At Compass Security, we recently launched our managed bug bounty service. We openly invite hunters to probe our publicly exposed services for vulnerabilities. In return for their valuable feedback, we offer monetary bounties up to CHF 5000. This blog posts presents an interesting vulnerability found by a hunter on the bug bounty program of our subsidiary, Hacking-Lab.
Compass Security Blog
Offensive Defense
Page 5 of 29
Authentication and authorization are critical components of any application. Various standards and frameworks have been developed to facilitate the development of such components and make applications more secure. Among them, JSON Web Tokens (JWTs) have become popular choice over the years.
In this article, we discuss commons flaws in JWT-based authentication and present our extension to automatically check for these issues in Burp: JWT-scanner.
This is hopefully the most useless blog post you will read this year as this post will detail our experience dealing with ransomware cases. It is one of the most common reasons why we get called in to help and it has become a big business. Chainalysis, for example, has tracked $1.1 billion in ransomware […]
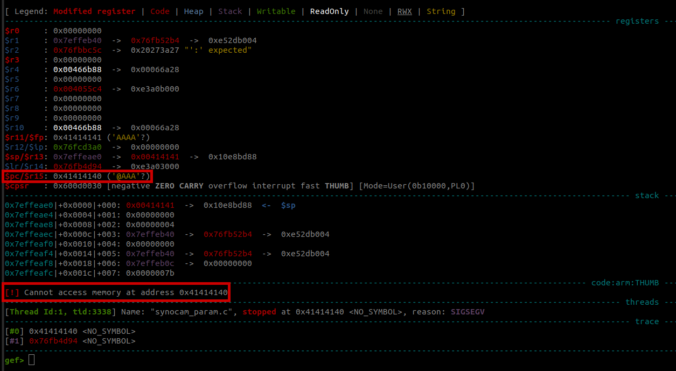
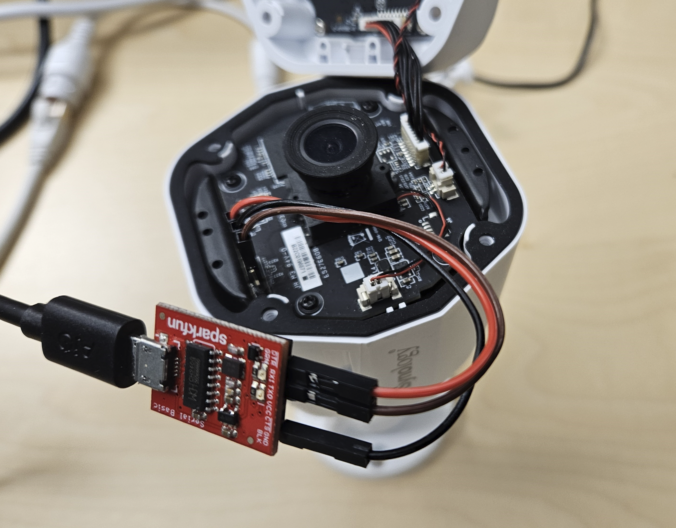
In this final part of this series, we are finally going to explain how the stack-based buffer overflow vulnerability can be exploited to gain unauthenticated remote code execution (RCE) on the Synology BC500 camera.
In this fourth part of the series, we analyze the memory corruption identified previously and manage to overwrite the program pointer!
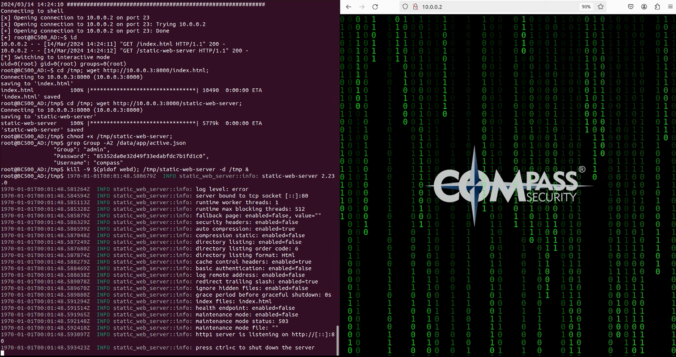
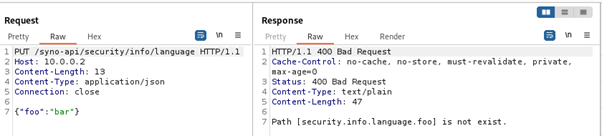
In this third part of the series, we focus on the exposed web services running on TCP ports 80 and 443.
Since a valid exploit chain must achieve code execution without prior authentication, we focus on the available functionality that can be accessed without authentication.
In this second blog post of the series, we start with the reconnaissance phase on the camera, a crucial step in understanding our target.
The aim here is to gather information about the target and identify potential vulnerabilities.
Around a year ago a few Compass analysts watched a talk at the Insomni’Hack conference about the Pwn2Own contest.
This is when they decided to take part! In this blog post, they talk about how they picked their target, got the firmware from the camera, and got into the shell.
What are LLMs LLMs (Large Language Models) are language models with a large number of parameters. These parameters are the model’s variables, which it learns during training. Typically, this training is unsupervised learning on a large data set, during which the algorithm tries to find patterns in the provided data. The more it learns, the […]
In today’s interconnected world, it is a well-known fact that systems with Internet exposure are under continual threat of cyber-attacks. This risk extends from private websites to corporate infrastructure. With the increasing modernization of Industrial Control Systems (ICS), these vital components also become more exposed to such threats. But what is the extent and nature […]
© 2026 Compass Security Blog