A journey into the discovery of privilege escalation vulnerabilities in the Lenovo Update process.
Compass Security Blog
Offensive Defense
Page 2 of 6
When accessing a remote server, one should always assume it has been compromised or might be in the near future. It is particularly crucial for users with administrative privileges to establish a secure connection to the Remote Desktop Protocol (RDP) service in order to not fall victim to credential theft or impersonation. To achieve this, there exist several measures in Windows. In this blog post, we’ll look at some of them, their benefits and their drawbacks.
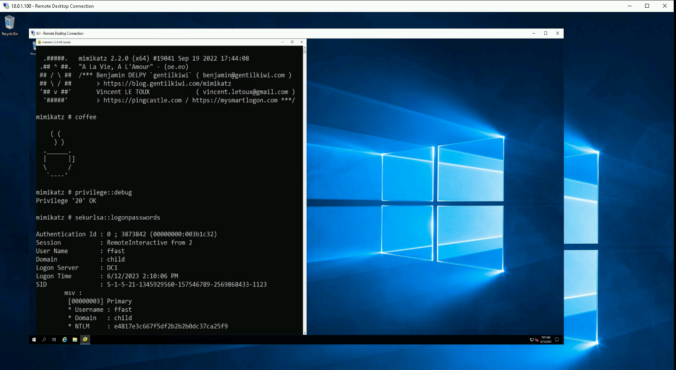
Sometimes, the good old credential dumping techniques just won’t work. This is the story of how a bad actor could dump credentials on a fully-patched, monitored and hardened workstation.
The ntds.dit file from a domain controller contains all password hashes of the domain. In a company with employees around the globe we were allowed to analyze the hashes. Here are the results, and the reason why you should implement a banned password list.
Passwordless products promise greater security and convenience by allowing users to log in to Windows systems with only their smartphone. But what is going on behind the scenes and how could a domain’s security stance be worsened by such a solution? In this post I will explain how these products are implemented and detail the vulnerabilities and weaknesses discovered in three tested products.
BloodHound is the way to go to for finding attack paths in an Active Directory (AD) environment. However, it is not always clear how the data is gathered without looking at the code of SharpHound, the data ingestor for BloodHound. Microsoft hardened their systems over time through updates, which makes enumeration of Active Directory (AD) […]
BloodHound is the way to go to for finding attack paths in an Active Directory (AD) environment. However, it is not always clear how the data is gathered without looking at the code of SharpHound, the data ingestor for BloodHound. Microsoft hardened their systems over time through updates, which makes enumeration of Active Directory (AD) […]
BloodHound is the way to go to for finding attack paths in an Active Directory (AD) environment. However, it is not always clear how the data is gathered without looking at the code of SharpHound, the data ingestor for BloodHound. Microsoft hardened their systems over time through updates, which makes enumeration of Active Directory (AD) […]
Agile software development models have become the de-facto standard. They are taught at universities and implemented in practice as far as possible. Anyone who doesn’t develop software using agile processes is on the verge, and already tilting towards that. At least that is how it seems. Consequently, the question is not whether the integration of […]
The end of the year is a good time to sit back and reflect for a moment on the past year. So let us take a look at the ten most common ways how I got Domain Admin privileges in our Active Directory penetration tests in 2021.
© 2025 Compass Security Blog