As a defender, you want to find and patch attack paths in your Active Directory environment. One cannot easily spot issues by looking at the Active Directory Users and Computers console, GPOs, etc. but here comes BLOODHOUND.
Compass Security Blog
Offensive Defense
Page 11 of 29
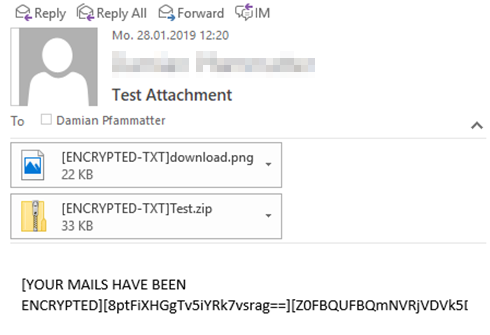
Ransomware focuses on encrypting data on a filesystem-level, either locally on infected client systems or remotely on accessible file servers. However, what if ransomware would start encrypting data on an application-level too?
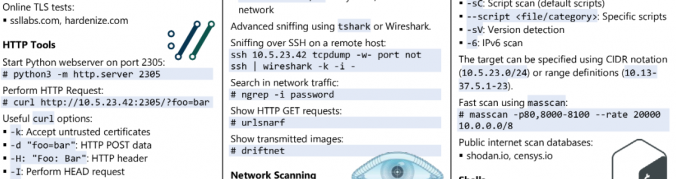
Everyone knows: cheat sheets are cool! They are very useful if you already know the basics about a topic but you have to look up details when you are not sure about something.
Mobile applications nowadays make heavy use of WebViews in order to render their user interfaces. Frameworks such as PhoneGap / Apache Cordova are even used to implement most of the application’s functionalities using WebViews only.
While native code, both in Android and in iOS, can quickly be analyzed using dynamic analysis tools like Frida, operations performed in WebViews cannot be easily debugged with the same methods.
Usually you need to pay for lunches with cash or using your credit card. But in some places employees can pay for a lunch using their access badge. And this is the payment method that will be covered in this blogpost.
Black box analysis of a not so smart card in ID-1 form factor that is in use for the billing of washing machines and tumble driers.
In this post, we are going to take a closer look at the enOcean technology, how security is implemented, and if the security measures and options available are sufficient.
In this last article about privilege escalation in Windows domains, we demonstrate how to extract credentials from running systems to compromise high-privileged accounts.
This second article about privilege escalation in Windows domains describes how to propagate by aiming for passwords that are lying around.
This first article of our series about privilege escalation in Windows domains demonstrates how to get a foothold by relaying credentials from users.
© 2026 Compass Security Blog