About a year ago, the Burp extension SAML Raider [0] was released as a result of a bachelor thesis [1] in collaboration with Compass Security. This Burp extension automates most of the steps, which are necessary to test a SAML single sign-on process and perform according attacks. With SAML Raider, an authentication bypass vulnerability in a Service Provider was found [2]. More information is available in our first blog post about SAML Raider here: SAML Burp Extension [5].
We did some bugfixing and added new features to SAML Raider in the past year. In version 1.2.0, we introduced the new ability to intercept and edit SAMLRequest Messages. The current version is 1.2.1, which is available here [3] on GitHub. It will also be in the official Burp Suite BApp store [4] shortly.
Decode SAMLRequest Message
There are several Burp Extensions [6] like SAML ReQuest [7], SAML Editor or SAML Encoder which allows you to edit SAMLRequests. We also got asked [8] if this feature is supported in SAML Raider, which was not the case. Because this would be a nice feature, we implemented it in version 1.2.0.
What is a SAMLRequest?
A SAMLRequest is the SAML message, which is sent from the user (browser) to the Identity Provider, to “ask” for an assertion. Usually, the SAMLRequest is sent to the Identity Provider, which will respond with a login form to ask for the credentials. If the login was successful, the SAMLResponse is sent back to the client, which is then forwarded to the Service Provider.
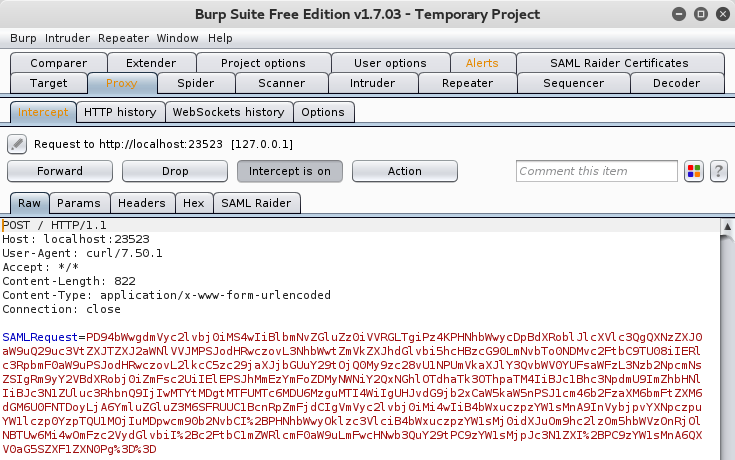
A SAMLRequest is sent via POST to the Identity Provider and looks like this:
So, it’s quite clear, that this is not so practical for quick editing and testing.
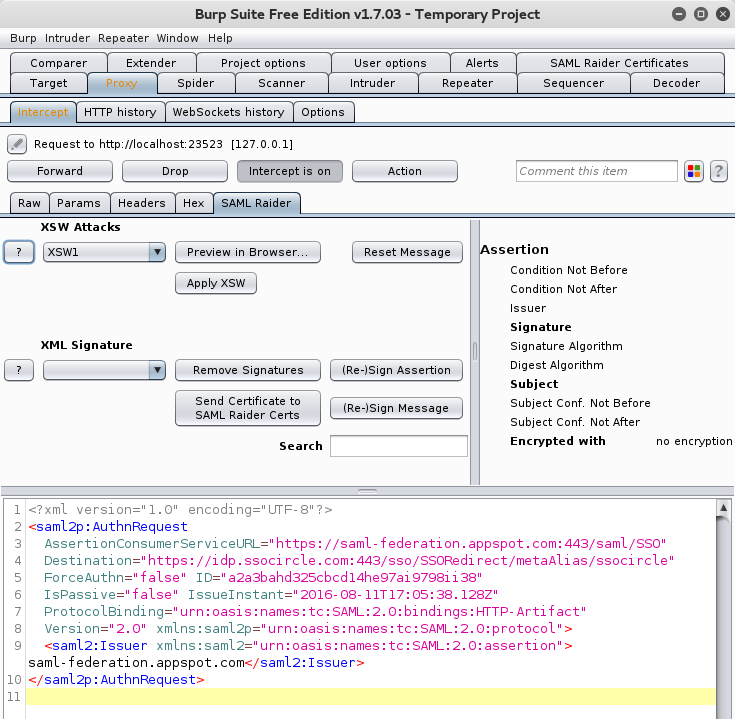
SAMLRequest in SAML Raider
SAML Raider is now able to properly decode a SAMLRequest and display it in the SAML Raider tab:
Now it is very easy to modify the SAMLRequest. The SAMLRequest is automatically encoded back in it’s original format and forwarded to the target, if the Forward button is clicked.
But why do you need to view/edit the SAMLRequest? With this new feature, you can read what the client is sending exactly to the Identity Provider and perform fuzzing or testing the Identity Provider itself.
So, if you have any questions, issues or features requests, don’t hesitate to contact us or open an Issue on GitHub [0].
References
- [0] SAMLRaider on GitHub: https://github.com/SAMLRaider/SAMLRaider
- [1] Bachelor Thesis: https://eprints.hsr.ch/464/1/eprints_BA_SAML2_Burp_Plugin_SAML_Raider_eduss_rbischof.pdf
- [2] SAML Service Provider Authentication Bypass: https://blog.compass-security.com/2015/09/saml-sp-authentication-bypass-vulnerability-in-nevisauth/
- [3] SAML Raider Releases: https://github.com/SAMLRaider/SAMLRaider/releases
- [4] SAML Raider in the Burp BApp Store: https://portswigger.net/bappstore/ShowBappDetails.aspx?uuid=c61cfa893bb14db4b01775554f7b802e
- [5] Blogpost about SAML Raider: https://blog.compass-security.com/2015/07/saml-burp-extension/
- [6] Fuzzing SAML: http://www.sjoerdlangkemper.nl/2016/07/28/fuzzing-saml-with-samlrequest/
- [7] SAMLReQuest Burp Extension: https://www.insinuator.net/2016/06/samlrequest-burpsuite-extention/
- [8] Blog comment asks for SAMLRequest feature: https://blog.compass-security.com/2015/07/saml-burp-extension/#comment-322651
Leave a Reply