Introduction
Last Friday and Saturday (15./16. June 2018), the 6th edition of the security conference Area41 (formerly Hashdays, https://area41.io/) organized by DEFCON Switzerland (https://www.defcon-switzerland.org/, https://twitter.com/defconCH) took place in Zürich. Every Compass security analyst can attend two conferences every year supported by Compass. So most of the analysts decided to go to the Area41 this year for watching the talks, taking part at the workshops and meet other people.
(Image source: https://twitter.com/c_APT_ure/status/1007556784142389248)
This wrap up contains some notes I took during the conference for things I consider interesting. Also check out the Twitter Hashtag #area41 (https://twitter.com/hashtag/AREA41) for more impressions!
Area41: Badge
Like in the previous years, the Area41 team created a very nice badge. The badge has a ESP8266 chip with WiFi and a display on it. You can configure your badge by creating a WiFi connection to it and then enter your username in a web interface. There are some apps installed for showing your nickname on the LCD, viewing the Area41 schedule, scan for WiFi and more. You can find Easter eggs by pressing the buttons on the badge in specific orders. There is a description on the Area41 page: http://area41.io/badge/. The source code is available on GitHub: https://github.com/le-krogoth/proteus. Some details were revealed at the closing ceremony.
It was even possible to play a sound from the badge by soldering a headphone to the RX pin:
(Image source: https://twitter.com/ozzi_____/status/1008088450778697729)
Area41: Recordings
All recorded talks are already available on the DEFCON Switzerland YouTube channel (https://www.youtube.com/user/defconswitzerland). A big thank to Cooper (https://twitter.com/ministraitor) for making this possible!
Talk: Keynote
- Speaker: Costin Raiu (@craiu)
- Recording: https://www.youtube.com/watch?v=jeLd-gw2bWo
Sometimes, it’s not very clear who is behind an attack. Even if someone takes credit for an attack, maybe this person is not telling the truth. A malware can be compared to other malware samples in order to see if there are similarities. For example, Google could link the WannaCry ransomware to the Lazarus group because two malware samples had the same binary code inside.
There is a software called Yara (https://virustotal.github.io/yara/) which can be used for finding similar code inside a list of samples.
(Image source: https://twitter.com/lupig69/status/1007571805589172224)
Talk: Chrome & WebRTC -eq Problems
- Speaker: Amit Dori (https://twitter.com/_AmitDori_)
- Recording: https://www.youtube.com/watch?v=-k39x-tUekc
If you already exploited a system and you want to download more data to the victim’s machine or exfiltrate data, you want to be as stealthy as possible. If your process tree looks suspicious, you may get detected by the blue team. After a short WebRTC introduction, Amit showed two example scenarios how you can use Google Chrome and WebRTC to achieve this.
If Chrome is started with the --use-fake-ui-for-media-stream parameter, the user is not asked when the webcam and microphone is tried to be accessed. By accessing an unsuspicious public WebRTC chat, the attacker can view and hear the victim.
The second scenario was used to download files to the victim’s machine also by using WebRTC features. To bypass the Same Origin Policy, the parameters --disable-web-security and --user-data-dir=c:\foo\bar were used.
To detect and mitigate such attacks, WebRTC should be disabled, UDP traffic should be monitored and also the parameters of the browser processes should be monitored. Usually, the browser is started without any parameters.
Talk: Monitoring MacOS For Malware And Intrusions
- Speaker: Daniel Roethlisberger (https://twitter.com/droethlisberger)
- Recording: https://www.youtube.com/watch?v=OSSkBgn_xJs
- Slides: https://asciinema.org/a/187361
Daniel developed and released a tool called xnumon. From the project page:
xnumon is a monitoring agent that produces system activity logs intended to be suitable for monitoring potentially large fleets of macOS systems for malware and intrusions. It aims at providing similar capabilities on macOS that sysmon provides on Windows.
The project page can be found on his website: https://www.roe.ch/xnumon. The code is available on GitHub: https://github.com/droe/xnumon.
