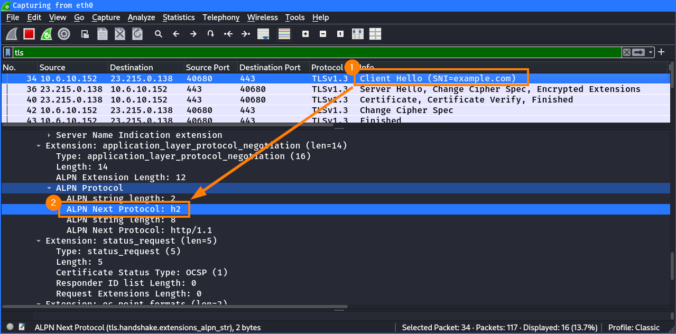
In the previous posts of this series, we looked at different ways to bypass web filters, such as Host header spoofing and domain fronting. As we’ve learned, these techniques can be detected by proxies employing TLS inspection, by checking whether the hostname in the SNI matches the one in the HTTP Host header. If they […]
Compass Security Blog
Offensive Defense
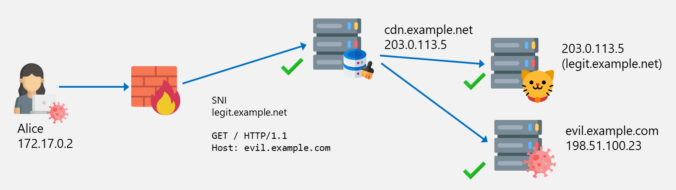
The last two blog posts in this series were about SNI spoofing and Host header spoofing. We also learned that the latter is addressed by some vendors with a technique called “Domain Fronting Detection”. But what exactly is domain fronting? This will be explained in this blog post.
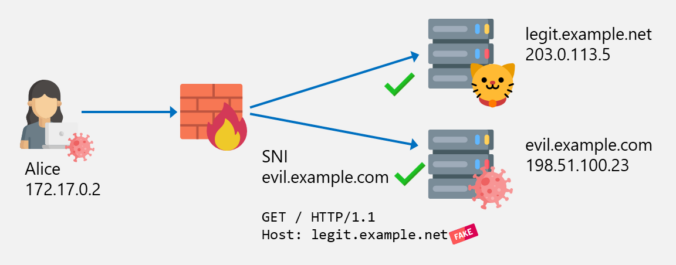
In the last post about bypassing web filters, I discussed how SNI spoofing works and how this can also be prevented by web filters. This post is about another bypass technique called Host Header spoofing.
This is the first part of a series of blog posts about techniques to bypass web filters, looking at increasingly advanced techniques with each part.
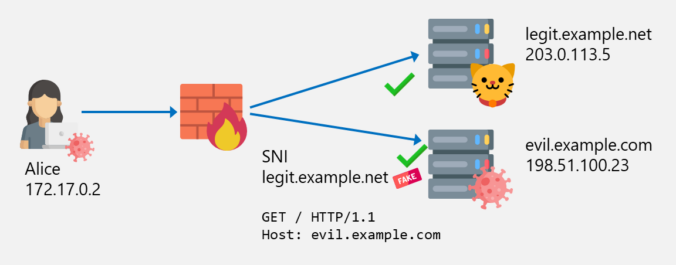
The first part is about how SNI spoofing can be used to bypass web filters.
With the rise of remote working, Microsoft Teams has become the de-facto standard for video conferences, chat, and collaboration. The nature of the Teams architecture are some central systems that route information between parties. With that comes that Teams client software must be allowed to communicate to the Internet. Microsoft even recommends letting Teams traffic bypass inspection proxies for compatibility reasons. Its network communication pattern has significant overlap with malicious C2 traffic und thus it is nearly impossible for blue teams to spot adversary communication. Therefore, Teams is an interesting candidate to be abuses for C2 traffic. Thus, we put some research into this.
When accessing a remote server, one should always assume it has been compromised or might be in the near future. It is particularly crucial for users with administrative privileges to establish a secure connection to the Remote Desktop Protocol (RDP) service in order to not fall victim to credential theft or impersonation. To achieve this, there exist several measures in Windows. In this blog post, we’ll look at some of them, their benefits and their drawbacks.
Passwordless products promise greater security and convenience by allowing users to log in to Windows systems with only their smartphone. But what is going on behind the scenes and how could a domain’s security stance be worsened by such a solution? In this post I will explain how these products are implemented and detail the vulnerabilities and weaknesses discovered in three tested products.
A post on how to trick browsers to work as a gateway to internal web servers and IoT devices, the concepts behind and how to easily exploit DNS rebinding using the Singularity of Origin framework.
Fighting cybercrime is one of the reason Switch announced to publish the .ch zone. Switzerland has a law on Open-Government-Data-Strategy that follows the open-by-default strategy The .ch zone file contains all registered .ch domain names that have a NS record that points to the nameserver that gives authoritative answers for that domain name. Compass Security is offering […]
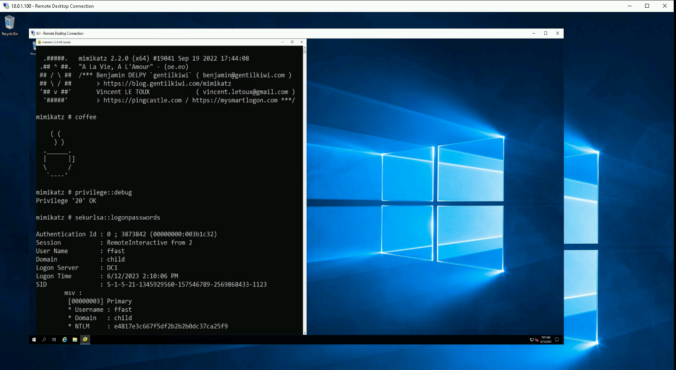
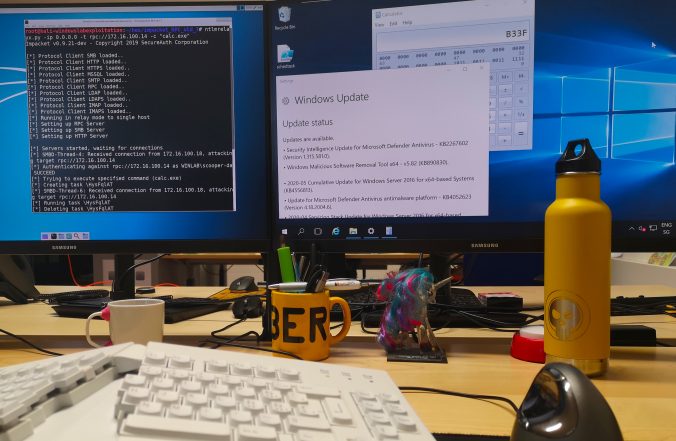
Since a few years, we – as pentesters – (and probably bad guys as well) make use of NTLM relaying a lot for privilege escalation in Windows networks.
In this article, we propose adding support for the RPC protocol to the already great ntlmrelayx from impacket and explore the new ways of compromise that it offers.
This vulnerability was discovered by Compass Security in January 2020, disclosed to Microsoft Security Response Center and assigned CVE-2020-1113 as identifier.
© 2025 Compass Security Blog