In case of an incident you’ll want to be ready to respond fast. Time is a crucial factor during an incident and the faster you move, the better. You want your Incident Resonse Team to be quick and prepared to work almost out of the box. We even made a blog post about challenging the forensic readiness a while ago.
The article discusses the very basics to keep systems ready for analysis of lateral movement. We present some guidelines and a tool (Readinizer) that you can run, to ensure that everything is set up as in the guidelines provided.
This will help you detect and react to lateral movements in your network.
Who is this guide for
This blog post is based on a thesis done in collaboration with the University of Applied Sciences Rapperswil HSR. The goal was to provide small enterprises with simple means of checking the most important settings against lateral movement but to avoid the learning curve of the Microsoft Security Compliance Toolkit.
Guidelines for lateral movement detection and security logs in general
To be prepared for a forensic investigation, systems need to log events. Some events cause noise, others deliver useful insights, but most are a mixed bag of noise and information. We will need a healthy mix to enable the investigation team to act fast and precise. This is where the guidelines come in.
There is quite a number of reputable institutions that provide well thought guidelines. The team of students that worked on the project relied on documentation by
- CERT-EU
- NSA
- JPCERT/CC
- ACSC
- MITRE
- SANS
- Microsoft
But what is Readinizer looking for specifically?
Explanations
This paragraph aims to justify some of the settings that the Readinizer tool checks and are included in the cheat sheet or why some configurations are skipped.
Pass the Hash Detection settings
Well, the obvious. Related events should definitely be logged to be able to detect lateral movement.
Account Lockout settings
To detect brute-force attacks of account logins, this policy should be considered and activated. Since only Failure events are thrown by these events, the guideline recommends logging failures only.
PowerShell Execution settings
PowerShell is a very powerfull interactive command-line, attackers can use it to do all sorts of malicious things on the system or network. This includes execution of code, changing configurations and creating accounts for example. Thus it is recommended to enable “Turn on Module Logging” and “Turn on PowerShell script Block Logging”.
Windows Update Errors settings
Since most enterprises roll out software and updates using other tools, the logging of these events is not considered in the readinizer tool.
Clearing event logs settings
The readinizer tool checks if these events are logged, since they’re a strong indication of a malicious attack or malware.
Why is there no application whitelisting configuration?
Application whitelisting can be very powerful to prevent advanced persistent threats. But since the application whitelisting is very elaborate and the Readinizer tool is tailored for small sized enterprises it is not included.
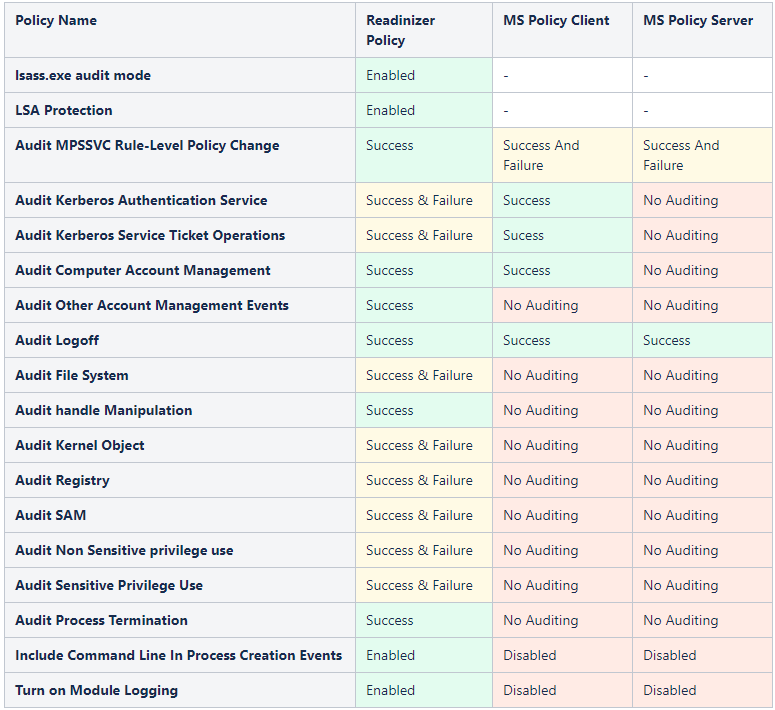
Comparison with Microsoft Policy
The table below shows some of the differences between the Readinizer Baseline Policy and the Policy suggested by Microsoft:
Using Readinizer
An extensive user manual with requirements, installations guide, how to’s and explanations can be found on the official github repo.