Talk: Looking into the White Box
- Speaker: Pascal Junod (https://twitter.com/cryptopathe)
- Recording: https://www.youtube.com/watch?v=ygHJ2rM-ies
- Slides: https://crypto.junod.info/area41-2018_talk.pdf
Pascal explained the concept of white box cryptography. In the intro, he explained that in black box cryptography, the analyst only can use the algorithms, without having access to the private/secure key material. In grey-box security, side channel attacks could be used to extract secret keys or implementation details. In white box (WB) cryptography, the cryptographic algorithms are running in a environment which assumed to be hostile. The analyst or attacker has full control of the implementation and environment where the algorithms are running. This could be a mobile phone or workstation computer / laptop. WB cryptography should be resistant against key extraction. It’s not easy to achieve this goal. To make the attacker’s life harder, the Kerckhoff’s principle (the security should only depend on the key, the algorithm can be public) should be ignored. Of course, the security should not only depend on the obfuscation of the cryptographic algorithm, but “obscurity on top of security” will make the attacker’s life harder. There is a lot of research in this field, but all published designs have been broken so far.
Blame the badge, or how a conf badge had us exploring Xtensa exploitation (compared to ARM)
- Speakers: Carel van Rooyen (https://twitter.com/carelvanrooyen) and Philipp Promeuschel (https://twitter.com/nks0ne)
- Recording: https://www.youtube.com/watch?v=-YN9BIYdHCE
In this talk, Carel and our co-worker Philipp gave a quick overview over the Xtensa platform and of two implementations (ESP8266 and ESP32). This platform has several anti-exploitation techniques active. The debugging on these devices was done using qemu-esp32, esp-idf (https://github.com/espressif/esp-idf), radare2 (https://rada.re/), gdb combined in a tmux (https://github.com/tmux/tmux) session for a comfortable usage Because the stack is not executable, already existing code (called gadgets) have to be used. For this, pre-existing gadgets from the ESP boot ROM were used. In a demo, they showed how this can be used for exploitation.
Talk: Red Team: Stories from the Trenches
- Speakers: Stefan Friedli (https://twitter.com/stfn42) & Michael Schneider
- Recording: https://www.youtube.com/watch?v=UQhgPfRJyXM
Stefan and Michael from scip AG explained the audience that the “classical” penetration test is dead. Nowadays, customers use many solutions for their services which are hosted at 3rd party providers. This means the external internet facing IT infrastructure of a company is shrinking and is therefore not that important anymore. It does also not make very much sense to pay a pentest company 5000 bucks for a simple Nessus scan against the external infrastructure. This money could be saved and invested for training the own employees doing the same task. However, in the end, it’s always possible to gain access to the internal company network. The question is not if it’s possible to break in – but only when. Therefore, it’s important to test the important stuff in the internal network.
There are a lot of techniques for owning a Windows network. Wmiexec from the Impacket tool suite (GitHub: https://github.com/CoreSecurity/impacket) can be used to invoke Mimikatz (https://github.com/gentilkiwi/mimikatz) on several systems to collect user credentials. To be more stealthy, Invoke-Mimikatz from the PowerSploit tool suite (GitHub: https://github.com/PowerShellMafia/PowerSploit) can be used. This will execute Mimikatz in the memory without writing anything to the filesystem. This can be used to bypass antivirus solutions. The Responder.py (GitHub: https://github.com/SpiderLabs/Responder) tool can be used to collect NetNTLM hashes within the network. For this, the victims have to connect to your Responder.py machine. This can be achieved by putting a SCF file in a Windows share (see here for more details on this attack: https://pentestlab.blog/2017/12/13/smb-share-scf-file-attacks/). Even if the company has 2FA deployed for the Windows login, there may be other services that uses the same credentials but without a 2nd factor. Kerberoasting can be used to obtain a kerberos ticket for a domain service. The password of the service in the ticket of this user can the be cracked offline. To gain domain admin privileges is a bit overrated. Even normal domain user accounts have access to sensitive files.
Michael published some PowerShell tools they use in their engagements on GitHub: https://github.com/scipag/PowerShellUtilities.
(Image source: https://twitter.com/al_maisan/status/1007619294224633861)
Talk: On the Security of Dockless Bike Sharing Services
- Speaker: Antoine Neuenschwander (https://twitter.com/ant0inet)
- Slides: https://www.slideshare.net/AntoineNeuenschwande/on-the-security-of-dockless-bike-sharing-services
- Recording: https://www.youtube.com/watch?v=KKlCLsU4v7o
Antoine analyzed the security of the two bike sharing services Smide and oBike.
