Security in Wi-Fi networks has been, at some point non-existent, then questioned, improved and questioned again over the last two decades. This post provides an overview over the latest developments in Wi-Fi and outlines attacks and defenses.
Compass Security Blog
Offensive Defense
Page 12 of 29
This post is intended to explain what you typically want to check for during an OpenID Connect assessment and also provide you with a guide to setup your own OpenID Connect test environment.
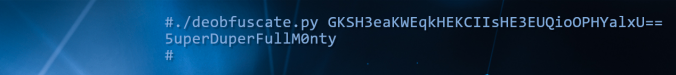
During internal penetration tests or Windows client hardening engagements, we often find configuration files with obfuscated passwords. The post demonstrates a general approach and required tools to effectively make use of such credentials.
Modern problems require modern solutions, this applies to the finance sector as well. So what problems am I talking about? Digital Invoices in a Mixed Payment Slip Landscape In Switzerland we are currently using multiple different variations of payment slips for invoices. There are four different types. Two of them are orange and the other […]
When attackers try to access confidential data, to steal money or simply to disrupt a business, they will often look for the weakest link to get inside a target network. In some case, this might be an outdated system exposed to the internet or an easy physical access to the network but quite often, the […]
Contents Introduction Background Story External Device Access Auditing with Windows Security Event Logs Audit Plug and Play Activity Audit Removable Storage Activity External Device Access Auditing with Default Windows Artifacts Other Ways to Monitor External Device Usage Conclusion References Introduction Have you ever investigated a data leakage case involving a suspect potentially leaking data to […]
Present State of Affairs We have been teaching forensics and network incident analysis for quite a while. We have investigated into a reputable number of cases and we are not the only doing so. Hence, one would expect a certain degree of automation in analysis. However, the high frequency of software release cycles somehow leads […]
In my free time, I like to do some bug bounty hunting. For some reasons, I’ve been doing this almost exclusively for Swisscom. One of the reason is that the scope is very broad and I like to have this vast landscape full of possibilities. While preparing the talk we had at BlackAlps (https://www.blackalps.ch) with […]
Have you ever said something and later regretted it? Or written an email to someone and then wished it had not happened? Or sent an SMS message but afterward desired to change its content? Well, replacing the content of previously sent SMSs is actually possible. SMS messages can be constructed in one of two modes: […]
Contents Introduction Attack Overview Step-by-Step Detection Email Clients Administration Tools Exchange Compliance Features MAPI Editor Eradication Microsoft Security Response Center Swiss Cyber Storm 2018 Conclusion References Introduction In recent investigations, Compass recognized a raise in popularity for attackers to compromise Microsoft Exchange credentials. As one of the first steps after having obtained the credentials (most […]
© 2026 Compass Security Blog