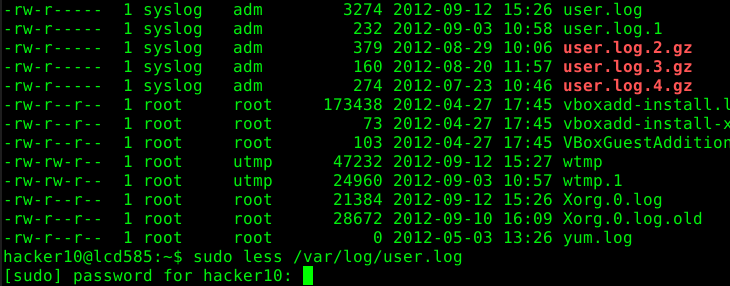
The following article describes common security issues regarding misconfigured sudoers’ files. The article focuses on a single entry which contains several security issues:
hacker10 ALL= (root) /bin/less /var/log/*
The article is split into the following five chapters:
- PART 1: Command Execution
- PART 2: Insecure Functionality
- PART 3: Permissions
- PART 4: Wildcards
- PART 5: Recapitulation
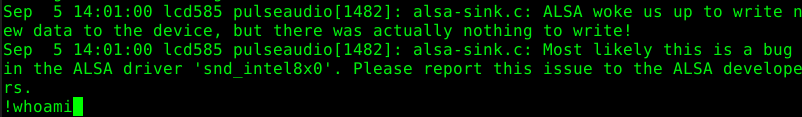
In this article we are going to focus on the command execution feature of “less” which may appear in other applications and scenarios as well. “less” allows a user to execute arbitrary commands by entering “!”.
Excerpt from the less man page:
! shell-command Invokes a shell to run the shell-command given. A percent sign (%) in the command is replaced by the name of the current file. A pound sign (#) is replaced by the name of the previously examined file. "!!" repeats the last shell command. "!" with no shell command simply invokes a shell. On Unix systems, the shell is taken from the environment variable SHELL, or defaults to "sh". On MS-DOS and OS/2 systems, the shell is the normal command processor.
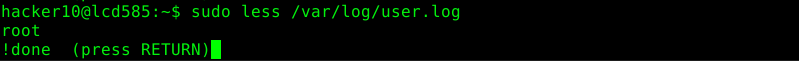
As an example, we run the command “whoami” within “less”:
This command is being executed with the same rights “less” is running. Therefore, whoever is allowed to read a file with less is allowed to execute commands with the same rights. In this case as the user “root”.
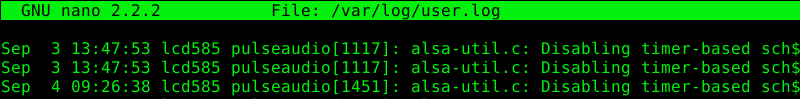
Another feature that falls in the category command execution is the possibility to start the default text editor as this is nothing else but the execution of another application. To start the default text editor the user has to press the “v” key.
Excerpt from the man page:
v Invokes an editor to edit the current file being viewed. The editor is taken from the environment variable VISUAL if defined, or EDITOR if VISUAL is not defined, or defaults to "vi" if neither VISUAL nor EDITOR is defined. See also the discussion of LESSEDIT under the section on PROMPTS below.
In our case we start the editor “nano” from “less”:
Of course it is possible to prevent “less” from executing arbitrary commands. There are two possible ways to do this. The one described in this part of the blog post focuses on the general prevention of additional command execution and isn’t “less” specific. Therefore, it is possible to use this solution for other applications as well.
Solution
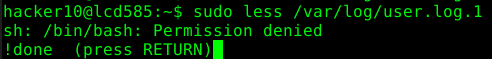
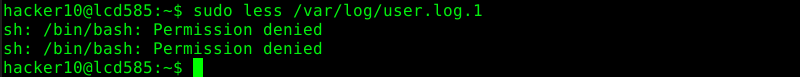
The execution of other binaries might be prevented by adding the NOEXEC tag in the sudoer’s file. This works only if “sudo” has been compiled with noexec support and if the underlaying OS supports this as well.
hacker10 ALL= (root) NOEXEC: /bin/less /var/log/*
The following two screenshots shows the results of the previously described methods to run an arbitrary command or default editor.
Leave a Reply