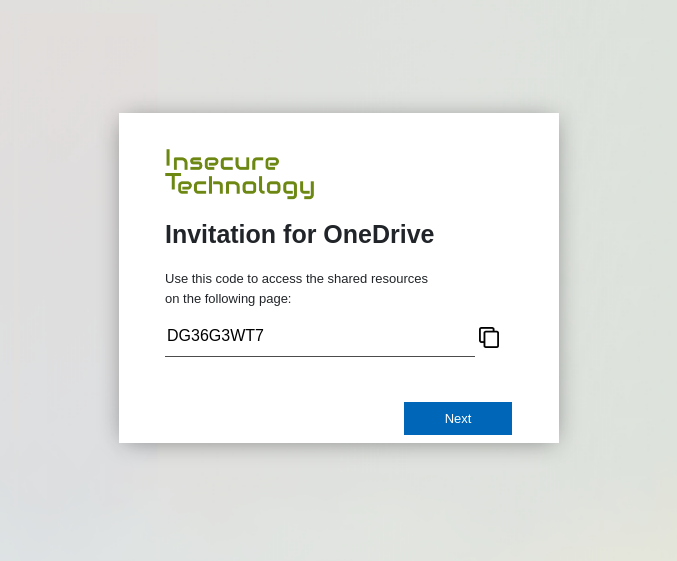
Device code phishing is nothing new. In fact it has been around for some years now. Despite the awesome capabilities of device code phishing, it is not widely used by threat actors. Therefore, it probably does not receive much attention from Microsoft. Compass Security is releasing two tools that can work hand in hand in a device code phishing exercise or even your next red team engagement.
Compass Security Blog
Offensive Defense
Page 2 of 3
A journey into the discovery of privilege escalation vulnerabilities in the Lenovo Update process.
Sometimes, the good old credential dumping techniques just won’t work. This is the story of how a bad actor could dump credentials on a fully-patched, monitored and hardened workstation.
Nowadays more and more security tools are used to monitor and generate alerts from different sources (EDR, Proxy, etc.).These alerts often contains URL, domain names, or file hashes that can and should be compared with a threat intelligence source to immediately identify current threats and avoid when possible false positives. In this article, we will […]
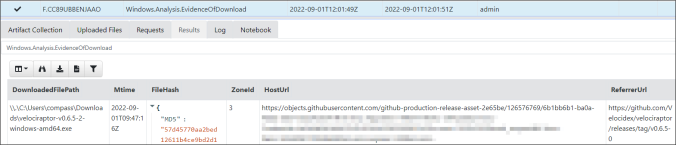
This post provides ideas of processes to follow and gives basic guidance on how to collect, triage and analyze artifacts using Velociraptor
BloodHound is the way to go to for finding attack paths in an Active Directory (AD) environment. However, it is not always clear how the data is gathered without looking at the code of SharpHound, the data ingestor for BloodHound. Microsoft hardened their systems over time through updates, which makes enumeration of Active Directory (AD) […]
BloodHound is the way to go to for finding attack paths in an Active Directory (AD) environment. However, it is not always clear how the data is gathered without looking at the code of SharpHound, the data ingestor for BloodHound. Microsoft hardened their systems over time through updates, which makes enumeration of Active Directory (AD) […]
BloodHound is the way to go to for finding attack paths in an Active Directory (AD) environment. However, it is not always clear how the data is gathered without looking at the code of SharpHound, the data ingestor for BloodHound. Microsoft hardened their systems over time through updates, which makes enumeration of Active Directory (AD) […]
Agile software development models have become the de-facto standard. They are taught at universities and implemented in practice as far as possible. Anyone who doesn’t develop software using agile processes is on the verge, and already tilting towards that. At least that is how it seems. Consequently, the question is not whether the integration of […]
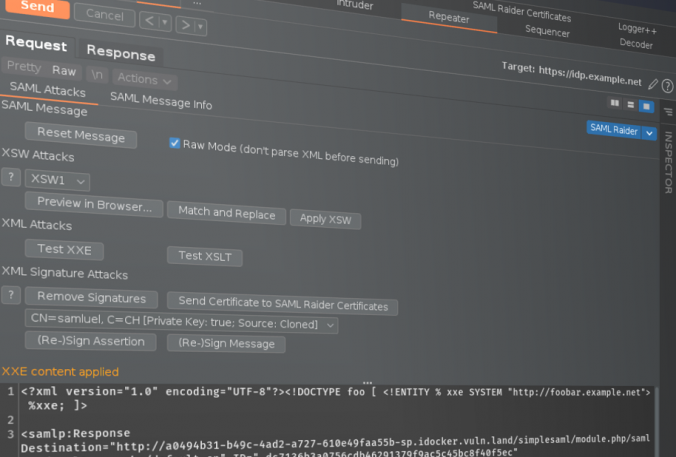
SAML Raider 1.4.0 is out which contains several new features like UI changes, new text editor, raw mode, XSW match/replace, parameter name definition and attack templates for XXE and XSLT attacks.
© 2026 Compass Security Blog