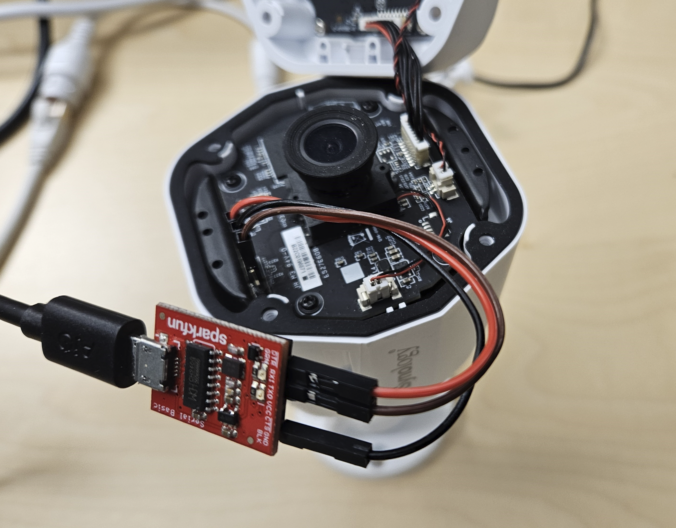
In this final part of this series, we are finally going to explain how the stack-based buffer overflow vulnerability can be exploited to gain unauthenticated remote code execution (RCE) on the Synology BC500 camera.
Compass Security Blog
Offensive Defense
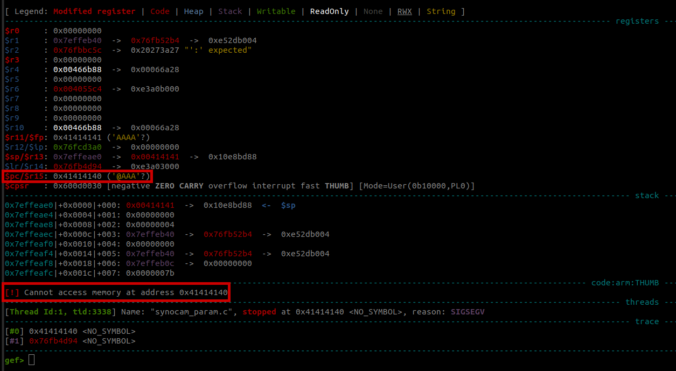
In this fourth part of the series, we analyze the memory corruption identified previously and manage to overwrite the program pointer!
In this third part of the series, we focus on the exposed web services running on TCP ports 80 and 443.
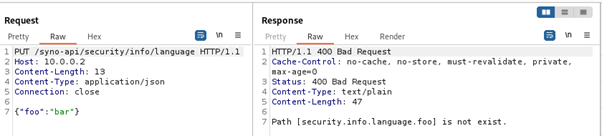
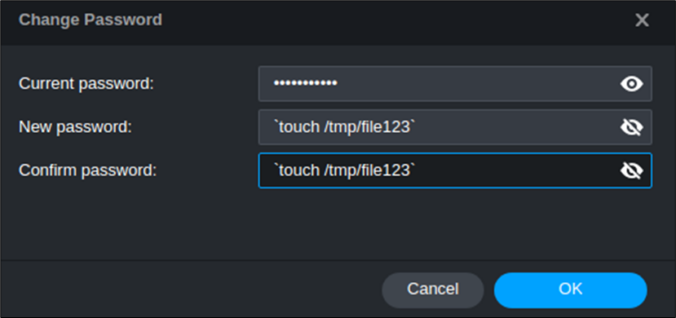
Since a valid exploit chain must achieve code execution without prior authentication, we focus on the available functionality that can be accessed without authentication.
In this second blog post of the series, we start with the reconnaissance phase on the camera, a crucial step in understanding our target.
The aim here is to gather information about the target and identify potential vulnerabilities.
Around a year ago a few Compass analysts watched a talk at the Insomni’Hack conference about the Pwn2Own contest.
This is when they decided to take part! In this blog post, they talk about how they picked their target, got the firmware from the camera, and got into the shell.
In this blog article, we would like to share key insights from the “Defeating Microsoft’s Default BitLocker Implementation” security training by Hands-On Security and emphasize the potential risks and consequences associated with this attack technique. Our target audience includes businesses looking to safeguard sensitive data on their Windows devices, as well as individuals with an elevated requirement for protecting their data.
During a DFIR (Digital Forensics and Incident Response) Case, we encountered an ESXi Hypervisor that was encrypted by the Ransomware LockBit 2.0. Suspicious SSH logons on the Hypervisor originated from an End-of-Life VPN Appliance (SonicWall SRA 4600). It turns out, this was the initial entry point for the Ransomware attack. Follow us into the forensics […]
ArcGIS [1] is a family of software providing geographic information system services. While testing a customer’s ArcGIS architecture we came across a SAML login flow. In this blogpost we show how we found and exploited an AES-CBC padding oracle in this flow.
A write-up of the OWASP Toronto January talk which mainly focused on the correlation and integration of results generated by automated tools in application security such as SAST, DAST and SCA. Alexandre Larocque concludes whether old-fashioned PDF reports are still worth it.
Black box analysis of a not so smart card in ID-1 form factor that is in use for the billing of washing machines and tumble driers.
© 2026 Compass Security Blog