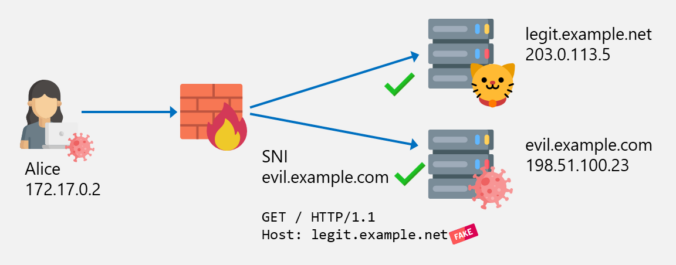
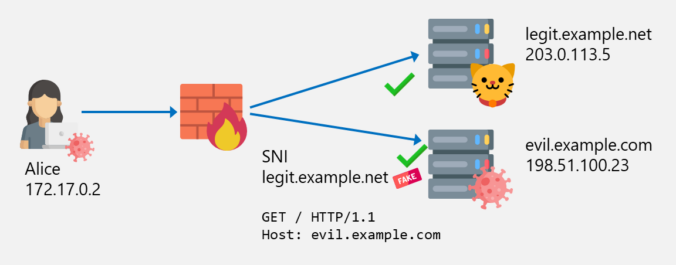
In the last post about bypassing web filters, I discussed how SNI spoofing works and how this can also be prevented by web filters. This post is about another bypass technique called Host Header spoofing.
Compass Security Blog
Offensive Defense
Page 3 of 29
This is the first part of a series of blog posts about techniques to bypass web filters, looking at increasingly advanced techniques with each part.
The first part is about how SNI spoofing can be used to bypass web filters.
Don’t we all know the hassle of managing loads of passwords, trying to come up with secure and unique ones only to try afterwards to remember them? Or always staying on high alert whether the URL is definitely the valid one for the website we are trying to visit?
What if all this could be over soon?
Welcome to Passkeys!
Introducing a certipy parse command to perform stealthy offline AD CS enumeration based on local registry data.
This blog post introduces our new custom queries for BloodHound Community Edition (CE) and explains how you can use them effectively to analyze your Active Directory infrastructure. TL;DR: Check out our new BloodHound CE custom queries! Active Directory and BloodHound The majority of our customers run a Microsoft Active Directory infrastructure, either exclusively on-prem or […]
Over the past few years, we have had the opportunity to conduct several Purple Teaming exercises together with our customers.
Particularly after Purple Teaming exercises involving external providers, we often see a mismatch between the customer’s expectations and the service provided.
This blog post attempts to summarize how to prevent the most prevalent issues with a managed security service as early as possible.
Red Teaming engagements are “realistic” attack simulations designed to test the security posture of an organization and its Blue Team. This term is used in many different ways, so if you’re not sure where to draw the line, Michael Schneier’s latest blog post provides a good comparison of different types of assessment. Anyway, when doing […]
TLDR: Scan GitLab job logs for credentials using https://github.com/CompassSecurity/pipeleak Many organizations use (self-hosted) GitLab instances to manage their source code and a lot of infrastructure is managed in code (IaC), thus these configurations must be source-controlled as well, putting a lot of responsibility on the source code platform in use. Often deployments are automated using CI/CD […]
At Compass Security, we are proud to offer a fully managed bug bounty program tailored to the needs of both SMEs and larger enterprises. From scoping to payout, we manage every aspect of the process to ensure a seamless experience for our customers and valued hunters. In this blog post, we’ll take a look at our journey since the launch of our service in October 2023, highlighting key milestones, metrics and learnings gathered along the way.
During Business Email Comproise (BEC) engagements we often have to analyze the provenance of emails. According to the FBI’s Internet Crime Report, BEC is one of the most financially damaging attacks, even surpassing ransomware in terms of losses. But how can we know all of this? Through email headers! This blog post tries to shed some light on the information contained within emails, what it means, and what can be done to prevent this type of attack.
© 2026 Compass Security Blog