Every Smide bike has a GPS chip and a GSM module built in. The bike communicates via GSM with a REST service of Smide. There is a mobile app which also communicates with this service. The mobile app can be used to book a bike. The bike will then be unlocked remotely by the Smide REST service. A user can lock the bike during the booking period (e.g. for making a break). For this, also a REST service is called to lock the bike. The built-in motor of the bike will automatically block. The bike can then not be moved anymore. Antoine discovered, that the booking ID can be changed to a booking ID that is not assigned to the correct user. Using this authorization vulnerability, it’s possible to block the motor of bikes while they are used. This is a serious vulnerability, because other people on the bike could get hurt when the bike stops while they are driving. This bug was fixed within 4 day and Antoine got 100 free minutes on the bike :-).
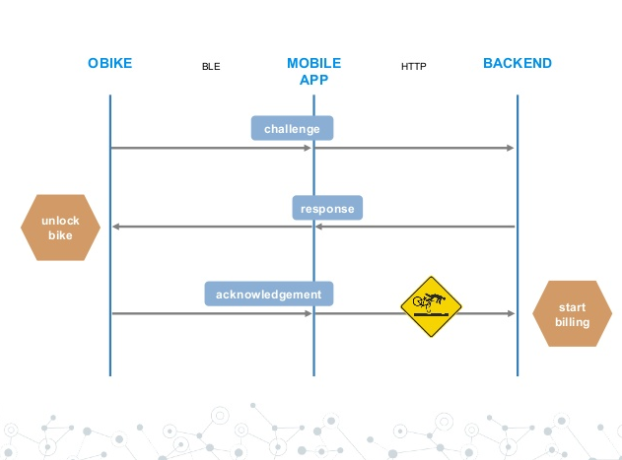
The oBike system works a bit different: The mobile app is the only part communicating with a REST service. The communication to the bike is done over Bluetooth Low Energy (BLE). If a bike ride is finished, the mobile app will tell the REST service where bike is located now. These location values can be set to arbitrary values by just modifying the HTTP request to the REST service. Antoine also analyzed the BLE communication between the mobile app and the bike lock. The message from the lock are signed using AES CBC-MAC. The whole security of the system is based on the used shared keys. For opening the lock, the lock sends a challenge to the backend (via the mobile app) and if the bike gets a properly signed message back from the backend, the bike is unlocked. Then, an acknowledge message is sent to the backend. After the backend receives this message, the billing process starts. Therein lies the problem: If this message is simply dropped, the bike is in an unlocked stage but the billing process has not started yet. Additionally, in the backend, the bike is marked as “broken”. oBike fixed some issued by encrypting and signing the calls to the REST interface. These keys can easily be extracted from a shared library within the mobile app.
The bike lock is open before the billing starts. (Image source: Antoines slides)
You can find more details on the GitHub project page here: https://github.com/antoinet/obike.
Talk: Modern pentest tricks for faster, wider, greater engagements
- Speaker: Thomas Debize
- Recording: https://www.youtube.com/watch?v=payapqmFATk
Thomas showed us what tools he uses during his pentest engagements. Nowadays, it’s possible to gain a lot of data by scanning the internet for yourself using masscan (https://github.com/robertdavidgraham/masscan), zmap (https://zmap.io/) and also by using 3rd party services like Shodan (https://www.shodan.io/), Censys (https://censys.io/), Scans.io (https://scans.io/) or the Chinese pendant Zoomeye (https://www.zoomeye.org/). Recon-ng (https://bitbucket.org/LaNMaSteR53/recon-ng) can be used to automatically use the API of such services in a neat framework.
To manage a huge amount of gathered data, these can be stored in simple CSV files. To manage these CSV files afterwards, the tool csvkit (https://csvkit.readthedocs.io/en/1.0.3/) can be used. This tool allows it to create statistics over CSV files or use them as a SQL-like database for joining multiple files together and querying for useful information. Because Excel is limited to 1M rows, Thomas uses the Dataiku web application (https://www.dataiku.com/) for analyzing the data.
