Due to recent developments we figured it would be great to contribute a cheat sheet and create security best-practices on how to tie down a Microsoft on-prem environment. Our work mostly relies on MS recommendations. However, we put some effort to really condense it to the essence. We hope to see this applied everywhere and thus open-sourced everything in our GitHub repository.
Compass Security Blog
Offensive Defense
Page 9 of 29
We show how to decrypt passwords from the configuration backup of a Xerox WorkCentre and how, during the reverse engineering, a command injection vulnerability was discovered (CVE-2021-27508).
We put more and more sensitive data on mobile devices. For many private conversations we use mobile applications, such as WhatsApp. This smooth access to the data and the Internet provides multiple benefits in our lives. On the other side, new attack vectors are created. Phishing messages do not need to be delivered in an […]
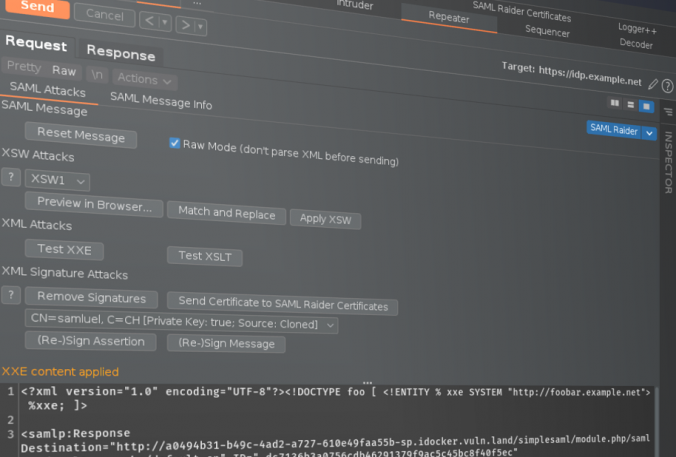
SAML Raider 1.4.0 is out which contains several new features like UI changes, new text editor, raw mode, XSW match/replace, parameter name definition and attack templates for XXE and XSLT attacks.
A post on how to trick browsers to work as a gateway to internal web servers and IoT devices, the concepts behind and how to easily exploit DNS rebinding using the Singularity of Origin framework.
Fighting cybercrime is one of the reason Switch announced to publish the .ch zone. Switzerland has a law on Open-Government-Data-Strategy that follows the open-by-default strategy The .ch zone file contains all registered .ch domain names that have a NS record that points to the nameserver that gives authoritative answers for that domain name. Compass Security is offering […]
Intro into a Compass Splunk App, which can be used to perform a first triage and high level analysis of Volatility results coming from multiple hosts.
This part will discuss a grey-box approach in defeating malware detection. It will discuss the relevant features used and how they are fed into a malware detection model to classify an input file. After a short theory part, we try to find out which features are especially important for malware analysis and how to modify them. Finally, we will change some of the features of our ransomware to evade our model. But before all this, it is advisable to get familiar with the file format used by our malware.
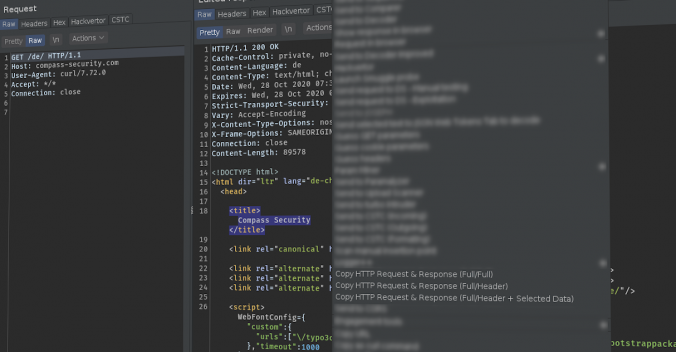
Writing good reports is key in penetration tests / security assessments, since this is the final result delivered to the customer. Vulnerabilities should be described in a way so that the customer can understand and also reproduce the issue. For web application pentests, the best way is often to show the HTTP requests and responses to explain an issue. This Burp Suite extension “Copy Request & Response” can assist you while the report.
Modern anti-malware products such as Windows Defender increasingly rely on the use of machine learning algorithms to detect and classify harmful malware. In this two-part series, we are going to investigate the robustness of a static machine learning malware detection model trained with the EMBER dataset. For this purpose we will working with the Jigsaw ransomware.
© 2026 Compass Security Blog