Intro into a Compass Splunk App, which can be used to perform a first triage and high level analysis of Volatility results coming from multiple hosts.
Compass Security Blog
Offensive Defense
This part will discuss a grey-box approach in defeating malware detection. It will discuss the relevant features used and how they are fed into a malware detection model to classify an input file. After a short theory part, we try to find out which features are especially important for malware analysis and how to modify them. Finally, we will change some of the features of our ransomware to evade our model. But before all this, it is advisable to get familiar with the file format used by our malware.
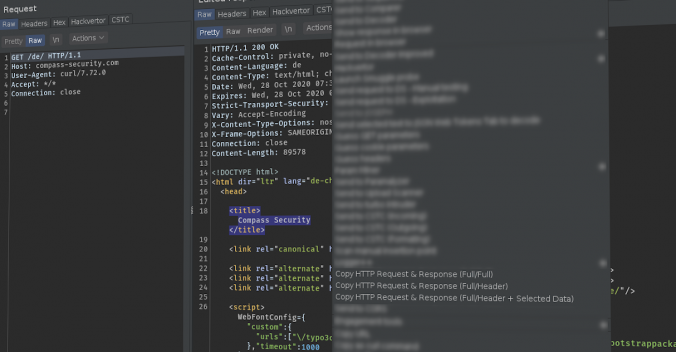
Writing good reports is key in penetration tests / security assessments, since this is the final result delivered to the customer. Vulnerabilities should be described in a way so that the customer can understand and also reproduce the issue. For web application pentests, the best way is often to show the HTTP requests and responses to explain an issue. This Burp Suite extension “Copy Request & Response” can assist you while the report.
Modern anti-malware products such as Windows Defender increasingly rely on the use of machine learning algorithms to detect and classify harmful malware. In this two-part series, we are going to investigate the robustness of a static machine learning malware detection model trained with the EMBER dataset. For this purpose we will working with the Jigsaw ransomware.
The article discusses the very basics to keep systems ready for analysis of lateral movement. We present some guidelines in form of a cheat sheet and a tool (Readinizer) that you can run, to ensure that everything is set up as in the guidelines provided.
During internal assessments in Windows environments, we use BloodHound more and more to gather a comprehensive view of the permissions granted to the different Active Directory objects. In this post, we’ll show an advanced usage of this tool by using our additional queries.
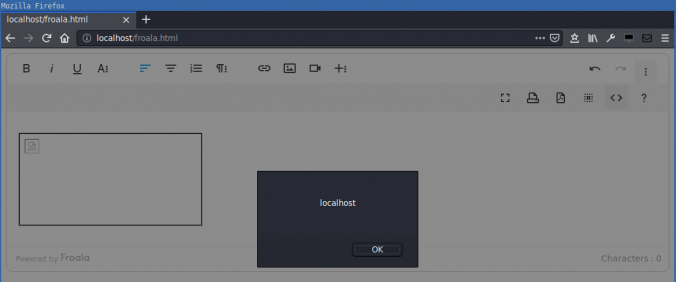
Compass found a DOM-based cross-site scripting (XSS) in the Froala WYSIWYG HTML Editor. HTML code in the editor is not correctly sanitized when inserted into the DOM. This allows an attacker that can control the editor content to execute arbitrary JavaScript in the context of the victim’s session.
Since a few years, we – as pentesters – (and probably bad guys as well) make use of NTLM relaying a lot for privilege escalation in Windows networks.
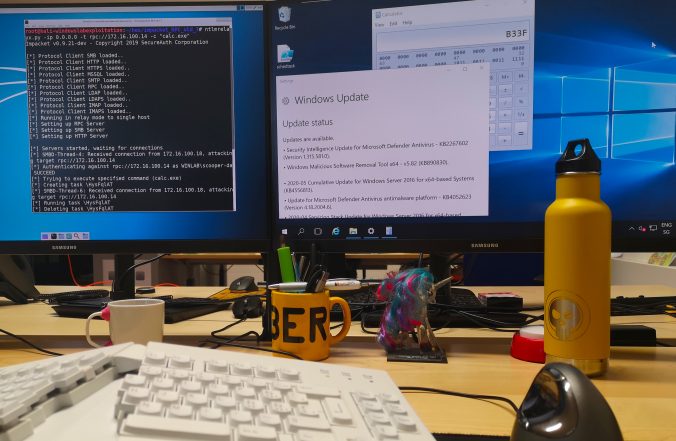
In this article, we propose adding support for the RPC protocol to the already great ntlmrelayx from impacket and explore the new ways of compromise that it offers.
This vulnerability was discovered by Compass Security in January 2020, disclosed to Microsoft Security Response Center and assigned CVE-2020-1113 as identifier.
In this blog post we will reverse engineer a sample which acts as downloader for malware (aka a “dropper”). It is not uncommon to find such a downloader during DFIR engagements so we decided to take a look at it. The sample that we are going to analyze has been obtained from abuse.ch and was […]
A new vulnerability (CVE-2020-0796) affecting SMBv3 has been discovered. The community has started to name this vulnerability SMBGhost because everyone knows this vulnerability is present but no additional details are available. Microsoft also released the advisory ADV200005. [1]
© 2025 Compass Security Blog