For executing tools in parallel, GNU parallel (https://www.gnu.org/software/parallel/) can be used for this. The following command queries a domain for subdomains in parallel:
$ parallel -a subdomains.txt –joblog job.log –progress -bar "dig +noall +answer {}.example.net"
Sometimes, a specific task cannot be done in Python, because there is no library which implements the needed features. Instead of writing Java code, Jython (http://www.jython.org/), can be used to write Java code inside Python. So you can combine the Python libraries you usually use with Java code which performs specific tasks.
Frida can be used for the dynamic analysis of applications. You can write JavaScript code that is injected into the running processes to instrument, modify and inspect your desktop or mobile apps.
If you want to run Python code on a Windows machine, a Python environment has to be available. In pentest engagements on compromised Windows hosts, this is not often the case. Also antivirus software could detect common Python attack tools. A Python script can be compiled into a Windows or Linux binary using PyInstaller (https://www.pyinstaller.org/) including all needed libraries into one single executable. This allows the execution of Python code on a Windows host without having Python installed. It’s also possible to encrypt the binary in order to bypass the antivirus signature matching engine.
For searching through source code, sift can perform advanced search operations. The performance is better than using grep and it also offers more options. For example, the –git parameter can be used in order to avoid searching through the .git/ directory of a repository.
You can check out the GitHub repositories of Thomas for more tools mentioned during his presentation: https://github.com/maaaaz.
Talk: Lazy ways to own networks
- Speaker: Nicolas Heiniger (https://twitter.com/nicolasheiniger)
- Slides: https://photochrome.ch/uploaded/2018-06-16_area41_lazy-ways-to-own-networks.pdf
- Recording: https://www.youtube.com/watch?v=aeDnoa4cpO0
Our colleague Nicolas shows some examples that owning a network is often relatively easy:
- Phishing: You can get credentials or internal network access by sending a Phishing mail to the employees of a company. Even if 2FA is generally used, not all publicly available applications ask for the 2nd
- Unpatched Systems: Often, you can get a quick and easy win if you search for unpatched systems. Seeing systems with the EternalBlue (MS17-010) vulnerability is not uncommon. There is an Nmap (https://nmap.org/) script which is already included in Nmap that let’s you search for this vulnerability:
# nmap -n -Pn -p 445 -sC --script smb-vuln-ms17-010 -iL targets.txt -oA nmap_eternalblue
These systems can be exploited very easy using Metasploit (https://github.com/rapid7/metasploit-framework). If you are on the machine, you can use Mimikatz (https://github.com/gentilkiwi/mimikatz) to gather the credentials and hashes of the logged in users.
- Default Credentials: A lot of internal systems still use default credentials like admin/admin. A typical example is a Tomcat server running as SYSTEM, which let’s you deploy arbitrary WAR files. Metasploit (https://github.com/rapid7/metasploit-framework) can generate WAR files that will open a reverse shell to the analyst’s machine.
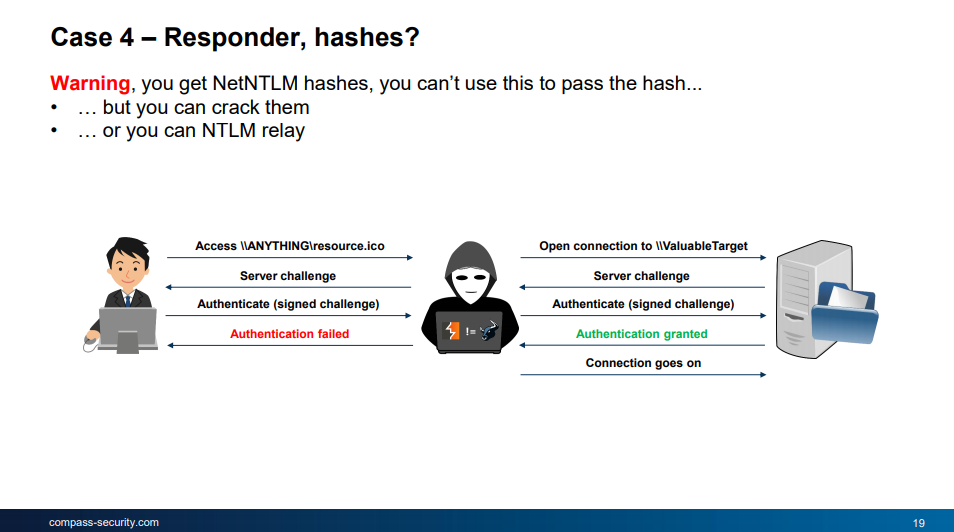
- Responder: The Responder tool (https://github.com/SpiderLabs/Responder) can be used to collect NetNTLM hashes in the network. To get as many hashes as possible, an SCF file can be put on a Windows share which then triggers the clients, forcing them to connect to the analyst’s machine, which reveals their hashes. Either you try to crack these hashes or you use them with MultiRelay.py (https://github.com/lgandx/Responder/blob/master/tools/MultiRelay.py) for performing an NTLM relay attack. This is a very powerful attack that let’s you authenticate to another machine with the privileges of the attacked user that sends the hash to you. This can be mitigated by enable SMB signing.
