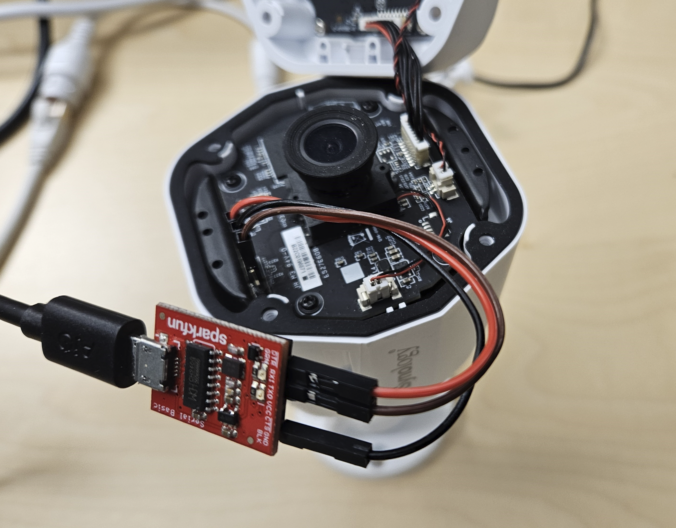
Introduction As you may know, Compass Security participated in the 2023 edition of the Pwn2Own contest in Toronto and was able to successfully compromise the Synology BC500 camera using a remote code execution vulnerability. If you missed this, head over to the blog post here https://blog.compass-security.com/2024/03/pwn2own-toronto-2023-part-1-how-it-all-started/ Unfortunately, the same vulnerability was also identified by other […]
Compass Security Blog
Offensive Defense
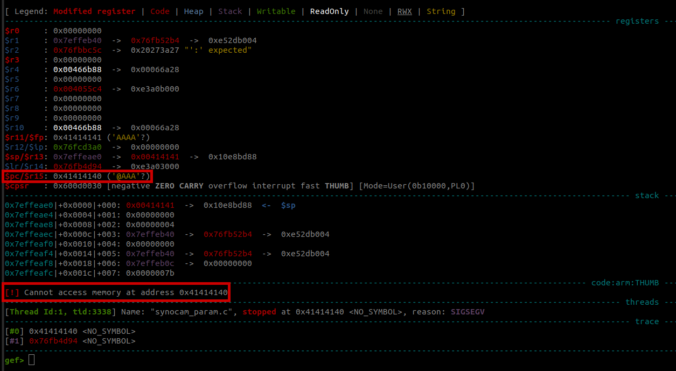
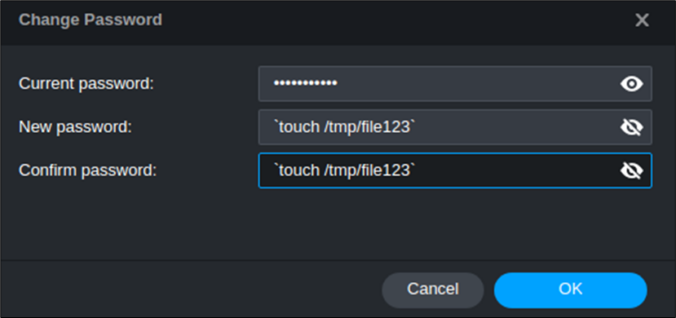
In this final part of this series, we are finally going to explain how the stack-based buffer overflow vulnerability can be exploited to gain unauthenticated remote code execution (RCE) on the Synology BC500 camera.
In this fourth part of the series, we analyze the memory corruption identified previously and manage to overwrite the program pointer!
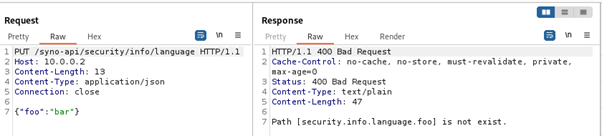
In this third part of the series, we focus on the exposed web services running on TCP ports 80 and 443.
Since a valid exploit chain must achieve code execution without prior authentication, we focus on the available functionality that can be accessed without authentication.
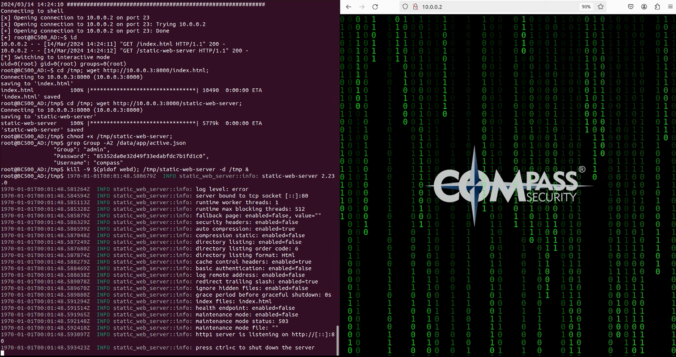
In this second blog post of the series, we start with the reconnaissance phase on the camera, a crucial step in understanding our target.
The aim here is to gather information about the target and identify potential vulnerabilities.
Around a year ago a few Compass analysts watched a talk at the Insomni’Hack conference about the Pwn2Own contest.
This is when they decided to take part! In this blog post, they talk about how they picked their target, got the firmware from the camera, and got into the shell.
Internet of Things (IoT) and Operational Technology (OT) is an area that has grown strongly in recent years and is increasingly being used in the business world. To be able to test the security in this area, let’s take a closer look at the Message Queuing Telemetry Transport (MQTT) protocol to understand the strengths and weaknesses of the protocol.
A post on how to trick browsers to work as a gateway to internal web servers and IoT devices, the concepts behind and how to easily exploit DNS rebinding using the Singularity of Origin framework.
Black box analysis of a not so smart card in ID-1 form factor that is in use for the billing of washing machines and tumble driers.
In this post, we are going to take a closer look at the enOcean technology, how security is implemented, and if the security measures and options available are sufficient.
© 2026 Compass Security Blog