A write-up of the OWASP Toronto January talk which mainly focused on the correlation and integration of results generated by automated tools in application security such as SAST, DAST and SCA. Alexandre Larocque concludes whether old-fashioned PDF reports are still worth it.
Compass Security Blog
Offensive Defense
Page 4 of 7
As a defender, you want to find and patch attack paths in your Active Directory environment. One cannot easily spot issues by looking at the Active Directory Users and Computers console, GPOs, etc. but here comes BLOODHOUND.
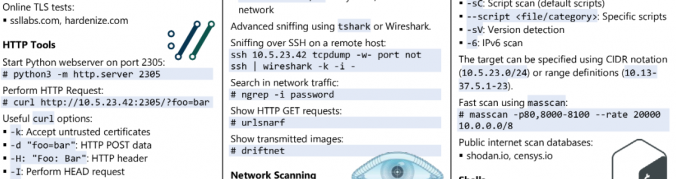
Everyone knows: cheat sheets are cool! They are very useful if you already know the basics about a topic but you have to look up details when you are not sure about something.
In this last article about privilege escalation in Windows domains, we demonstrate how to extract credentials from running systems to compromise high-privileged accounts.
This second article about privilege escalation in Windows domains describes how to propagate by aiming for passwords that are lying around.
This first article of our series about privilege escalation in Windows domains demonstrates how to get a foothold by relaying credentials from users.
This post is intended to explain what you typically want to check for during an OpenID Connect assessment and also provide you with a guide to setup your own OpenID Connect test environment.
Recently our analysts have been spending increasing amounts of time on IoT security. More specifically looking at the Tensilica Xtensa microcontroller architecture, and even more specifically at the Mongoose OS embedded operating system. With some public (CVE-2017-7185), and some not yet disclosed advisories (watch this space for Dobin Rutishauser’s work), we are happy to announce that […]
JSON Web Token, or more commonly known as JWT, is an open standard [1] that defines a compact and self-contained structure for securely transmitting information between multiple parties. The contained information can be verified and trusted through digital signatures. JWTs can be integrity protected using a secret using the HMAC algorithm or a public / private […]
SharePoint is a very popular browser-based collaboration and content management platform. Due to its high complexity, proprietary technology and confusing terminology it is often perceived as a black-box that IT and security professionals do not feel very comfortable with. These days, web security topics are well understood by many security professionals, penetration testers and vendors. But what […]
© 2026 Compass Security Blog