NTLM Relaying (Image source: Nicolas slides)
- Modern Dumpster Diving: A regular domain user usually has access to lots of shares. Very often, credentials of domain users, local admins or service users are laying around in scripts or configuration files. Backup files of servers can be used to extract the stored NTLM hashes. These are treated like passwords, meaning you can directly use them to authenticate you on a system by performing the so called pass-the-hash attack.
- Boot from USB: If you have physical access to a company’s computer, you should definitively try to boot from USB. Either you replace the utilman.exe file with cmd.exe, which allows you to open a command prompt as SYSTEM by pressing Windows+U on the login screen, or you extract again the NTLM hashes and use them for the pass-the-hash attack in order to jump on other workstations in the network.
- Custom Tools/Scripts: Finding tools like self-developed “RunAdm.exe” which launches a process as local admin is not uncommon. They can be used to run arbitrary code as local admin. Companies try to make it harder and harder for us to abuse them, but this is always possible. Either the custom command can be specified, the password can be extracted out of the binary by using a decompiler (https://www.jetbrains.com/decompiler/) or read by monitoring the Windows API calls directly (http://www.rohitab.com/apimonitor). Such tools should never be used.
- Credential Reuse: The already explained pass-the-hash attack can be performed against every host in the network which has the password configured. The tool CrackMapExec (https://github.com/byt3bl33d3r/CrackMapExec/) can be used to launch such an attack over the whole corporate network by using one single command. CrackMapExec can then also automatically dump NTLM hashes of other workstations or launch mimikatz to gain access to the users’ credentials. To mitigate this, local users should have a random and unique password configured on every host in the network. Microsoft LAPS (Local Administrator Password Solution, https://www.microsoft.com/en-us/download/details.aspx?id=46899) can be used for this.
- Bonus – Printer Trick: Modern printers offer an address book for the scan-to-mail feature. This is often connected to the Active Directory. It already happened several times on pentest engagements, where a domain admin was configured in the web interface of the printer. These credentials can be extracted by setting up an own LDAP server (or start Responder.py) , changing the server in the printer interface and searching for a contact in the AD on the printer. The password can the be retrieved on the analyst’s server.
Talk: Swimming IoT or how to hack a vessel
- Speaker: Stephan Gerling (https://twitter.com/ObiWan666)
- Recording: https://www.youtube.com/watch?v=GMWoS7v3qFo
Stephan showed in his talk that vessels these days have a lot of technology on board. These ships have autopilots, GPS, GSM, radar, engine control, entertainment systems, WiFi, VoIP and also Internet access included. The communication between the electronic devices of these ships is done over a bus system called NMEA. This bus system is also connected via a TCP/IP to NMEA gateway to the local network on the ship and also to the Internet. The “smart” ships can be controlled by mobile applications over the Internet.
The AIS (Automatic Identification System) periodically sends some statistic information (like a unique ID, navigation status, turn direction, speed, position, …) to remote systems via radio signals. These information can be viewed on online tools like Marinetraffic (https://www.marinetraffic.com). This information can also received using a SDR like HackRF. An SDR can also spoof fake information.
The routers on a yacht are built without much security in mind. There is a .NET application for configuring one of these routers. The application connects via FTP to the router and downloads an XML file. After a configuration change, the XML is changed and uploaded to the router again. The FTP credentials are hard coded in the app and the XML does also contain the WiFi password. The analyzed router does also have remote support and several open ports on the internet-facing interface. A Winbox Management software can be used to configure the routers remotely. The username/passwords are the same on every router and can be found in the .NET application source code. Such routers can be found on Shodan.
