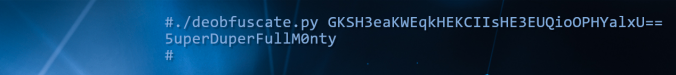
Device code phishing is nothing new. In fact it has been around for some years now. Despite the awesome capabilities of device code phishing, it is not widely used by threat actors. Therefore, it probably does not receive much attention from Microsoft. Compass Security is releasing two tools that can work hand in hand in a device code phishing exercise or even your next red team engagement.
Compass Security Blog
Offensive Defense
Nowadays more and more security tools are used to monitor and generate alerts from different sources (EDR, Proxy, etc.).These alerts often contains URL, domain names, or file hashes that can and should be compared with a threat intelligence source to immediately identify current threats and avoid when possible false positives. In this article, we will […]
ArcGIS [1] is a family of software providing geographic information system services. While testing a customer’s ArcGIS architecture we came across a SAML login flow. In this blogpost we show how we found and exploited an AES-CBC padding oracle in this flow.
During internal penetration tests or Windows client hardening engagements, we often find configuration files with obfuscated passwords. The post demonstrates a general approach and required tools to effectively make use of such credentials.
When attackers try to access confidential data, to steal money or simply to disrupt a business, they will often look for the weakest link to get inside a target network. In some case, this might be an outdated system exposed to the internet or an easy physical access to the network but quite often, the […]
Compass Security is developing security tools on regular basis. I for myself created a plugin/extension for Burp Intercepting Proxy called BurpSentinel. It can makes some tedious manual testing more automated, and helps identifying security vulnerabilities in web applications like XSS weaknesses or SQL injections. Compared to fully automated scanners (like the one already integrated into Burp), it has […]
Mobile Geräte sind ein wesentlicher Teil unseres Lebens, sowohl im Privaten als auch im Unternehmensumfeld. Diesen September führt Compass Security das erste Mal in Bern den iPhone & iPad Security Kurs durch. Was sind die Sicherheitskonzepte bei iOS-Geräten? Wie können iOS-Devices ins Unternehmensumfeld eingebunden werden? Welches sind die gängigen Angriffe und wie kann man sich […]
This article was published when I just flipped through the final slides talking at “Hack in Paris” on smart meter wireless protocol issues. The combo of trainings, conference and the “nuit du hack” is held at the Disney Land Resort Paris for the 4th edition. Yes, Disney Land. When I arrived at the hotel I […]
On this Wednesday (09.04.2014) I gave a presentation at OWASP Switzerland chapter. Initially I choose to present an overview of SSL/TLS, which is based on our previous blog article Compass SSL/TLS recommandations. Accidently, the timing with the OpenSSL heartbleed bug was perfect, so the presentation was updated in time with several slides about this current vulnerability. […]
Die Compass Security AG unternimmt die nächsten Wachstumsschritte auf europäischer Ebene. Unter der Firmierung Compass Security Deutschland GmbH (www.csnc.de) hat das Team rund um Marco Di Filippo (bisher Regional Director Germany) am 01. Januar 2013 ihre Arbeit in Berlin aufgenommen. Die hohe Nachfrage aus dem Raum Deutschland veranlasste die Compass Security AG, ihre Aktivitäten sowie […]
© 2026 Compass Security Blog