for every share in the network:
- IP Address
- Hostname
- Share Name
- 20 top level files and directories
- ACLs for the top level files and directories
We managed to implement this tool by combining Linux Samba tools (smbclient, smbcalcs) in an advanced shellscript.
Technology:
- Windows, filesharing, network share
- ACL, Permissions
- masscan
- samba / smbclient / smbcacls
- Linux, Shell, Scripting
Topic #6 – Exploit.courses testing and training
Dobin Rutishauser teaches the “Exploiting & Defense” part of the Application- and Software-Security module at the Bern University of Applied Sciences (Berner Fachhochschule). For this assignment he created a website which provides writeups and challenges to be solved by the students. It also hosts dedicated per-user Linux container, accessible via JavaScript terminal. The Hack-Lab was used to check the website for usability problems, resistance against local DoS attacks, security problems and also basic functionality checks. We also performed a review of some of the writeups, where the team members solved several of the challenges. This includes the ARM buffer overflow challenge, and an extended version of the shellcode development challenge.
The team could identify several small bugs, some small mistakes in the writeups, and gave valuable usability improvement feedback.
Technology:
- qemu, LXC / LXD
- x86, x64 and ARM
- gdb, readelf and python
- AngularJS and go






Leave a Reply