Other management interfaces of ships are available directly on the internet. One example showed that the authentication is only done on the client. Depending on the entered username, a different page is loaded. This is done on the client using JavaScript. Therefore, the authentication can be easily bypassed.
Shodan also has a ship tracking page that can be found here: https://shiptracker.shodan.io/.
Talk: Web Cryptominers in the .CH Zone
- Speaker: Antoine Neuenschwander (https://twitter.com/ant0inet)
- Recording: https://www.youtube.com/watch?v=WOH0u8kezLo
Antoine explained how a blockchain works and how this technique is used in crypto currencies. There are cryptocurrencies like Monero, that do not require ASICS or GPUs for mining. Instead, this is done on CPUs. Since this task can also be done within the browser using JavaScript. Antoine searched through all ~2M .ch domains (he works at Switch, so he has access to all .ch domains) and analyzed how many such miners are installed. In May 2018, 116 miners were detected out of 1.2M .ch domains. One destination Monero address was used 14 times. A Shodan search showed, that this address was used over 500 times over the world. If the user is not informed about the mining process, the site is considered as malicious and blocked.
Talk: Fuzzing For Worms
- Speaker: Dobin Rutishauser (@dobinrutis)
- Slides: https://docs.google.com/presentation/d/1tLELphbkh2bVLyIedagNoFKBn_DEYv29RskZY4u-szA/edit?usp=sharing
- Recording: https://www.youtube.com/watch?v=akpk9hrizc4
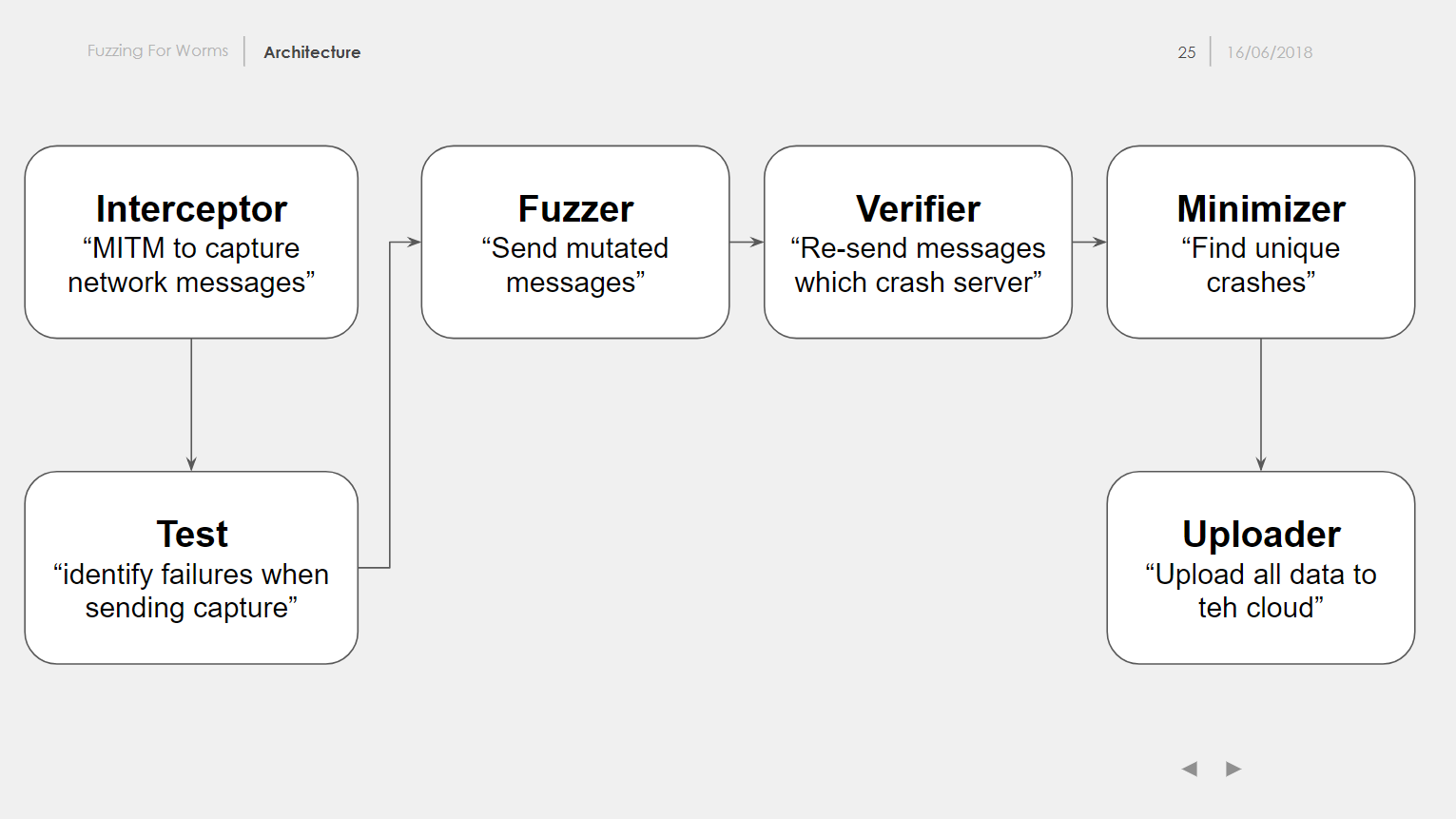
Our colleague Dobin wrote a software called ffw (Fuzzing For Worms, https://github.com/dobin/ffw) which can be used for fuzzing network servers, because AFL (American Fuzzy Lop, http://lcamtuf.coredump.cx/afl/) is not ideal for this task. To use ffw, legit network traffic has to be intercepted first. After that, the traffic data is changed using radamsa (https://gitlab.com/akihe/radamsa) and then sent to the server again. If the server crashes, there might be a bug in the server. This payload can be re-sent to verify and reproduce the crash. To analyze the crash, the stack trace is needed to locate the function where the server crashes. For this, the server is started again in GDB and the stack trace is written to a file and parsed by ffw.
ffw architecture (Image source: Dobin’s slides)
To get a high code coverage, ffw should also support feedback-driven fuzzing. For this, HonggFuzz (https://github.com/google/honggfuzz) was integrated into ffw. HonggFuzz can tell ffw if a new basic block in the code was reached.
