The end of the year is a good time to sit back and reflect for a moment on the past year. So let us take a look at the ten most common ways how I got Domain Admin privileges in our Active Directory penetration tests in 2021.
Compass Security Blog
Offensive Defense
On October 12th the Swiss Cyber Storm conference took place in the Kursaal in Bern. Several Compass analysts attended the conference, our security analyst Yves Bieri held a talk and we also had a booth. The conference was great fun, finally a in-person conference with many interesting talks. This blog post wraps up some talks we attended.
Sometimes one goes deep down the rabbit hole, only to notice later that what we were looking for is just under one’s nose.
This is the story of a digital forensic analysis on a Linux system running docker containers. Our customer was informed by a network provider that one of his system was actively attacking other systems on the Internet. The system responsible for the attacks was identified and shut down.
Our DFIR hotline responded to the call and we were provided with a disk image (VMDK) to perform a digital forensic analysis.
ArcGIS [1] is a family of software providing geographic information system services. While testing a customer’s ArcGIS architecture we came across a SAML login flow. In this blogpost we show how we found and exploited an AES-CBC padding oracle in this flow.
During a customer project, we could bypass the biometric authentication mechanism of Ionic Identity Vault on Android, because the Android KeyStore entry does not require any authentication. This post shows how this was done and how it can be exploited.
A little bit over a year ago, I wrote an article on this blog about CVE-2020-1113 and how it enabled to execute code on a remote machine through relaying NTLM authentication over RPC triggering a scheduled task on the remote system. History repeats itself and a vulnerability of the same category has been fixed by Microsoft in June this year.
Due to recent developments we figured it would be great to contribute a cheat sheet and create security best-practices on how to tie down a Microsoft on-prem environment. Our work mostly relies on MS recommendations. However, we put some effort to really condense it to the essence. We hope to see this applied everywhere and thus open-sourced everything in our GitHub repository.
We show how to decrypt passwords from the configuration backup of a Xerox WorkCentre and how, during the reverse engineering, a command injection vulnerability was discovered (CVE-2021-27508).
We put more and more sensitive data on mobile devices. For many private conversations we use mobile applications, such as WhatsApp. This smooth access to the data and the Internet provides multiple benefits in our lives. On the other side, new attack vectors are created. Phishing messages do not need to be delivered in an […]
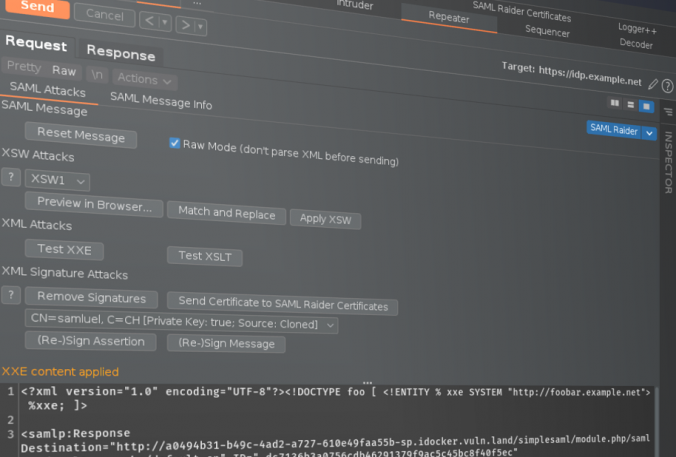
SAML Raider 1.4.0 is out which contains several new features like UI changes, new text editor, raw mode, XSW match/replace, parameter name definition and attack templates for XXE and XSLT attacks.
© 2026 Compass Security Blog