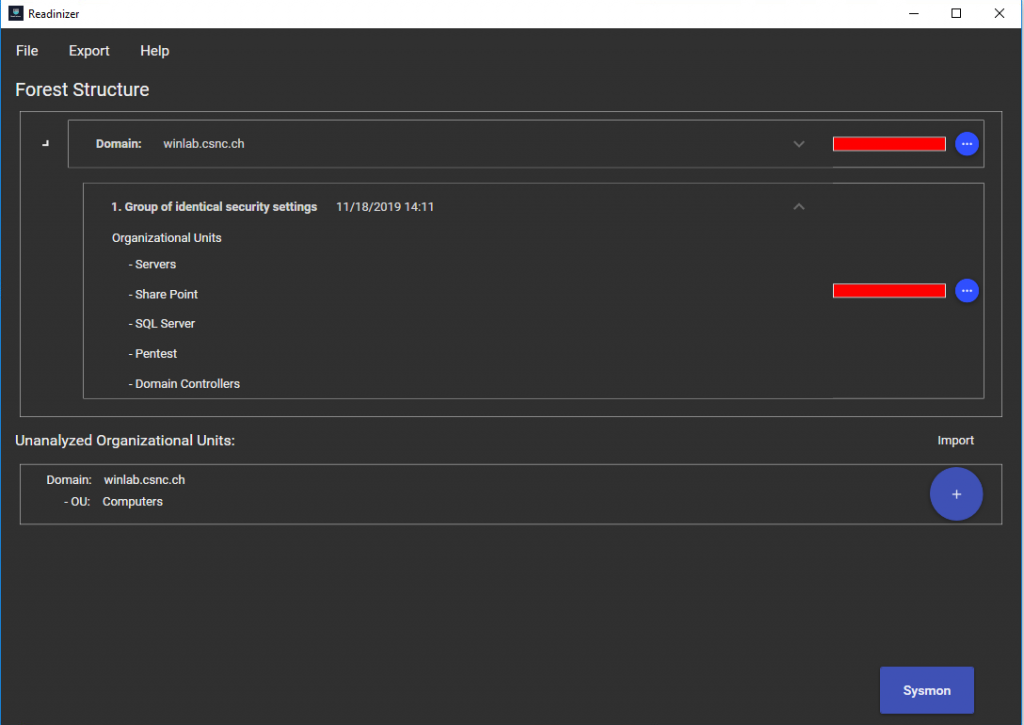
Readinizer can be used to implement the guidelines proposed in the cheat sheet with 4 simple steps:
- build Readinizer and install it according to the manual (incl. Recommended GPO Settings)
- run the tool over you domain and go grab a coffee
- once the Readinizer has done its job, you should get a report of how good you performed:
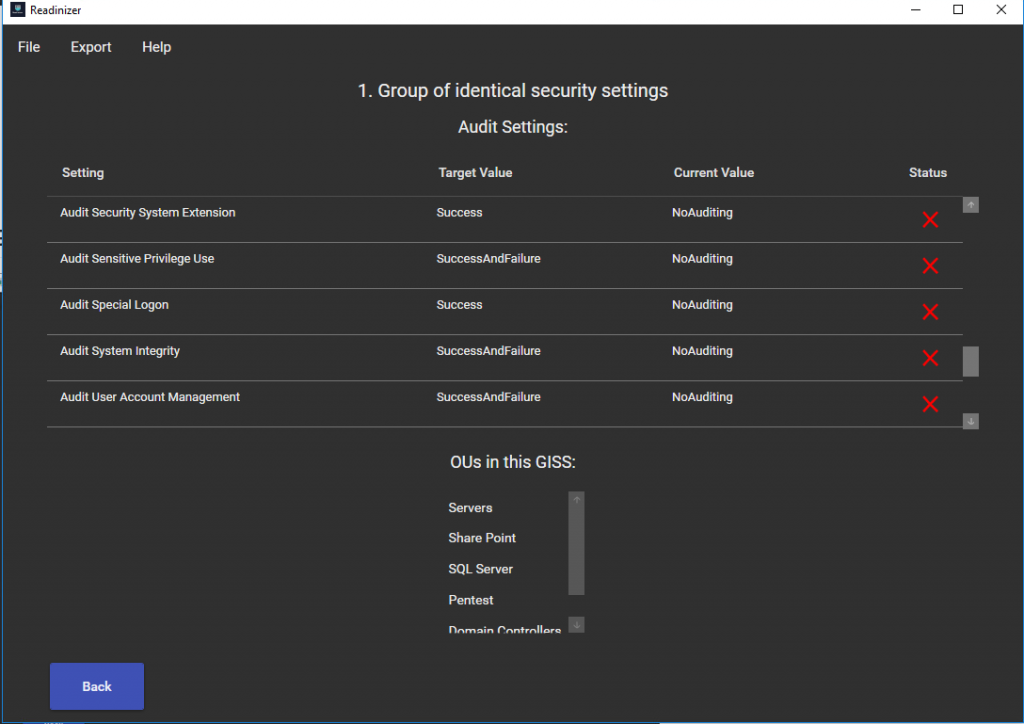
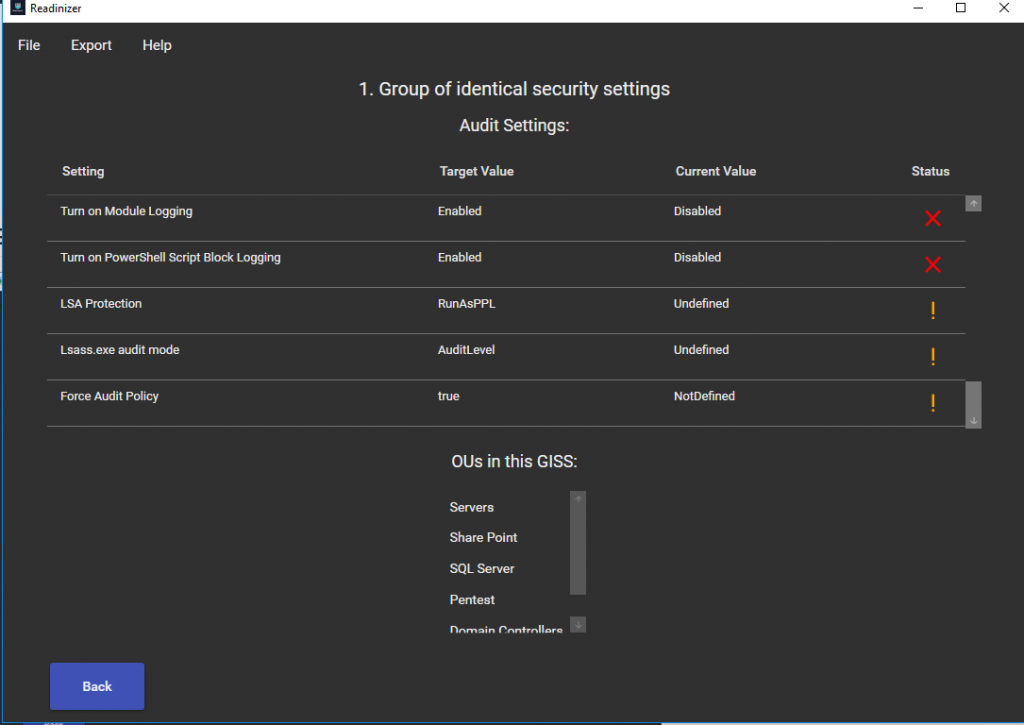
In most cases, everything will be bad or partially or undefined. But now that we have this information, we can go change the GPO’s and update them on the machines. After the configuration is done, you can rerun Readinizer and most things should be good.
Step 4 would be to change the config and repeat from step 2.
Further reading
If you are curious on how to do even more than just tuning GPOs then you are kindly advised to check Readinizer’s Wiki page and learn on how to deploy Sysmon or how to create a central log collector. No sales buzz, no AI magic, no license fees – just leveraging what Microsoft provides out-of-the-box.
Credits
Claudio Mattes and Lukas Kellenberger for diving into the topic, compiling an overview on the various guidelines and getting their hands dirty programming the Readinizer!
Mattia Ninivaggi for preparing the post and compiling the cheat sheet.
The University of Applied Sciences in Rapperswil, HSR (soon to become OST) electrical engineering, software and security faculties for their close collaboration.
References
- GovCERT.ch. APT Case RUAG (Espionage Case at RUAG). Technical report, MELANI:GovCERT, May 2016.
- JPCERT/CC. Detecting Lateral Movement through Tracking Event Logs. , June 2017.
- CERT-EU. Detecting Lateral Movements in Windows Infrastructure. , February 2017.
- NSA. Spotting the Adversary with Windows Event Log Monitoring. , December 2013.
- Australian Cyber Security Center – ACSC. Windows Event Logging and Forwarding. , January 2019.
- Microsoft. Use Windows Event Forwarding to help with intrusion detection. , February 2019
- Jessica Payne. Monitoring what matters. Windows Event Forwarding for everyone (even if you already have a SIEM.). , November 2015
- SwiftOnSecurity. sysmon-config. , May 2019.
- Readinizer Abstract, e-prints Archive
- Readinizer Thesis, FS 2019-BA-EP-Mattes-Kellenberger-Readinizer (Readiness Analyzer, Visualizer and Optimization).pdf (180 pages)
Leave a Reply