Ffw does not need a lot of computing power, because most of the bugs were found within the first minutes after launching the fuzzer. To improve the performance, parallel fuzzing was implemented. For this every process is created within a new network namespace, so the same port number can be used multiple times.
Dobin found several bugs in Mongoose MQTT, libcoap, libiec, vnc4server or libmodbus using ffw. Ffw does not need a lot of configuration or patching the target application and can be used very quickly. However, it is not as fast as AFL, but low hanging fruits can be earned rather quick in contrast for setting up AFL.
Check out the ffw GitHub repo (https://github.com/dobin/ffw) and Dobin’s blog (https://www.dobin.ch/blog/) for more infos about ffw.
Workshop: UploadScanner – Filing Fiddly Files
Tobias Ospelt (https://twitter.com/floyd_ch) from modzero developed a Burp Suite extension (the pro version is needed) which can be used for testing the file upload functionality of web applications. In the workshop, he showed how file uploads work and how these can be tested by using this new extension. The extension uploads various filetypes to the application and tests if it can be downloaded again and if it changed. Predefined payloads exist for testing various code injection, XXE or SSRF vulnerabilities.
The extension looks really cool and supports an analyst massively in testing file uploads.
Tobias will release the Extension soon on GitHub (https://github.com/modzero/mod0BurpUploadScanner). You should definitively try it out!
Workshop: Security Fabric Challenge
Me, a friend and three other Compass colleagues participated in the Fortinet challenge. The goal was to configure several Fortinet firewalls according to some requirements. We all had basically no deep Fortinet knowledge and experience but we let us explain some configuration steps by the helpful Fortinet employees. In the end, we managed to win the 3rd place. We won a bottle of wine and a dry bag that will definitively used in the Aare this year :-).
Workshop: Lockpicking Area
The people from SPASS (http://lockpicking.ch/) taught other people how to pick locks in the lockpicking area.
(Image source: https://twitter.com/wizche/status/1007994489372278784)
Conclusion
This was an awesome conference with a lot of qualitative talks and cool workshops. It was fun to meet other people. Thanks to the organization committee Candid (https://twitter.com/mylaocoon), Désirée (https://twitter.com/d3sre) and krogoth (https://twitter.com/le_krogoth)!





Leave a Reply