Sometimes, the good old credential dumping techniques just won’t work. This is the story of how a bad actor could dump credentials on a fully-patched, monitored and hardened workstation.
Compass Security Blog
Offensive Defense
Page 7 of 29
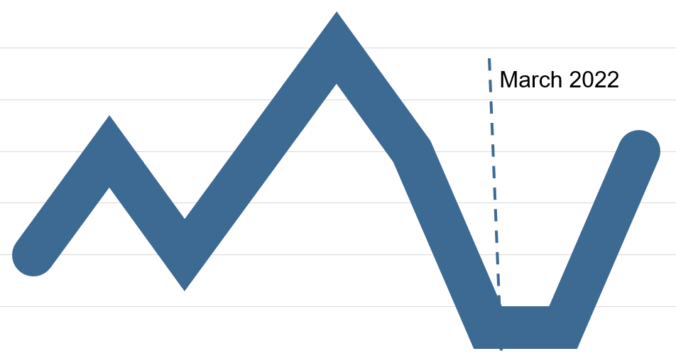
The anonymous data on our cases allows us to answer the question “What is a typical DFIR case at Compass Security?” and we conclude its the analysis, containment, eradication and recovery of one or a few devices in a Windows domain which is probably no surprise :)
Red Teaming exercises are getting popular with the growth of security operations centers. These attack simulations aim to help companies improve their defenses and train the blue team. But solid foundations are necessary to get the most of such an exercise.
Nowadays more and more security tools are used to monitor and generate alerts from different sources (EDR, Proxy, etc.).These alerts often contains URL, domain names, or file hashes that can and should be compared with a threat intelligence source to immediately identify current threats and avoid when possible false positives. In this article, we will […]
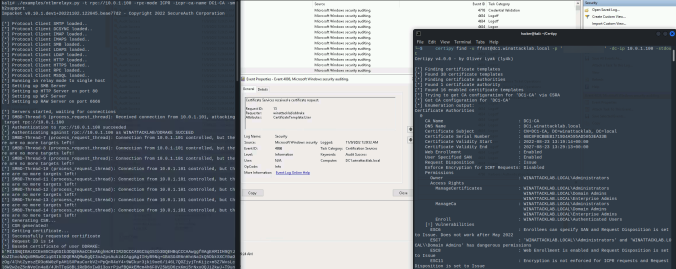
In June last year, the good folks at SpecterOps dropped awesome research on Active Directory Certificate Services (AD CS) misconfigurations. Since then, we find and report these critical vulnerabilities at our customers regularly. One of these new attack path is relaying NTLM authentication to unprotected HTTP endpoints. This allows an attacker to get a valid […]
One of the rare cases where we can decrypt and recover files following-up with a ransomware attack.
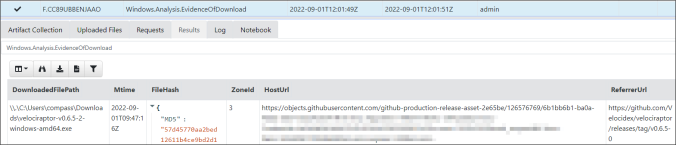
This post provides ideas of processes to follow and gives basic guidance on how to collect, triage and analyze artifacts using Velociraptor
More and more companies use Microsoft 365, well even we at Compass-Security use it internally. Moving to the cloud solves many issues that our DFIR team had to deal with in the past years. Managed infrastructure means no ProxyShell, Hafnium, etc. We’re grateful for that.
Email authentication and security is another complex topic that was often misconfigured in the past. We often could send phishing email in the name of our clients during assessments. Office 365 makes the life of scammers and phishers somehow harder. We’re also grateful for that.
However we still encounter some O365 environments where it’s possible to send spoofed emails. Why is that, you ask? We also wondered and dug into the O365 features and settings!
The ntds.dit file from a domain controller contains all password hashes of the domain. In a company with employees around the globe we were allowed to analyze the hashes. Here are the results, and the reason why you should implement a banned password list.
Passwordless products promise greater security and convenience by allowing users to log in to Windows systems with only their smartphone. But what is going on behind the scenes and how could a domain’s security stance be worsened by such a solution? In this post I will explain how these products are implemented and detail the vulnerabilities and weaknesses discovered in three tested products.
© 2026 Compass Security Blog